Git Lab researcher recently reported an issue that “iTerm2 Sending passwords in Plan Text to the ISP DNS Server’s and various things from the MacOS”
iTerm is used by 150,000-200,000 active users including all the version of iTerm releases so far including Nightly Build
What is iTerm2?
iTerm2 is a GPL-licensed terminal emulator for macOS. It was derived from and has mostly supplanted the earlier “iTerm” application.
iTerm2 supports operating system features such as window transparency, full-screen mode, Exposé Tabs, Growl notifications, and standard keyboard shortcuts. Other features include customizable profiles and Instant Replay of past terminal input/output. – As per Wiki
Who is using iTerm?
Who don’t like working in old Terminal fashion, people install iTerm for the ease of use in MacOS

What Features of iTerm makes people to use it
- Automatic Profile Switching
- Password Manager
- Badges
- Buried Sessions
- Captured Output
- Coprocesses
- Hotkeys
- Session Restoration
- Shell Integration
- Smart Selection
- tmux Integration
- Triggers
- Utilities
- Scripting
- Dynamic Profiles
- Inline Images Protocol
- Proprietary Escape Codes
Researcher quoted that simple three steps to recreate and identify the issue yourself
- Install iTerm
- Hover on things that remotely resemble URLs and touch Cmd
- Watch iTerm leak things in plain text over DNS
Researchers found this Backdoor implanted / Security Flaw [if the flaw is proved as not meant to sniff the users domain passwords – Still there is no confirmation from the developers of iTerm] flagged as an issue about the iTerm suspecting behaviors
2 Major issues has been registered so far and still research is going and based on the comments from other security researchers
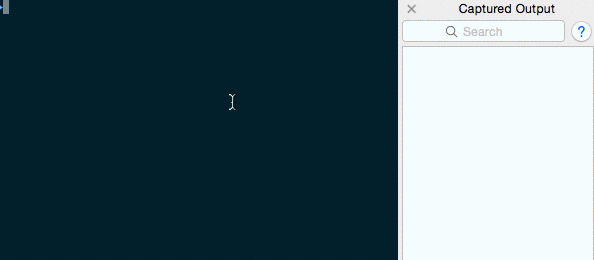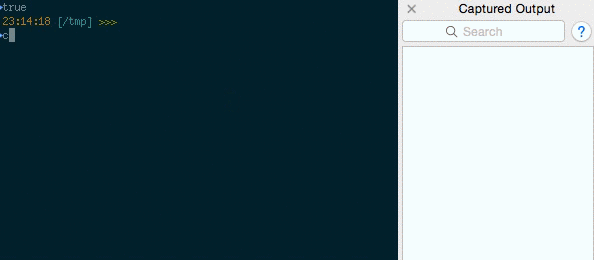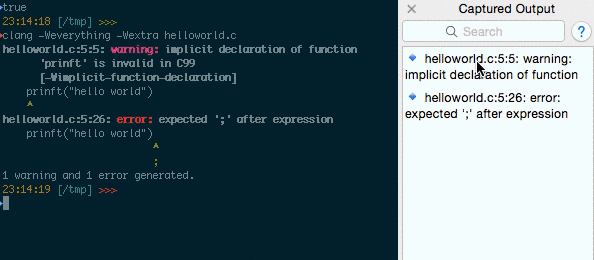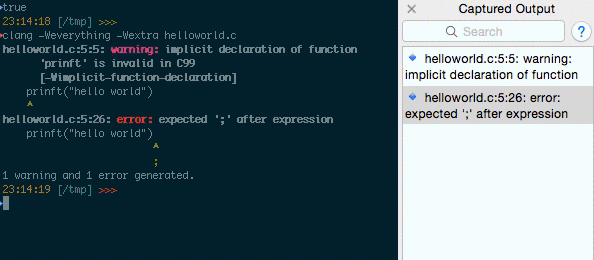
1. Smart Selection is issuing the DNS Requests – Issue 3688
Researcher Confirms “I use the openssl rand -base64 10 command to generate passwords. When I double click to select stdout, and hold the Cmd key to copy it to clipboard, a DNS query is issued for any string before a / character.”
2. Undesirable Domain lookup behaviour – Issue 5303
Turn on Preferences->Pointer-> ⌘-Click Opens Filename/URL (Semantic History)
launch an iterm window, type google.com
Holding ⌘ key, highlight google.com text.
What happened:
Once you hover over the url while holding ⌘ key, iterm issues a DNS query for that domain highlighted.
What should have happened:
Domains should not be queried through DNS to determine whether they are highlighted in iTerm. The current behavior can compromise a security analyst or incident responders investigation by querying a URL unintentionally while in iTerm. Often hackers/attackers monitor their attacking infrastructure for such investigators and these types of queries coming from a targets network.
Research Performed in:
- iTerm2 version: 3.0.15
- OS version: 10.12.6
Recommendation Given:
Already 200+ researcher’s surprised about the behaviors of the iTerm2 and most of them suggesting to Uninstall the iTerm2 from your MacOS
Recent implant in CCleaner and other software breaches confirming the GPL based product is always risky to install. We can see lot of Mature organizations taking the action which confirms the Corporate & IT Sectors still using the GPL based products. Not sure how the Audit team’s still not able to label the flaw of the organization.
People already lost the trust on GPL based products. Are we really require a new LAW to control the GPL software’s for the safety of the people??? Think Over Please













Leave A Comment