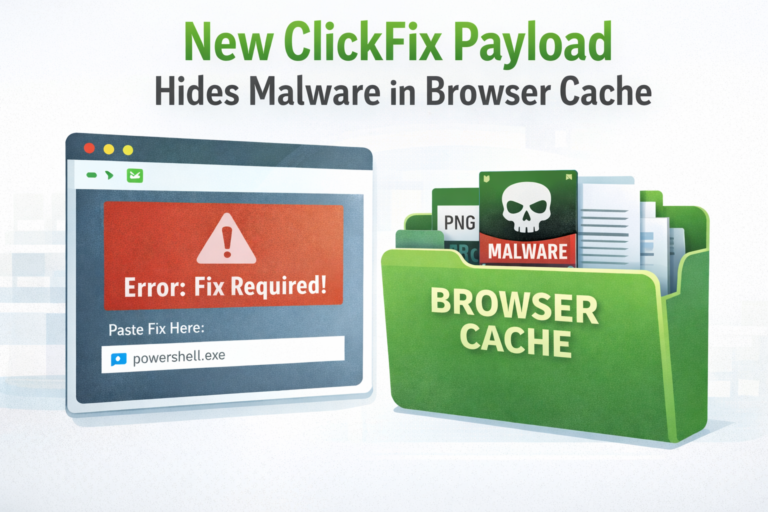
Cybersecurity researchers have uncovered a new version of the ‘ClickFix’ social engineering campaign. In this updated attack,...
The flaw, tracked as CVE-2026-22769, has a maximum CVSS score of 10.0 (Critical) and has been exploited...
Researchers from ETH Zurich have discovered 25 serious security vulnerabilities in three major cloud password managers: Bitwarden,...
Google has released an urgent Chrome update to fix a high-severity vulnerability that is actively being exploited....
A newly disclosed high-risk vulnerability, tracked as CVE-2026-1731, is impacting self-managed deployments of BeyondTrust Remote Support (RS)...