Security researchers have uncovered a coordinated malware campaign targeting people working in the cryptocurrency and Web3 industry....
A new phishing campaign is pretending to be LastPass support emails to trick users into revealing their...
Microsoft has discovered advanced phishing campaigns that misuse the normal behavior of the OAuth 2.0 authentication process....
Google Chrome’s security team has announced a new plan to protect HTTPS from future quantum computer attacks....
A serious security issue has been found in the MS-Agent framework. The flaw, tracked as CVE-2026-2256, allows...
GTFire is a newly identified phishing campaign that misuses trusted Google services, including Firebase and Google Translate,...
On March 2, 2026, Anthropic’s AI assistant Claude experienced a major global outage that disrupted users and...
A critical security flaw (CVE-2026-27728) has been identified in OneUptime, a service monitoring platform. The issue allows...
Hackers are actively mapping SonicWall firewalls worldwide. In just four days, over 84,000 SonicOS scanning sessions were...
OpenClaw, a popular open-source AI assistant with over 100,000 GitHub stars, recently fixed a serious security flaw...
The ongoing Middle East conflict has significantly elevated cyber risk across the region. During periods of geopolitical...
A new scam is targeting Zoom users by exploiting trust in meeting invitations. In just twelve days,...
A hacker reportedly manipulated Anthropic’s Claude AI to assist in a coordinated cyberattack against Mexican government agencies,...
Microsoft says attackers are creating fake Next.js projects to trick developers. These projects look normal and often...
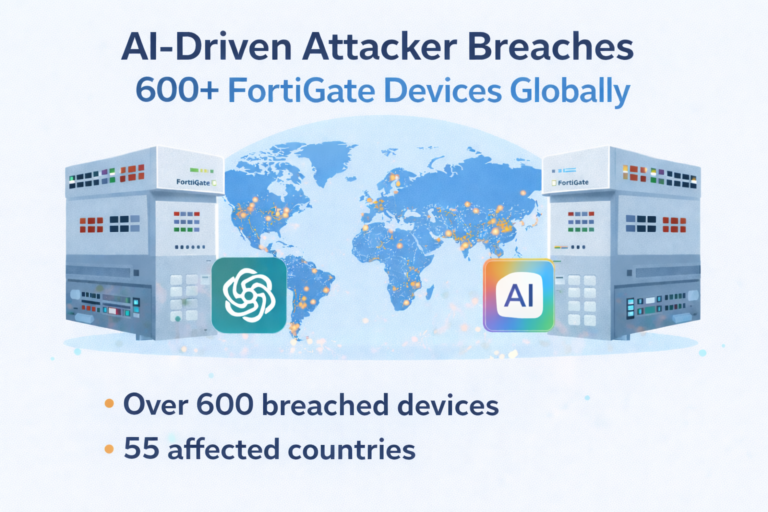
A financially motivated threat actor used commercial generative AI tools to compromise more than 600 FortiGate devices...
ZeroDayRAT is a newly discovered mobile spyware service that targets both Android and iOS devices. Unlike traditional...
Google says it stopped more than 1.75 million malicious or policy-violating Android apps from reaching users in...
Software Error in Business Loan Application PayPal has notified a small group of customers about a cybersecurity...
Three Vulnerabilities Could Allow Remote Code Execution Google has released an urgent Chrome security update fixing three...
PromptSpy is a newly discovered Android malware family that uses Google’s Gemini AI model to make real-time...
A security weakness in Microsoft 365 Copilot is allowing the AI assistant to generate summaries of emails...
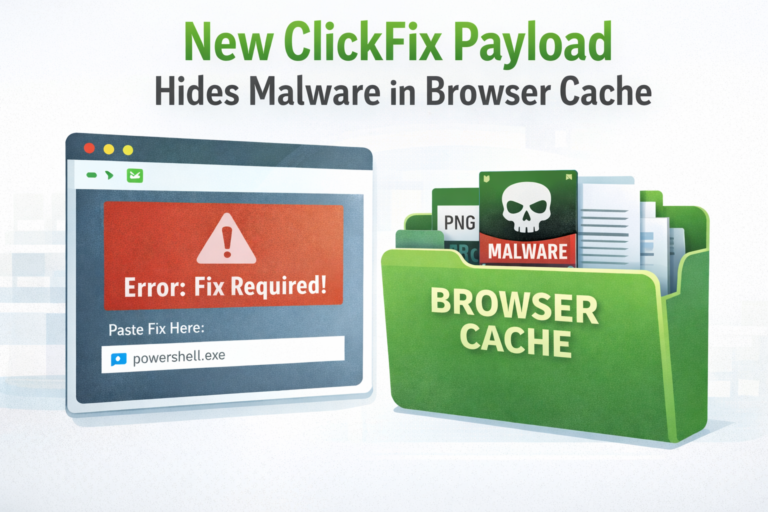
Cybersecurity researchers have uncovered a new version of the ‘ClickFix’ social engineering campaign. In this updated attack,...
The flaw, tracked as CVE-2026-22769, has a maximum CVSS score of 10.0 (Critical) and has been exploited...
Researchers from ETH Zurich have discovered 25 serious security vulnerabilities in three major cloud password managers: Bitwarden,...
Google has released an urgent Chrome update to fix a high-severity vulnerability that is actively being exploited....
A newly disclosed high-risk vulnerability, tracked as CVE-2026-1731, is impacting self-managed deployments of BeyondTrust Remote Support (RS)...
CISA has raised concerns about a serious security issue affecting Notepad++, one of the most widely used...
A recent investigation uncovered 287 Chrome extensions that may be quietly collecting users’ browsing data and transmitting...
Threat actors are evolving — and they’re doing it on trusted platforms. A recent campaign shows attackers...
Microsoft 365 administrators across North America are experiencing significant access issues with the Microsoft 365 admin center,...
Cybercriminals are running a sneaky operation that uses a fake version of the popular 7-Zip archiving tool...
A new security advisory from Fortinet highlights a serious weakness in FortiOS that could let attackers slip...
Security researchers at LayerX uncovered a design-level weakness affecting Claude Desktop Extensions (DXT), the extension framework tied...
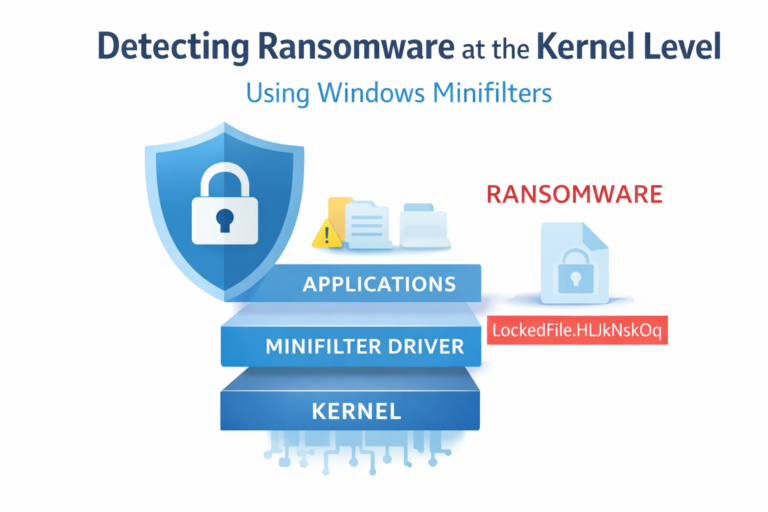
A security researcher has published a proof-of-concept tool on GitHub aimed at stopping ransomware from inside the...
A widespread web server misconfiguration issue has quietly exposed millions of websites to potential data theft and...
A new and well-planned phishing campaign is targeting users of Apple’s payment ecosystem. The attackers are not...
Recent research from Google’s Threat Intelligence Group reveals that adversaries are now building malware that actively leverages artificial intelligence (AI) during...
F5 has released its latest security update, fixing several vulnerabilities across its products. Although F5 lists some...
TP-Link has disclosed multiple serious security flaws in its Archer BE230 v1.2 Wi-Fi router. These vulnerabilities allow...
A large, organized scanning campaign has been observed targeting Citrix NetScaler (ADC) Gateway systems across the internet....
A malware framework called PeckBirdy has been active since 2023, using built-in system tools (LOLBins) to quietly...
Microsoft has issued KB5074105, an important preview update for Windows 11 versions 24H2 and 25H2, aimed at...
A newly observed Linux threat called ShadowHS is showing how modern attackers are moving beyond traditional malware....
A fast-growing open-source personal AI project has unintentionally created a major security concern after more than 21,000...
The latest Metasploit Framework update brings several new modules that help security teams test real-world attack paths....
A serious security warning has been issued for several Johnson Controls industrial control products due to a...
Researchers at NeuralTrust uncovered a new AI weakness called Semantic Chaining. It affects multimodal systems like Grok...
A year-long study tracking 550 hacked e-commerce sites across 68 countries shows that removing a skimmer once...
MITRE has just unveiled a dedicated cybersecurity framework — the Embedded Systems Threat Matrix™ (ESTM) — to...
A working proof-of-concept exploit has been made public for CVE-2026-24061, a critical remote code execution vulnerability affecting...
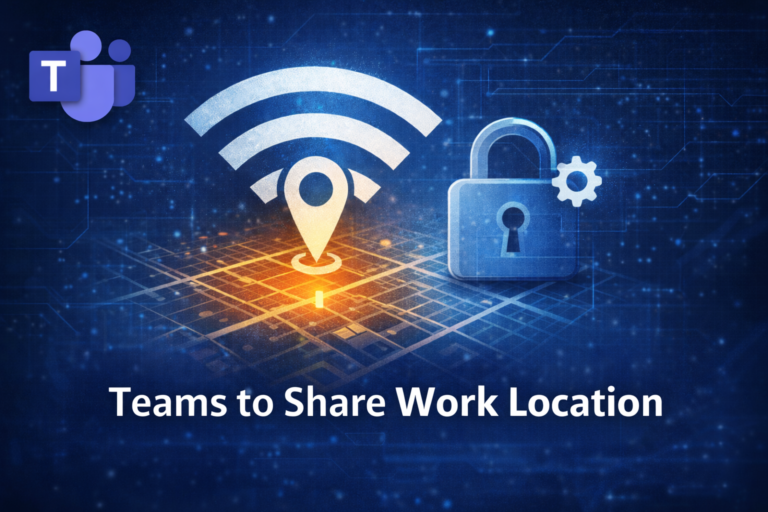
Microsoft is preparing to introduce a new Teams feature that can automatically show where employees are working...
Microsoft investigates startup and stability issues affecting recent Windows 11 versions Microsoft is investigating serious problems linked...
A recently identified ransomware strain named Osiris was linked to an intrusion at a large food services...
The OWASP ZAP project has introduced a new add-on that brings the OWASP Penetration Testing Kit (PTK)...
A newly reported high-impact security flaw in BIND 9, one of the most widely deployed DNS server...
Cisco has issued an urgent security alert after identifying a previously unknown remote code execution flaw being...
Multiple vulnerabilities in Apache Airflow versions prior to 3.1.6 could lead to the exposure of sensitive credentials...
A critical security vulnerability has been identified in the Advanced Custom Fields: Extended WordPress plugin, exposing more...
The Everest ransomware group is claiming a significant breach involving McDonald’s India, alleging that hundreds of gigabytes...
VoidLink has emerged as a serious threat to Linux-based cloud infrastructure, marking a clear shift in how...
Default Service Agent Permissions Expose High-Risk Identity Paths Security researchers have uncovered critical privilege escalation vulnerabilities in...
Google has confirmed an Android bug that affects how volume buttons behave when the Select to Speak...
Microsoft has addressed a security weakness in Windows Remote Assistance that could allow attackers to bypass built-in...
A newly disclosed critical vulnerability in Cal.com, an open-source scheduling and booking platform, could allow attackers to...
Security researchers have released a detailed technical analysis of the DragonForce ransomware, along with confirmation that working...
Palo Alto Networks has released security updates to fix a denial-of-service (DoS) vulnerability in its PAN-OS firewall...
Elastic has released new security updates to fix multiple vulnerabilities across its platform, including a high-severity issue...
A serious security issue has been identified in the ServiceNow AI Platform, exposing organizations to the risk...
SAP has released its January 2026 Security Patch Day updates, publishing 17 new security notes on January...
Instagram has confirmed that its platform was not compromised after a wave of unexpected password reset emails...
Recent research has shed light on how underground carding markets operate online. Investigators identified 28 active IP...
The React2Shell vulnerability (CVE-2025-55182) continues to be heavily targeted, with attackers launching more than 8.1 million attack...
LockBit 5.0 has appeared as the newest version of one of the most active ransomware groups in...
More than 900,000 Chrome users were impacted by two harmful browser extensions that quietly collected AI chat...
Google has released an urgent security update for the Chrome browser to fix a high-severity vulnerability that...
Several large organizations worldwide have been breached after attackers reused stolen login details collected by infostealer malware....
Eaton has released a security advisory after identifying multiple vulnerabilities in its UPS Companion (EUC) software. If...
In December 2025, a phishing campaign hit over 3,000 organizations, mostly in manufacturing. The attackers used Google’s...
A newly disclosed vulnerability in Apache NuttX RTOS could allow attackers to crash systems or trigger unexpected...
Cybercrime activity is increasingly shaped by automation and repeatable services. Researchers at Hudson Rock have identified ErrTraffic...
GlassWorm has returned with a dangerous new evolution, shifting its focus entirely to macOS. First discovered in...
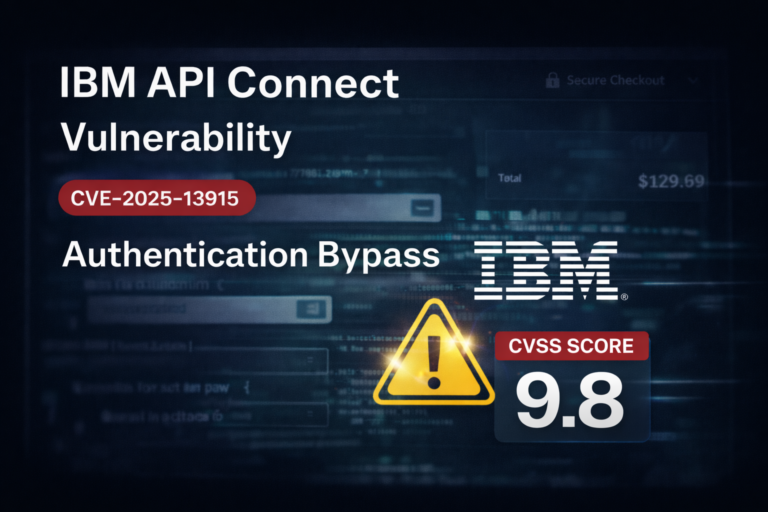
IBM has disclosed a critical security flaw in its API Connect platform that allows attackers to bypass...
A newly uncovered Magecart operation shows how web-based attacks on online stores are becoming more advanced. Magecart...
CISA has flagged a serious security issue affecting MongoDB Server and confirmed that it is being actively...
Since March 2025, attackers running a Spanish-language phishing campaign have been going after Microsoft Outlook accounts. The...
Windows privilege escalation remains a common technique used by attackers to gain deeper control of a system....
A massive data leak linked to WIRED has surfaced online, exposing personal information tied to more than...
A security issue in the Trust Wallet Chrome extension led to losses of more than $7 million....
For a long time, Gmail users had only one option if they wanted a new email address:...
Microsoft is making Microsoft Teams safer by default. Beginning January 12, 2026, the platform will automatically apply...
Threat actors are using a new attack method that combines ClickFix social engineering with image steganography to...
A malicious npm package called “lotusbail” has been secretly stealing WhatsApp messages and user data from developers...
A major data breach at Marquis has compromised the personal information of hundreds of thousands of bank...
GitHub has officially introduced Claude Opus 4.5, Anthropic’s latest flagship AI model, into its Copilot platform. With...
An active zero-day exploit in Cisco AsyncOS is being used to target Secure Email Gateway and Secure...
Operation ForumTrol has launched a new phishing campaign aimed at Russian political scientists and academic researchers. The...
CISA has issued an urgent alert about a critical zero-day vulnerability in Apple WebKit that is being...
Microsoft has released security guidance to address a critical vulnerability called React2Shell (CVE-2025-55182). The issue affects applications...
Frogblight is a sophisticated Android banking Trojan mainly targeting users in Turkey by pretending to be official...
JSCEAL is a new threat targeting Windows users, mainly people using cryptocurrency apps or accounts with sensitive...
ReversingLabs has uncovered a supply-chain attack involving 19 malicious VS Code extensions.Active since February 2025, the campaign...
DomainTools Investigations has uncovered a rapidly growing malware network aimed at Chinese-speaking users around the world. The...
The cybersecurity landscape is at a worrying point. On December 5, 2025, Huntress discovered a smart attack...
A new vishing attack uses social engineering and legitimate Microsoft tools to run commands and deploy multi-stage...
Adex, an anti-fraud platform under AdTech Holding, has uncovered and shut down a long-running malware scheme tied...
India is weighing a new rule that would force all smartphones to keep GPS-based location tracking active...
Security teams around the world are rushing to fix systems after a major React vulnerability was revealed:...
A critical command injection vulnerability in Array Networks’ ArrayOS AG systems is being actively exploited, with confirmed...
Three major cyber agencies — CISA, NSA, and the Canadian Cyber Centre — have issued a new...
A new phishing campaign has been uncovered using fake Calendly pages to steal credentials from Google Workspace...
Google has released Chrome 143 to the Stable channel, with version 143.0.7499.40 now available for Linux and...
A newly disclosed security flaw in Apache Struts could let attackers trigger disk exhaustion attacks, potentially making...
Users of the new Outlook for Windows are facing a problem where Excel attachments won’t open if...
A fake VS Code extension pretending to be the Material Icon Theme was found targeting Windows and...
A Proof‑of‑Concept exploit has been released for a critical remote code execution vulnerability in Microsoft Outlook, tracked...
Albiriox is a new Android malware that recently appeared on cybercrime forums. It offers advanced remote-access features...
GitLab has released important security updates for both its Community Edition (CE) and Enterprise Edition (EE) to...
Hidden vulnerabilities in old Python code can create serious risks for today’s development environments. A recent example...
A gap in Microsoft Teams’ B2B guest access allows attackers to bypass Defender for Office 365 protections,...
A threat actor calling themselves ResearcherX has claimed to sell a full-chain zero-day exploit for Apple’s new...
Security researchers at Socket discovered a deceptive Chrome extension called Crypto Copilot. It pretends to be a...
The Tor Project has introduced a major upgrade to its cryptographic system, replacing its long-standing relay encryption...
A proof-of-concept (PoC) exploit has been released for CVE-2025-9501, a critical command-injection vulnerability in W3 Total Cache,...
A new malware campaign is actively targeting users in Brazil, using WhatsApp as the primary channel to...
Salesforce has disclosed a significant security incident involving unauthorized access to customer data through compromised OAuth tokens...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a newly identified Oracle vulnerability to its...
A new command-and-control system called Matrix Push C2 has become a major threat to users on all...
A serious remote code execution flaw in Microsoft’s Windows Graphics Component allows attackers to take control of...
Microsoft has launched an investigation into a widespread issue affecting Microsoft Copilot in Microsoft 365, where users...
A new and rapidly growing scam is targeting WhatsApp users worldwide, exploiting the platform’s screen-sharing feature introduced...
Cloudflare released a detailed report explaining the cause of a major network outage that disrupted global internet...
Cisco has revealed serious security vulnerabilities in Cisco Unified Contact Center Express (Unified CCX). These issues allow...
Cisco has released a warning about a newly discovered high-severity vulnerability (CVE-2025-20341) affecting the Cisco Catalyst Center...
Fortinet has released an urgent security update for a critical vulnerability in FortiWeb Web Application Firewall (WAF)....
On November 7, Veracode researchers found a dangerous typosquatting attack targeting developers who use GitHub Actions. A...
A new vulnerability has been discovered in Lite XL, a lightweight open-source text editor, that could let...
A new phishing scam is targeting iPhone users who have lost their devices, taking advantage of their...
A newly discovered malware campaign is leveraging one of cybercriminals’ most effective lures cryptocurrency to distribute DarkComet...
Microsoft has released its November 2025 Patch Tuesday update, fixing 63 security vulnerabilities across its products. One...
Ivanti has released an urgent security update for Ivanti Endpoint Manager, addressing a newly discovered high-severity flaw...
Cybercriminals are now hacking websites to insert malicious links that help boost their own search engine rankings....
QNAP has released an urgent security update after security researchers at Pwn2Own Ireland 2025 successfully hacked QNAP...
Cybersecurity teams are under constant pressure to find vulnerabilities before attackers do. Traditional penetration testing takes time,...
Google has uncovered a new form of AI-assisted malware that uses its own Gemini large language model...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two new security flaws affecting Gladinet and...
Cybersecurity researchers have revealed four critical vulnerabilities in Microsoft Teams that could have allowed attackers to impersonate...
Researchers have discovered a new wave of attacks using the Lampion banking trojan, a malware active since...
WhatsApp has rolled out passkey-encrypted backups, a major upgrade that makes protecting chat history easier and more...
On October 29, 2025, CISA released new guidance to help organizations detect and reduce attacks exploiting CVE-2025-59287,...
Cybercriminals are using a new phishing technique that hides invisible characters in email subject lines to bypass...
A sophisticated Android banking trojan called Herodotus has appeared, using new techniques to evade detection. All about...
A new security flaw has been discovered in the recently released OpenAI Atlas browser. The issue was...
A new analysis by Wordfence security researchers has revealed a recurring malware strain that uses PHP’s variable...
Cybersecurity researchers have uncovered a sophisticated cybercriminal operation dubbed “Jingle Thief,” which has been targeting cloud environments...
E-commerce security experts at Sansec have issued a warning about active exploitation targeting a newly disclosed Adobe...
A new cyber espionage campaign has been launched by an Iranian state-sponsored hacking group known as MuddyWater,...
Record-Breaking Day for Security Researchers Day One of Pwn2Own Ireland 2025 concluded with an extraordinary showcase of...
A critical security flaw in Oracle E-Business Suite (EBS) is being actively exploited by the Cl0p ransomware...
The Akira ransomware gang is now reportedly bypassing multi-factor authentication (MFA) protections on SonicWall VPN devices, according...
Attackers Exploiting VPN and Web Services to Gain Root Access — CISA Issues Emergency Directive Two critical...
In a series of escalating cyber threats, two distinct hacking groups— the newly identified ComicForm and the...
A large-scale cyberattack has been uncovered. The attack was enabled by DNS misconfigurations across global networks. Over...
Google has issued an emergency security update for its Chrome browser following the discovery of a critical...
A newly identified ransomware group known as The Gentlemen has been targeting enterprises across 17 countries since...
Threat hunters recently found 45 secret domains linked to Salt Typhoon, a China-backed hacking group. These domains,...
Cybercriminals are misusing iCloud Calendar to send phishing emails from Apple’s servers. These fake emails look like...
In a shocking cybersecurity incident that highlights the growing threats to global financial systems, hackers recently targeted...
In a major cybersecurity incident shaking the tech world, Zscaler, a leading cloud security provider, has confirmed...
Every organization – whether it’s a global enterprise with thousands of employees or an individual tech enthusiast...
In recent months, security researchers have identified a new phishing campaign aimed at macOS users, disguised as...
A new set of 60 malicious packages targeting the RubyGems ecosystem has been discovered. These packages masquerade...
Cybersecurity researchers have identified 11 malicious Go packages engineered to download and execute additional payloads from remote...
Mozilla has issued an urgent security alert to its developer community after identifying a sophisticated phishing campaign...
A sophisticated attack technique has emerged in which cybercriminals exploit free trials of Endpoint Detection and Response...
On Tuesday, Apple rolled out security updates for its entire software lineup, addressing a vulnerability that Google...
Choicejacking is a new USB attack that tricks phones into sharing data at public charging stations, bypassing...
In the latest example of a software supply chain attack, unidentified threat actors breached Toptal’s GitHub organization...
A significant cybersecurity breach has compromised the privacy of users accessing one of the internet’s most infamous...
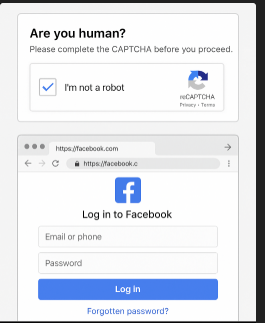
A fast-growing phishing campaign is leveraging a Browser-in-the-Browser (BitB) overlay to mimic Facebook’s login page and steal...
A highly sophisticated WordPress malware campaign has been uncovered, exploiting the seldom-monitored mu-plugins (must-use plugins) directory to...
Google has unveiled a new initiative called OSS Rebuild, aimed at strengthening the security of open-source package...
“A New DCHSpy Variant Unveiled: Iranian Cyber Group MuddyWater Targets Mobile Data Amid Rising Israel-Iran Tensions” This...
On July 19, 2025, CoinDCX, India’s second-largest cryptocurrency exchange, confirmed a sophisticated security breach that led to...
On July 17, 2025, CISA released three important advisories concerning Industrial Control Systems (ICS), targeting critical vulnerabilities...
Google’s cutting-edge AI-driven security tool, Big Sleep, has reached a major milestone by identifying and halting the...
A sophisticated new credential stealer has surfaced on GitHub, masquerading as a legitimate forensic toolkit while targeting...
A new wave of phishing emails is circulating globally, posing as offers for a “Social Media Manager”...
Security researchers have identified a critical vulnerability in Google Gemini for Workspace that allows attackers to insert...
A critical security flaw in Microsoft Remote Desktop Client, identified as CVE-2025-48817, could enable attackers to execute...
A new wave of cyberattacks is actively compromising WordPress websites through the use of malicious SEO plugins...
Cybersecurity researchers have uncovered two security vulnerabilities in the Sudo command-line utility used in Linux and Unix-like...
CrowdStrike Services has observed SCATTERED SPIDER escalating its attacks across multiple industries


CrowdStrike Services has observed SCATTERED SPIDER escalating its attacks across multiple industries
CrowdStrike Services outlines the techniques used by SCATTERED SPIDER in attacks targeting the aviation, insurance, and retail...
A critical security flaw in Anthropic’s Model Context Protocol (MCP) Inspector tool, identified as CVE-2025-49596, has raised...
Pro-Iranian Hacktivist Group Leaks Sensitive Data from Major Sporting Event In a significant cyber incident that underscores...
Microsoft has unveiled plans to extend security updates for Windows 10 until October 13, 2026, offering critical...
In a decisive move highlighting growing concerns over digital privacy and cybersecurity, the United States House of...
In a shocking cryptocurrency security breach, CoinMarketCap, the leading crypto price tracking platform, fell victim to a...
Newly discovered Linux vulnerabilities, identified as CVE-2025-6018, CVE-2025-6019, and CVE-2025-6020, threaten major distributions like Ubuntu, Debian, Fedora,...
Zoomcar, India’s prominent car-sharing platform, has disclosed a significant data breach affecting approximately 8.4 million of its...
FTC Cracks Down on Payment Processor’s Role in Deceptive Schemes On June 16, 2025, the Federal Trade...
Scattered Spider Threat Looms Over Insurance Industry Google’s Threat Intelligence Group has identified multiple cybersecurity breaches in...
What is the Coinbase Data Breach All About? In June 2025, global crypto exchange Coinbase disclosed a...
A newly discovered security vulnerability, identified as CVE-2025-46701, has been found in Apache Tomcat’s CGI servlet implementation....
Netskope Threat Labs has uncovered a stealthy malware campaign delivering the PureHVNC Remote Access Trojan (RAT), using...
Between April and May 2025, threat actors launched a multi-wave phishing campaign by exploiting the trusted infrastructure...
On May 8, 2025, cybersecurity analysts at GreyNoise identified a large-scale and tightly coordinated scanning campaign that...
A critical vulnerability (CVE-2025-4009) was found in Evertz’s Software Defined Video Network (SDVN) products, allowing attackers to...
At this year’s Pwn2Own Berlin, researchers revealed two new zero-day flaws in Mozilla Firefox, targeting its content...
DocuSign is trusted by over 1.6 million customers, including 95% of Fortune 500 companies, and has more...
A serious security issue has been discovered in the TI WooCommerce Wishlist plugin, which is used on...
Linux 6.15, released on May 25, 2025, brings major updates to the open-source world with new features...
A new phishing scam is targeting Indian air travelers by pretending to be the trusted DigiYatra service....
OpenAI has upgraded ChatGPT with powerful deep research features, now supporting direct integration with cloud platforms like...
Cisco has patched a security flaw (CVE-2025-20255) in its Webex Meetings service that could let attackers manipulate...
PowerDNS has released an important security update to fix a high-risk vulnerability in DNSdist, its DNS proxy...
Microsoft is rolling out a major security upgrade in Windows 11 called Administrator Protection, aimed at stopping...
On May 13, 2025, a sophisticated supply chain attack compromised the trusted VMware administration tool RVTools, turning...
Cybersecurity researchers have discovered a sophisticated malware campaign that leverages AutoIT, a scripting language known for its...
A critical vulnerability has been found in the Auth0-PHP SDK that could let attackers bypass authentication by...
Researchers have found a way to bypass Kernel Address Space Layout Randomization (KASLR) on fully updated Windows...
A new phishing campaign is tricking users with fake Zoom meeting invites that appear to come from...
Xerox has rolled out its April 2025 security update for the FreeFlow Print Server v2 (Windows 10),...
Adobe has released an urgent security update for Illustrator after discovering a critical vulnerability (CVE-2025-30330) that affects...
A critical vulnerability, CVE-2025-31644, has been discovered in F5 BIG-IP systems running in Appliance mode. The flaw...
A new macOS vulnerability, CVE-2025-31258, has been disclosed by security researcher wh1te4ever, along with a proof-of-concept (PoC)...
Broadcom-owned VMware has released security updates to fix a moderate-severity vulnerability (CVE-2025-22247) in VMware Tools, which has...
The IPFire team has officially released IPFire 2.29 – Core Update 194, bringing a host of security...
Cofense Intelligence researchers have uncovered a phishing method that uses Blob URIs to sneak fake login pages...
Cybersecurity experts at Palo Alto Networks’ Unit 42 have discovered a new method attackers use to hide...
Cybercriminals are increasingly pretending to be IT staff or trusted authorities to trick employees into giving them...
Cisco has issued critical security updates to address a vulnerability in its Switch Integrated Security Features (SISF),...
The Agenda ransomware group (Qilin) ramped up attacks in early 2025, hitting key sectors worldwide with tools...
Researchers at ANY.RUN have discovered a complex attack using the Diamorphine rootkit to install a crypto miner...
In a targeted cyber espionage campaign, attackers are using fake documents referencing the recent Pahalgam attack to...
Cybersecurity firm Sansec has exposed a sophisticated supply chain attack that compromised 21 popular e-commerce applications, giving...
A serious security flaw has been discovered in Apache ActiveMQ’s .NET Message Service (NMS) library. This vulnerability,...
Quantum computing is moving from theory to reality—and with it comes a serious challenge for today’s encryption...
A serious security flaw in Tesla’s Model 3 was revealed during the 2025 Pwn2Own hacking competition. The...
Commvault, a global company known for data protection and information management, has confirmed a cyberattack on its...
Security researchers have found three serious flaws in the Netgear EX6200 Wi-Fi extender that let hackers access...
In today’s cyber threat landscape, who the Chief Information Security Officer (CISO) reports to is more than...
Cybercriminals have used the Nitrogen ransomware campaign to target victims through fake online ads. Nitrogen Ransomware They...
A serious security flaw, CVE-2025-2783, has been found in Google Chrome, affecting the Mojo inter-process communication (IPC)...
A multi-stage carding attack targeted a Magento eCommerce site running outdated version 1.9.2.4, unsupported since June 2020....
A significant data leak involving Microsoft Defender XDR exposed over 1,700 sensitive documents from many organizations, triggered...
Researchers discovered two critical UAF vulnerabilities in Chrome, actively exploited in the wild, but Google’s MiraclePtr defense...
Threat actors have exploited a zero-day flaw in Ivanti Connect Secure (CVE-2025-0282) to install a web shell...
A major remote code execution (RCE) vulnerability, CVE-2025-34028, has been discovered in Commvault’s on-premise backup and recovery...
NFC Technology Abused in Global ATM and POS Fraud Cybercriminals, mainly from Chinese underground networks, are using...
Cybersecurity researchers have found critical SQL injection vulnerabilities in four TP-Link router models, which could allow attackers...
The Socket Threat Research Team has discovered three malicious open-source packages—two on PyPI and one on npm—designed...
Hackers have been using Cloudflare tunnels since February 2024 to host malware and spread remote access trojans...
A recent report from IBM X-Force reveals that infostealer malware delivered through phishing emails has spiked by...
Cybersecurity researchers recently uncovered a server linked to the KeyPlug malware, used by the threat group RedGolf...
A major security flaw (CVE-2024-13059) was found in the open-source AI tool AnythingLLM. Discovered in February 2025,...
Attackers are now using server-side phishing to target employee and member login portals, making it harder to...
Apple has released iOS 18.4.1 and iPadOS 18.4.1 to fix two zero-day vulnerabilities that were actively exploited...
Google has released an urgent security update for its Chrome browser after two critical vulnerabilities were found,...
As companies shift to zero-trust security models, security awareness has become a key line of defense. CISOs...
Many Microsoft Teams users around the world are currently facing issues with file sharing due to an...
VMware has announced the release of ESXi 8.0 Update 3e, the latest version of its industry-leading hypervisor....
Cisco Talos researchers have found a major smishing campaign targeting U.S. toll road users. Active since October...
A new wave of cyber espionage has highlighted BPFDoor, a stealthy malware used to secretly access and...
A new remote access trojan (RAT) called ResolverRAT is posing a serious threat to businesses around the...
Microsoft has added a major security upgrade to Exchange Server and SharePoint Server by integrating them with...
Dell Technologies has released a critical alert about serious flaws in PowerScale OneFS that could let attackers...
AhnLab Security Intelligence Center (ASEC) discovered a cyber attack targeting Korean users with ViperSoftX malware. ViperSoftX Malware...
Cybersecurity experts have found a new phishing attack that steals Office 365 credentials and installs malware, putting...
Microsoft has released an urgent patch for a serious security flaw—CVE-2025-29810—affecting Windows Active Directory Domain Services (AD...
More than 5,000 Ivanti Connect Secure devices remain exposed to a high-risk remote code execution (RCE) vulnerability,...
CISA has issued a warning about a critical vulnerability (CVE-2025-31161) in CrushFTP that is being actively exploited....
North Korea’s Lazarus Group has ramped up its Contagious Interview campaign by using new npm packages with...
A new cyber threat called Neptune RAT is raising concerns among Windows users, as it targets sensitive...
A new Android spyware app uses a password prompt to prevent uninstallation, making it difficult for users...
Oracle confirmed a data breach affecting its older Gen 1 servers, its second incident in weeks, highlighting...
A ransomware attack targeted MSPs via phishing emails, deploying Qilin ransomware across customer environments. Ransomware Attack Targets...
Kaspersky Lab has discovered a new version of the Triada Trojan targeting Android devices. This variant is...
Cisco has revealed a critical flaw (CVE-2025-20212) in its AnyConnect VPN Server for Meraki MX and Z...
Symantec has discovered a sophisticated phishing campaign targeting Monex Securities (マネックス証券), a leading online securities firm in...
A massive 400GB dataset with info from 2.87 billion X (formerly Twitter) users has appeared on hacker...
With the U.S. tax deadline nearing, scammers are ramping up IRS-themed attacks. McAfee Labs reports a rise...
A newly disclosed flaw in HPE’s Insight CMU v8.2, CVE-2024-13804, allows attackers to bypass authentication and execute...
Recent cyberattacks by the APT group Earth Alux have exposed the use of advanced malware, including the...
Cybersecurity analysts have identified a campaign using a fake Zoom installer to spread BlackSuit ransomware on Windows...
Microsoft Introduces “Quick Machine Recovery” to Simplify Boot Issue Fixes Microsoft has introduced Quick Machine Recovery, a...
Mozilla has released an urgent update for Firefox on Windows to fix a critical vulnerability. This follows...
The Tor Project has quickly released an emergency update, Tor Browser 14.0.8, available only for Windows users....
Researchers from Qatar Computing Research Institute and Mohamed bin Zayed University developed DeBackdoor, a framework to detect...
Elastic Security Labs has discovered a complex malware campaign, REF8685, targeting Iraq’s telecom sector. The campaign uses...
With no official streaming release for the new Snow White, many users are resorting to piracy, making...
Forescout Vedere Labs found 46 vulnerabilities in solar inverters from Sungrow, Growatt, and SMA. Exploiting these flaws...
Cloudflare’s 1-hour outage, affecting services like R2 storage and Cache Reserve, was caused by a faulty credential...
CrushFTP and Next.js face critical vulnerabilities, raising security concerns. Rapid7 warns these flaws could lead to data...
In 2024, AI-related threats grew as cybercriminals increasingly targeted large language models (LLMs). KELA’s “State of Cybercrime”...
In 2024, mobile banking malware affected nearly 248,000 users, a 3.6x jump from 69,000 the previous year....
A critical vulnerability in the popular WordPress plugin GamiPress, identified as CVE-2024-13496, allows unauthenticated SQL injection attacks...
Sygnia uncovered a cyber espionage operation by a China-linked group, “Weaver Ant.” The group targeted a major...
Microsoft experienced a major outage on March 19, 2025, affecting Outlook on the web. The issue was...
Dragon RaaS, a ransomware group blending hacktivism and cybercrime, has become a key player in the “Five...
Menlo Security’s annual Browser Security Report reveals a 130% increase in zero-hour phishing attacks and growing use...
A new cyber threat hides malware in JPEG images to steal credentials. Users download seemingly harmless images,...
Flashpoint’s 2024 report reveals a sharp rise in cyber threats, with 3.2 billion stolen credentials — a...
VPN vulnerabilities have become a major threat to organizations worldwide. Cybercriminals and state-sponsored hackers are increasingly exploiting...
The FBI warns that free file conversion tools are being used to spread malware. The FBI’s Denver...
A recent study revealed a major vulnerability in RSA keys, especially in IoT devices. Researchers found that...
A critical vulnerability, CVE-2025-24016, has been found in the Wazuh SIEM platform, affecting versions 4.4.0 to 4.9.0....
Threat actors behind SocGholish are now using hacked websites to spread RansomHub ransomware. The attack starts with...
GreyNoise has reported a coordinated wave of attacks exploiting Server-Side Request Forgery (SSRF) vulnerabilities across various platforms....
CISA has warned about a Junos OS vulnerability (CVE-2025-21590) in Juniper Networks. This flaw allows high-privileged local...
In 2025, a new wave of DCRat backdoor attacks has emerged, using the Malware-as-a-Service (MaaS) model. Cybercriminals...
A newly discovered XML External Entity (XXE) injection vulnerability in PHP allows attackers to bypass security measures...
CISA has warned about a critical Windows Win32 kernel vulnerability, identified as CVE-2025-24983. This use-after-free flaw in...
A major vulnerability, CVE-2024-31317, has been discovered in Android, allowing attackers to exploit the Zygote process for...
Rust in the Linux kernel enhances memory safety, a key focus in development. Launched in 2021 by...
Apple released iOS 18.4 Beta 3 on March 10, 2025, for developers (build number 22E5222f). While no...
Microsoft’s Time Travel Debugging (TTD) tool, used to record and replay Windows programs, has critical bugs in...
Microsoft says Silk Typhoon is now targeting remote management tools and cloud apps for access, showing a...
Cybersecurity researchers at G DATA have discovered a new malware campaign using fake booking websites to spread...
Cisco has disclosed a vulnerability in Webex for BroadWorks that could let attackers intercept user credentials and...
A serious flaw in the popular GiveWP Donation Plugin has put over 10,000 WordPress sites at risk...
Google is developing Shielded Email, a tool that creates disposable email aliases to protect users’ real Gmail...
Amnesty International’s Security Lab discovered a cyber-espionage campaign in Serbia, where authorities used a zero-day exploit chain...
Chinese hackers exploited a patched Check Point VPN flaw (CVE-2024-24919) to target organizations in Europe, Africa, and...
At Black Hat Asia 2025, experts will reveal a major flaw in modern dashcams, showing how hackers...
Pass-the-Cookie attacks let hackers bypass MFA using stolen browser cookies, putting corporate accounts at risk across Office...
Cisco has released a critical advisory for a command injection vulnerability (CVE-2025-20161) affecting its Nexus 3000 and...
Recent reports show Google’s SafetyCore service, which scans content on devices, has been quietly installed on Android...
A critical flaw in the Essential Addons for Elementor plugin, affecting over 2 million WordPress sites, exposes...
GRUB2 vulnerabilities expose millions of Linux devices to secure boot bypass and remote code execution. Discovered during...
The TgToxic Android malware, first found in July 2022, has been updated to better steal login credentials...
Palo Alto Networks researchers have discovered a new Linux malware, “Auto-Color,” which poses a serious threat due...
Google and Mandiant warn of rising phishing attacks on U.S. higher education, exploiting academic schedules and institutional...
A critical flaw (CVE-2025-27090) in the Sliver C2 server allows attackers to hijack TCP connections using SSRF,...
A malware campaign spreading XLoader malware uses DLL side-loading by exploiting a legitimate Eclipse Foundation tool, jarsigner,...
A recent phishing campaign by Hackmosphere exposed vulnerabilities among top decision-makers, like CEOs and CTOs. The study...
Researchers discovered that the malware, disguised as a Chrome update, uses Dropbox’s API to steal credentials and...
Researchers found four critical Ivanti EPM vulnerabilities allowing unauthenticated attackers to exploit machine credentials for relay attacks....
A newly discovered vulnerability in LLMs like ChatGPT raises concerns about adversarial attacks, where techniques like prompt...
A recent study from the National University of Singapore and NCS Cyber Special Ops R&D examines how...
SectopRAT (Arechclient2) is a highly obfuscated .NET-based Remote Access Trojan (RAT). Researchers recently found it posing as...
Researchers found malware targeting WordPress sites, using backdoors for remote code execution. The attacks exploit vulnerabilities, highlighting...
RansomHub has rapidly emerged as a major cybercrime syndicate in 2024–2025, expanding its arsenal to target Windows,...
PortSwigger released Burp Suite 2025.2, adding AI integration to the Montoya API for smarter, AI-powered extensions. Bug...
ClearSky Cyber Security has identified a UI vulnerability in Microsoft Windows exploited by Mustang Panda, a threat...
A subgroup of Russia’s state-backed hacker group Seashell Blizzard (Sandworm) has ramped up cyberattacks under a campaign...
OpenAI is advancing its efforts to reduce reliance on Nvidia by developing its first in-house AI chip....
New York Governor Kathy Hochul announced a ban on the use of the China-based AI startup DeepSeek...
Microsoft’s February 2025 Patch Tuesday fixes multiple vulnerabilities, including critical RCE and privilege escalation flaws. Users and...
Fortinet has issued an urgent warning about a critical zero-day vulnerability (CVE-2025-24472) in FortiOS and FortiProxy. The...
A critical SSRF flaw in Microsoft Power Platform’s SharePoint connector let attackers steal credentials and impersonate users...
Apple released iOS 18.3.1 and iPadOS 18.3.1 to fix a zero-day vulnerability exploited in targeted attacks by...
ShadowServer reports a surge in brute-force attacks on edge device logins, with up to 2.8 million IPs...
A recent cybersecurity threat in India targets users of various banks with a sophisticated malware campaign. Discovered...
MacOS users are seeing a sharp rise in password-stealing malware, spread through fake apps and ads. Leading...
IBM released critical updates for Cloud Pak for Business Automation, fixing vulnerabilities that could expose sensitive data,...
A zero-day vulnerability in Microsoft Sysinternals tools exposes Windows systems to DLL injection attacks, allowing attackers to...
The BADBOX botnet has infected over 192,000 Android devices worldwide, expanding from low-cost brands to major ones...
A newly found flaw in Voyager PHP, a Laravel management tool, risks RCE on affected servers. Discovered...
On February 3, 2025, Google released the February Android Security Bulletin, fixing 47 vulnerabilities. One major flaw,...
Silent Push coined “infrastructure laundering” to describe cybercriminals exploiting cloud services for illegal activities. They rent IPs...
A new phishing campaign is targeting high-profile X (formerly Twitter) accounts. SentinelLABS found that attackers aim to...
Trend Micro’s Managed XDR team recently uncovered a malware campaign using GitHub’s release infrastructure to spread Lumma...
DeepSeek, a fast-growing Chinese AI company, has shaken up the industry and caught cybercriminals’ attention. After its...
Google announced it blocked a record 2.28 million policy-violating apps from the Play Store in 2023. It...
Researchers from Georgia Tech and Ruhr University Bochum discovered two new speculative execution attacks, SLAP and FLOP,...
Apple released security updates for iOS, macOS, and more to address a new zero-day vulnerability, reinforcing its...
Microsoft has introduced a new phishing protection feature for Teams to enhance cybersecurity. The feature alerts users...
A new Apache Solr vulnerability, affecting versions 6.6 to 9.7.0, exposes Windows instances to risks of file...
A flaw in Android kiosk tablets at luxury hotels let attackers remotely control room functions, risking guest...
On October 29, 2024, the Mirai botnet launched a record-breaking DDoS attack, peaking at 5.6 terabits per...
Keeping systems and applications up to date is critical for security and performance in today’s rapidly evolving...
A new ransomware, “Helldown,” is exploiting vulnerabilities in Zyxel firewalls to breach corporate networks. Researchers have linked...
A critical Windows File Explorer flaw, CVE-2024-38100, has been exploited, allowing attackers to gain admin-level access through...
A security researcher recently discovered a critical SQL injection vulnerability on Microsoft’s DevBlogs site (https://devblogs.microsoft.com), allowing attackers...
FunkSec, a RaaS operator, utilizes artificial intelligence to evolve threat actor strategies. While AI aids in scaling...
A critical vulnerability in OpenAI’s ChatGPT API allows attackers to launch DDoS attacks on arbitrary websites by...
Security researchers have uncovered multiple Azure DevOps vulnerabilities, enabling CRLF injection and DNS rebinding attacks. Discovered by...
Apple has announced an exciting Information Security Internship in London, designed for tech-savvy students passionate about starting...
A highly sophisticated Linux rootkit, Pumakit, has been identified targeting critical infrastructure sectors like telecommunications, finance, and...
Microsoft Teams now lets users customize banner notification positions to improve focus and productivity. This feature is...
AWS has issued a critical security advisory for vulnerabilities in certain versions of its clients for Amazon...
A Russian developer, supported by the National Technology Initiative, has launched the Apparatus Sapiens AI module to...
Researchers have discovered “Sneaky 2FA,” a phishing kit targeting Microsoft 365 accounts to steal credentials and bypass...
Researchers discovered a misconfiguration in on-premise applications that bypasses Active Directory Group Policy meant to disable NTLMv1,...
Cybercriminals are running advanced phishing attacks on Microsoft 365 users using fake URLs that closely resemble real...
Hackers are targeting Fortinet FortiGate firewalls with exposed management interfaces online. Arctic Wolf reports that between November...
Microsoft has warned of an MFA issue affecting some Microsoft 365 users, blocking access to certain applications...
Juniper Networks disclosed CVE-2025-21598, a critical vulnerability in Junos OS and Junos OS Evolved, allowing remote attackers...
Cybercriminals are exploiting critical LDAP vulnerabilities (CVE-2024-49112 and CVE-2024-49113) by distributing fake proof-of-concept (PoC) exploits for “LDAPNightmare”...
The PRIVESHIELD browser extension automatically creates isolated profiles to group websites based on browsing habits and interactions,...
Google has updated Chrome to version 131.0.6778.264/.265 for Windows and Mac, and 131.0.6778.264 for Linux, fixing critical...
Hackers breached Argentina’s Airport Security Police (PSA) payroll system, exposing sensitive employee information. They accessed salary records...
Cybercriminals created PhishWP, a malicious WordPress plugin, to mimic payment gateways like Stripe for phishing attacks on...
The January 2025 Android Security Bulletin highlights critical vulnerabilities affecting Android devices. Users should update to security...
A critical vulnerability has been found in the UpdraftPlus: WP Backup & Migration Plugin, affecting over 3...
A PoC exploit for the critical OpenSSH vulnerability CVE-2024-6387 has been released, enabling remote attackers to execute...
Apple has agreed to pay $95 million to settle a class-action lawsuit claiming Siri violated users’ privacy...
ASUS warns of critical router flaws (CVE-2024-12912, CVE-2024-13062) allowing arbitrary command execution. Users are urged to update...
Cyberhaven, a cybersecurity company, revealed that its Chrome extension, with over 400,000 users, was targeted in a...
Researchers warn of a public PoC exploit for a critical Oracle WebLogic vulnerability. Oracle WebLogic Vulnerability The...
Microsoft has warned of an issue affecting Windows 11 version 24H2 that blocks critical security updates. The...
Researchers observed increased activity from the “FICORA” and “CAPSAICIN” variants, which exploit vulnerabilities in outdated D-Link routers...
IBM has warned of two security flaws (CVE-2024-47102 and CVE-2024-52906) in its AIX operating system that could...
Adobe released a critical security update for ColdFusion to address a vulnerability that allows attackers to read...
Threat analysts report the “Araneida Scanner,” based on a cracked Acunetix version, is used for illegal activities...
A critical command injection vulnerability in the systeminformation npm package, CVE-2024-56334, exposes millions of systems to RCE...
The “BMI CalculationVsn” app on the Amazon App Store secretly collects sensitive data, like app package names...
Researchers uncovered a malware campaign in the npm ecosystem, where “k303903” used fake packages to spread the...
BADBOX is a cybercriminal operation that infects Android devices, like TV boxes and smartphones, with malware before...
Researchers have observed a rise in malicious activity on the VSCode Marketplace, exposing its vulnerability to supply...
Recent research links The Mask group to a 2022 attack on a Latin American organization, exploiting an...
VIPKeyLogger, similar to the Snake Keylogger, spreads through phishing campaigns via attachments disguised as archive or Microsoft...
The FLUX#CONSOLE campaign exploits .MSC files to deploy backdoor malware, highlighting advanced phishing and Windows feature abuse....
Cybercriminals are using fake CAPTCHA pages to spread password-stealing malware. These fake CAPTCHAs, often appearing as pop-ups,...
Hackers are exploiting a new Apache Struts2 vulnerability (CVE-2024-53677) with a critical CVSS score of 9.5, posing...
Hackers used Microsoft Teams to trick victims into granting remote system access, showcasing advanced social engineering tactics,...
Dell Technologies has issued a security advisory for critical vulnerabilities that could be exploited by attackers. Customers...
Researchers at Elastic Security Labs discovered PUMAKIT, a Linux malware using stealth and unique privilege escalation to...
A new vulnerability in Facebook Messenger for iOS could disrupt group calls by exploiting emoji reactions. Discovered...
Researchers have found vulnerabilities in the infotainment systems of some Skoda and Volkswagen cars, which could let...
Microsoft is investigating a widespread outage that impacted access to Microsoft 365 web apps and the admin...
Realst malware targets Web3 professionals using fake companies like “Meetio” with AI-generated content. Victims are lured into...
Microsoft’s final Patch Tuesday of 2024 addresses 71 vulnerabilities, including 16 critical ones and a zero-day. This...
A critical vulnerability in Qlik Sense for Windows may allow remote code execution. It affects all versions...
Cipla, an Indian pharmaceutical company, has reportedly been attacked by the Akira ransomware group. The hackers claim...
Google has launched Vanir, an open-source tool to simplify and automate security patch validation. First previewed at...
SonicWall warns of critical flaws in SMA 100 series appliances, enabling remote code execution, authentication bypass, and...
A newly discovered vulnerability in HCL Software’s DevOps Deploy and Launch platforms, CVE-2024-42195, allows attackers to insert...
Researchers reported CVE-2023-49785, a critical ChatGPT Next Web (NextChat) vulnerability, raising cybersecurity concerns over its SSRF exploitation...
APT36, a Pakistani cyber-espionage group, now uses ElizaRAT, a Windows RAT with advanced evasion and C2 features,...
Hackers exploit wevtutil.exe for LOLBAS attacks, enabling command execution, payload downloads, and persistence while bypassing security. wevtutil.exe...
CVE-2024-44308, a critical Safari vulnerability, has been actively exploited, impacting iOS, visionOS, and macOS. Affected Software and...
Amazon has improved cloud security with AI/ML threat detection in GuardDuty. This new feature enhances threat detection...
HPE has released a security alert about a critical flaw in its IceWall product, CVE-2024-11856, which lets...
Uniswap Labs has launched a $15.5 million bug bounty to secure its new protocol, Uniswap v4—the largest...
Cybersecurity researchers have uncovered a large-scale DDoS campaign attributed to a threat actor known as “Matrix.” Despite...
PixPirate malware is targeting users in Brazil, India, Italy, and Mexico, posing as a fake authentication app...
NVIDIA has issued a critical security update for a major vulnerability in its Unified Fabric Manager (UFM)...
ProjectSend, an open-source file-sharing web app, is actively being exploited after CVE-2024-11680 was assigned on November 25,...
GodLoader malware, discovered by Check Point, stealthily infects Windows, macOS, Linux, Android, and iOS, using the Godot...
The Russian-aligned group RomCom exploited two critical zero-day vulnerabilities in Mozilla Firefox and Windows in a sophisticated...
A major data breach has caused widespread concern, as a database with sensitive financial details of over...
Meta has removed over 2 million accounts involved in malicious activities, including complex fraud schemes like “pig...
The Python-based NodeStealer has evolved, now targeting Facebook Ads Manager budgets, stealing credit card info, and browser...
Helldown, a new ransomware group, has been exploiting vulnerabilities to breach networks and compromise victims since August...
Two malicious Python packages pretending to be tools for ChatGPT and Claude were found on PyPI, the...
Trend Micro has revealed a critical vulnerability in Deep Security 20 Agent that could allow remote code...
Recent threat analysis examined outbound traffic and binaries in container environments. Researchers, using honeypot data and threat...
A new vulnerability, CVE-2024-31141, was found in Apache Kafka Clients, allowing attackers to escalate privileges and gain...
A critical unpatched vulnerability has been found in Citrix Virtual Apps and Desktops, now being actively exploited....
Zoho released a security update for a critical SQL injection flaw in ADAudit Plus (CVE-2024-49574), fixed in...
CISA issued an urgent alert for two Palo Alto Networks vulnerabilities, CVE-2024-9463 and CVE-2024-9465, which are actively...
Chinese hacker group SilkSpecter launched a phishing campaign targeting Black Friday shoppers in Europe and the USA,...
Critical flaw found in ‘Really Simple Security’ WordPress plugin, risking 4M+ sites. CVE-2024-10924 allows potential remote attacks...
A recently discovered zero-day vulnerability, CVE-2024-43451, is being actively exploited, targeting Windows systems across multiple versions. Identified...
Google Cloud will start issuing CVEs for critical vulnerabilities in its services, aiming to boost transparency and...
Dell Technologies has revealed critical vulnerabilities in its Enterprise SONiC OS (versions 4.1.x and 4.2.x), which could...
Amazon confirmed that employee data was exposed due to a breach at a third-party vendor, which exploited...
Researchers have found that Fakebat malware is again being spread through malicious Google Ads, targeting users searching...
Researchers found five malicious npm packages targeting Roblox developers, stealing credentials and personal data. These packages, including...
Hackers exploit Excel documents due to their popularity and built-in vulnerabilities. With VBA macros now blocked by...
CheckPoint security experts recently warned about fake copyright claims spreading Rhadamanthys stealer malware. Stealer malware is designed...
A critical vulnerability in Cisco Unified Industrial Wireless Software, affecting Cisco Ultra-Reliable Wireless Backhaul (URWB) Access Points,...
Recent research has identified a new Android malware strain, initially mistaken for TgToxic, now called ToxicPanda. Although...
The threat actor known as IntelBroker, along with EnergyWeaponUser, has claimed responsibility for a major data breach...
The “ClickFix” tactic exploits fake Google Meet and Zoom pages to deliver advanced malware, mimicking legitimate video...
Palo Alto Networks’ Unit 42 recently found that hackers are using AV and EDR bypass tools from...
Researchers have shown an exploit for the Spectre Flaw, targeting the Indirect Branch Predictor Barrier (IBPB) vulnerability....
The Meta malvertising campaign, active for over a month, spreads SYS01 InfoStealer by disguising it within ElectronJs...
Evasive Panda deployed a new C# tool, CloudScout, in early 2023 to target a Taiwanese government entity....
Google has released a Chrome update addressing critical vulnerabilities, safeguarding millions of users. The latest Stable version,...
Recent cyberattacks by Akira and Fog threat actors have targeted multiple industries by exploiting a vulnerability (CVE-2024-40766)...
WrnRAT is a new malware that cybercriminals deploy by disguising it as popular gambling games like Badugi,...
Multiple vulnerabilities in the Realtek SD card reader driver, RtsPer.sys, affect laptops from major brands like Dell...
WhatsUp Gold, a popular network monitoring tool, has a critical vulnerability in versions before 2024.0.0, exposing organizations...
Cisco issued a critical advisory for a vulnerability in its Adaptive Security Appliance (ASA) Software that could...
Stored XSS vulnerability in Roundcube Webmail is exploited in attacks on ex-USSR government agencies. Researchers identified the...
GitLab released patches (17.5.1, 17.4.3, and 17.3.6) for both Community and Enterprise Editions, fixing a critical HTML...
Lazarus APT exploited a Chrome zero-day using a crypto-themed game as bait, showcasing the group’s evolving financial...
Broadcom has issued critical security updates for severe vulnerabilities in VMware vCenter Server that allow remote code...
Phishing attacks trick individuals into revealing sensitive info by impersonating trusted entities, often through urgent emails with...
Kaspersky reports nearly 10 million personal and corporate devices were compromised by data-stealing malware in 2023, a...
PNG files are popular and widely used on the internet, making them a tempting target for threat...
Hackers posed as ESET to spread wiper malware via phishing emails starting October 8, 2024. The emails,...
Bumblebee malware has reemerged, threatening corporate networks globally, following its first sighting since Europol’s May 2024 Operation...
A group of hackers reportedly sells sensitive data stolen from Cisco, allegedly by IntelBroker in collaboration with...
The ErrorFather campaign, a new variant of the Cerberus banking trojan, emerged in September 2024. It uses...
Infostealer malware, like the recently identified PureLogs, poses significant risks due to its low cost and ease...
Hackers exploit a zero-day vulnerability (CVE-2024-43047) in Qualcomm chipsets, risking millions of Android users globally. The flaw...
Researchers revealed six new vulnerabilities, including a critical one in Foxit PDF Reader that allows arbitrary code...
A critical use-after-free vulnerability in Firefox and Firefox Extended Support Release (ESR) is being actively exploited in...
CISA warns of two critical Microsoft zero-day vulnerabilities, CVE-2024-43572 and CVE-2024-43573, actively exploited in the wild. CVE-2024-43572...
Hackers infiltrated JAXA, compromising top officials’ accounts, including President Hiroshi Yamakawa, in a series of cyberattacks since...
Attackers used the EternalBlue vulnerability to access the observatory farm, create a hidden admin share, and run...
A critical vulnerability in the Cacti network monitoring tool, discovered in version 1.2.28, could allow attackers to...
A researcher identified a method to exploit Visual Studio by executing arbitrary code during the debugging of...
FakeUpdate, a fake browser update scam, is now targeting users in France, aiming to deploy the WarmCookie...
Perfctl, a stealthy malware, is actively targeting millions of Linux servers worldwide. Discovered by Aqua Nautilus researchers,...
The Browser Company has launched a Bug Bounty Program for its Arc Browser after quickly resolving a...
Google released a Chrome update fixing critical vulnerabilities that could allow arbitrary code execution. Version 129.0.6668.89/.90 is...
XWorm is a malware known for its obfuscation techniques and ability to evade detection, posing a significant...
Hackers are exploiting Docker Swarm, Kubernetes, and SSH servers, targeting Docker API vulnerabilities as the entry point...
Developers of the Linux printing system CUPS recently disclosed several vulnerabilities that could allow attackers to execute...
The newly emerged Gorilla Botnet has launched over 300,000 DDoS attacks across 100+ countries from September 4...
Diehl Defence anti-aircraft missiles are successfully intercepting Russian attacks on Kyiv, with a 100% hit rate. Germany...
Phishing attackers used an HTML smuggling technique to deliver malware. The attack began with a phishing email...
NIST released new password security guidelines in Special Publication 800-63B, improving cybersecurity and user experience. One of...
CAPTCHAs, or Completely Automated Public Turing tests, are used online to verify users are human, not bots....
A critical vulnerability in TeamViewer’s Windows Remote client, CVE-2024-7479 and CVE-2024-7481, allows attackers to elevate privileges on...
Recently, Google alerted organizations about North Korean IT workers acting on behalf of hackers. Organizations today face...
Researchers at BitSight TRACE found multiple 0-day vulnerabilities in ATG systems used to manage fuel storage tanks,...
Cisco revealed a critical vulnerability, CVE-2024-20439, in its Smart Licensing Utility, allowing unauthorized access due to a...
Apple’s macOS 15 Sequoia update has broken several key security tools, sparking user frustration across social media...
A new malware campaign is gaining traction online, using fake CAPTCHA sites to trick users into installing...
The Walt Disney Company will stop using Slack for internal communication following a hack that leaked over...
A critical 0-click RCE vulnerability (CVE-2024-20017) in MediaTek Wi-Fi 6 chipsets, used by devices like Ubiquiti, Xiaomi,...
A threat actor has allegedly claimed a breach of Federal Bank, exposing sensitive data of hundreds of...
HZ RAT, a remote access trojan (RAT) that has targeted Windows devices since 2020, has recently been...
A hacking group has claimed responsibility for breaching the Dell employee database, asserting access to sensitive information...
CISA has issued six advisories highlighting vulnerabilities in various industrial control systems. The advisories cover: These advisories...
Researchers discovered a large Chinese state-sponsored IoT botnet, “Raptor Train,” which compromised over 200,000 SOHO and IoT...
A threat actor is reportedly selling a database from Bharat Petroleum Corporation Limited (BPCL). DarkWebInformer first reported...
Amazon Prime Day scams refer to fraudulent schemes that exploit the retailer’s sell-off day. While the event...
Apple has released iOS 18, fixing 32 security vulnerabilities. The update is available for iPhone XS and...
North Korean hackers are targeting LinkedIn users with advanced malware called RustDoor. This highlights the growing use...
Threat actors are exploiting Selenium Grid’s default lack of authentication in two active campaigns, deploying exploit kits,...
Millions of D-Link routers are vulnerable to critical security flaws. Urgent firmware updates have been released, and...
Adobe’s September 2024 updates fixed 28 vulnerabilities, including a critical ColdFusion flaw (CVSS 9.8). Other affected products...
Hackers are exploiting a critical Apache OFBiz vulnerability (CVE-2024-45195) that allows unauthenticated remote code execution, threatening organizations...
Kali Linux 2024.3, the latest version of Offensive Security’s Debian-based distribution for ethical hacking, has been released....
Cody Thomas created Apfell in 2018, an open-source macOS post-exploitation framework that later evolved into Mythic, a...
Recent research has uncovered new Android Spyware targeting mnemonic keys, vital for cryptocurrency wallet recovery. Disguised as...
Hackers target SMBs because they often have weaker security and lack cybersecurity awareness. Without regular security audits...
Zyxel released critical hotfixes to fix a command injection vulnerability in two of its NAS products, NAS326...
Cybersecurity researchers at Fortinet recently discovered that hackers have been exploiting GeoServer RCE vulnerability to deploy malware,...
Critical vulnerabilities have been found that could let attackers execute commands on systems. These issues, listed in...
SonicWall revealed a critical RCE vulnerability (CVE-2024-40766) in SonicOS on August 22, 2024. Initially, no exploitation was...
Recent research shows Predator spyware has resurfaced with improved evasion techniques, despite US sanctions. It’s still active...
The Tor Project has released Tor Browser 13.5.3, featuring important security updates and usability improvements. You can...
Lazarus Group, a notorious North Korean-linked hacker group active since 2010, has intensified its attacks in 2024....
ToddyCat is an APT group active since December 2020, targeting government and military entities in Europe and...
Emansrepo, a Python infostealer, is spread through phishing emails with fake purchase orders. The attack has evolved,...
The D-Link DAP-2310 Wireless Access Point is vulnerable to remote code execution, allowing attackers to gain unauthorized...
DeadXInject, the group behind AresLoader and AiDLocker ransomware, is now offering ManticoraLoader, a new Malware-as-a-Service (MaaS) targeting...
Researchers have identified a sophisticated phishing campaign using a .NET-based Snake Keylogger variant. This attack uses weaponized...
Proofpoint researchers have uncovered a cyberattack campaign, “Voldemort,” using Google Sheets as a C2 platform. Targeting Windows...
A malicious AutoIT executable opens Gmail login pages and steals clipboard data, captures keystrokes, and controls system...
A sophisticated malware is threatening organizations in the Middle East by disguising itself as the legitimate Palo...
A critical vulnerability in App::cpanminus (cpanm), a popular tool for installing Perl modules, has been identified. Known...
The eight Android and iOS apps fail to protect user data by transmitting sensitive information, such as...
Attackers can exploit Windows drivers to bypass security by exploiting vulnerabilities or using stolen signatures to load...
A recently disclosed vulnerability in the Apache Portable Runtime (APR) library, identified as CVE-2023-49582, could expose sensitive...
Microsoft 365 users report emails with images being wrongly flagged as malware and quarantined, identified as Issue...
Patelco Credit Union revealed a ransomware attack compromising member and employee data, raising concerns about security and...
Researchers discovered a new malware campaign called BeaverTail, targeting job seekers in a North Korean cyber espionage...
Google has released Chrome 128 (128.0.6613.84 for Linux and 128.0.6613.84/.85 for Windows and Mac) to address a...
Cybercriminals are using Google search ads to distribute malware disguised as legitimate ads for Slack. This advanced...
ESET researchers recently identified new Android malware called “Ngate” that allows hackers to withdraw money from victims’...
Recent Log4j attacks use obfuscated LDAP requests to execute malicious scripts, establish persistence, and exfiltrate data. Multiple...
Researchers uncover new attack vectors in MIFARE Classic cards by analyzing the CRYPTO-1 algorithm and vulnerabilities, demonstrating...
UULoader malware delivers payloads like Gh0st RAT and Mimikatz, targeting Korean and Chinese speakers through malicious installers....
A critical security vulnerability affects Dell SupportAssist for Home PCs, specifically in installer version 4.0.3. Dell SupportAssist...
A critical vulnerability (CVE-2024-5932) in the GiveWP plugin exposes over 100,000 WordPress sites to remote code execution...
RipperSec, a pro-Palestinian Malaysian hacktivist group that started on Telegram in June 2023, has quickly grown to...
A critical vulnerability in the Windows TCP/IP stack enables unauthenticated remote code execution (RCE) through specially crafted...
A critical vulnerability in Microsoft apps for macOS allowed hackers to surreptitiously spy on Mac users’ activities....
A new threat called Styx Stealer has emerged, targeting users by stealing sensitive data like saved passwords,...
Recent research revealed a vulnerability in the Android package of many Google Pixel smartphones. Devices shipped globally...
The notorious Lazarus hacker group exploited a zero-day vulnerability in Microsoft Windows, targeting the Ancillary Function Driver...
In July 2022, Microsoft patched a PPL bypass flaw, but a new exploit called “BYOVDLL” has been...
Cybersecurity researchers have uncovered a sophisticated malspam campaign targeting users via email and phone. Attackers are exploiting...
A ransomware group, RansomHub, has introduced EDRKillShifter, a tool designed to disable EDR systems. This advancement highlights...
IBM recently revealed critical vulnerabilities in QRadar Suite Software and IBM Cloud Pak for Security. Exploitation of...
Threat actors frequently exploit browser flaws to gain unauthorized access and conduct various illicit activities. Recently, Oligo...
SAP has issued a major security update addressing critical authentication bypass and server-side request forgery vulnerabilities, with...
A critical vulnerability in 1Password for macOS allows attackers to bypass security measures and access vault items....
A vulnerability, CVE-2024-38856, has been found in Apache OFBiz, allowing unauthenticated remote code execution. A patch is...
Recently, Trend Micro researchers uncovered a sophisticated malvertising campaign targeting social media users with a multi-step deception...
Cybersecurity experts have uncovered sophisticated Android spyware, LianSpy, targeting users to steal sensitive data. It uses advanced...
A Russia-linked threat actor used a car ad to phish diplomats and deliver the HeadLace backdoor, likely...
Voice Over Wi-Fi (VoWiFi) is commonly used for making voice calls over Wi-Fi, improving call quality and...
Researchers found a flaw in Ubiquiti G4 Wi-Fi cameras that exposes critical data. They believe a similar...
Hackers are exploiting a critical vulnerability (CVE-2024-6220) in the WordPress plugin 简数采集器 (Keydatas) that allows unauthenticated users...
Microsoft has patched critical vulnerabilities in Edge. Users should update to the latest version to ensure security....
A critical flaw in GeoServer, an open-source Java software, exposes thousands of servers to risk. The vulnerability,...
Guardio Labs recently identified “EchoSpoofing,” a critical vulnerability in Proofpoint’s email protection service used by 87% of...
Cybersecurity firm TrustedSec has introduced a new tool named Specula, which leverages a longstanding vulnerability in Microsoft...
Microsoft is investigating a global outage affecting access to some Microsoft 365 and Azure services. Microsoft 365...
Attackers are using Gh0stGambit to spread Gh0st RAT malware to Chinese users via a fake Google Chrome...
Progress, the company behind MOVEit Transfer, has issued a critical security alert for a newly discovered vulnerability...
Hackers exploit malicious Python packages to attack developer environments, inject harmful code, and steal sensitive information or...
A critical local privilege escalation vulnerability (CVE-2024-41637) was found in RaspAP, an open-source project for turning Raspberry...
Indian iPhone users are inundated with SMS phishing scams posing as India Post delivery notifications, aimed at...
The hacktivist group USDoD claims to have leaked CrowdStrike’s “entire threat actor list” and an “entire IOC...
Google Chrome now has a new download system with alerts for potentially harmful files, enhancing user security....
A new threat, Jellyfish Loader, has been identified as a .NET-based shellcode downloader disguised as a Windows...
“Krampus,” a new malware loader, is gaining popularity on the dark web, according to MonThreat on X...
Malicious Python packages uploaded by “dsfsdfds” to PyPI stole sensitive data from user systems and sent it...
Researchers at Sucuri recently discovered that website swap files can be exploited to install a persistent credit...
Cisco disclosed a significant flaw in the upload module of RV340 and RV345 VPN routers, allowing remote,...
Since July 4, 2024, SocGholish (FakeUpdates) has shown new behavior. The infection chain starts with a compromised...
SonicWall has disclosed a critical heap-based buffer overflow vulnerability in SonicOS IPSec VPN, identified as CVE-2024-40764, which...
New research reveals a novel approach to hiding malware in APK installers. Adversaries manipulate the file header...
Threat actor ‘Hana’ claims to have breached Dettol India, affecting 453,646 users, according to a FalconFeedsio post...
A recent CrowdStrike update has caused widespread Blue Screen of Death (BSOD) errors on Windows machines. The...
HTTP Request Smuggling exploits differences in how web servers and intermediaries handle HTTP request sequences. Attackers craft...
X-Labs identified ransomware targeting Turkish businesses through PDF attachments in emails from the internet[.]ru domain. These PDFs...
In early 2024, Cofense researchers discovered Poco RAT, a malware specifically targeting Spanish-speaking individuals in the mining...
In 2022, HardBit Ransomware 4.0 emerged, differing from typical groups by avoiding leak sites and double extortion....
Pinterest, with over 518 million users, faces a potential data leak. Hacker “Tchao1337” claims to have leaked...
Hackers target Juniper Junos due to its extensive use in business networking, making it a prime target...
Imagine receiving an email that appears completely legitimate. This is the deceptive capability of the new FishXProxy...
McAfee Labs researchers have identified a sophisticated malware delivery method, “ClickFix,” using advanced social engineering to trick...
Microsoft’s July security update addresses 142 vulnerabilities, including one already being exploited. This update is part of...
International cybersecurity agencies have issued a warning about APT40, a PRC state-sponsored cyber group linked to the...
Ransomware-as-a-service (RaaS) has evolved into a sophisticated, enterprise-like model. From 2022 to 2023, ransomware ads on the...
Researchers discovered that attackers can exploit improperly configured Jenkins Script Console for criminal activities like cryptocurrency mining....
A critical vulnerability, CVE-2024-29510, has been discovered in the Ghostscript rendering platform. This format string flaw affects...
The first half of 2024 has witnessed a notable surge in info-stealing malware masquerading as AI tools...
A new multi-stage trojan, “Orcinius,” exploits Dropbox and Google Docs. It starts with an Excel spreadsheet containing...
eSentire’s Threat Response Unit (TRU) has uncovered a sophisticated campaign in which threat actors exploit the ScreenConnect...
A vulnerability in an unauthenticated endpoint allowed threat actors to identify phone numbers associated with Authy accounts....
Hackers are targeting and weaponizing AnyDesk, Zoom, Teams, and Chrome due to their widespread use across multiple...
A newly discovered OpenSSH vulnerability, dubbed regreSSHion, allows remote attackers to gain root privileges on Linux systems...
Transparent Tribe (aka APT36), active since 2016, uses social engineering to target Indian government and military personnel....
Google has launched kvmCTF, a new vulnerability reward program targeting the Kernel-based Virtual Machine (KVM) hypervisor. Announced...
Cybercriminals are exploiting Binance smart contracts as intermediary C2 servers, favoring them due to their resilience against...
A new malicious code execution technique, GrimResource, targets Microsoft Management Console. Attackers exploit an old cross-site scripting...
A critical vulnerability in OpenSSH, affecting versions 8.5p1 to 9.7p1, has been discovered, potentially exposing millions of...
Hackers exploit Chrome extensions to embed malware, gather personal data, display pop-ups, change URLs, and manipulate the...
Threat actors leverage RATs for sustained access to compromised systems, facilitating prolonged espionage and exploitation. North Korean...
A PoC exploit for the SQL Injection vulnerability CVE-2024-5276 in Fortra FileCatalyst Workflow has been released, affecting...
A critical vulnerability, CVE-2024-5806, in MOVEit Transfer software poses severe risks to organizations relying on it for...
A threat actor has publicly claimed a zero-day vulnerability in the widely-used Google Chrome browser. The account...
A new threat actor has surfaced, claiming a zero-day vulnerability in the Linux GRUB bootloader for local...
Talos Intelligence has uncovered a sophisticated cyber campaign orchestrated by the threat actor SneakyChef. This operation utilizes...
A Microsoft Power BI vulnerability allows unauthorized access to sensitive data in reports, affecting tens of thousands...
Hackers frequently target ESXi systems due to their extensive use in managing enterprise virtualized infrastructure, making them...
A new security flaw allows attackers to impersonate Microsoft corporate email accounts, increasing phishing risks. Discovered by...
Hackers are increasingly exploiting Progressive Web Apps (PWAs) for sophisticated phishing attacks to steal user credentials, as...
Cybersecurity researchers have uncovered a sophisticated malware campaign by the Void Arachne group, targeting Chinese-speaking users with...
Google has released a new Chrome browser update, version 126.0.6478.114/115 for Windows and Mac, and 126.0.6478.114 for...
The Spinning YARN attackers have initiated a fresh cryptojacking campaign, focusing on publicly exposed Docker Engine hosts....
A critical vulnerability in several D-Link wireless router models allows unauthenticated attackers to gain administrative access. The...
Recent research uncovered websites deploying Lumma Stealer disguised as browser updates. These sites, posing as tutorial pages...
On Patch Tuesday, June 11, 2024, Microsoft fixed numerous flaws, including a remote code execution vulnerability in...
WARMCOOKIE is a new Windows backdoor delivered via a phishing campaign called REF6127. It can take screenshots,...
A significant vulnerability, CVE-2024-37629, has been discovered in SummerNote 0.8.18, allowing Cross-Site Scripting (XSS) via the Code...
SSH and RDP provide remote server access (Linux and Windows respectively) for administration. Both protocols are vulnerable...
Hackers target Apple due to its large user base and wealthy customers, including business people and managers...
Malware distributors exploit MSI installers because Windows OS inherently trusts them to run with administrative rights, bypassing...
A popular ZKTeco biometric terminal has critical vulnerabilities, including an SQL injection flaw via QR codes. This...
A new prompt injection vulnerability, CVE-2024-5184, has been found in EmailGPT, the service and Chrome plugin that...
A PoC exploit has been released for the critical Veeam Backup Enterprise Manager authentication bypass vulnerability, CVE-2024-29849,...
Apache RocketMQ, a widely used messaging system for handling high volumes of data and critical operations, often...
The new ‘Fog’ ransomware targets US education and recreation businesses. Attackers used compromised VPN credentials from two...
Cisco disclosed a major security vulnerability in its Webex Meetings platform, affecting some customers in its Frankfurt...
Phishing attackers distribute email attachments with malicious HTML files designed to exploit users into running the code...
Zyxel has identified and released security patches for critical vulnerabilities affecting their NAS326 and NAS542 devices. These...
In South Korea, attackers distribute malware disguised as cracked software, including RATs and crypto miners, and register...
Hackers exploit the widespread use and trust of Word documents, easily deceiving users into opening them. These...
Since Russia’s invasion of Ukraine on February 24, 2022, tensions have been high globally. Following the invasion,...
A critical vulnerability in the Citrix Workspace app for Mac, tracked as CVE-2024-5027, could allow attackers to...
Microsoft Office provides tools for creating professional reports, college essays, CVs, and notes on Office 365. It...
A new privilege escalation vulnerability (CVE-2024-29072, severity 8.2 High) has been discovered in multiple versions of Foxit...
A new ransomware strain called Embargo, written in Rust, has surfaced with its Darknet infrastructure. Using double...
Hackers frequently target routers, the gateways connecting devices and networks to the internet, because they are often...
A recent study by University of Maryland security researchers revealed a major privacy vulnerability in Apple’s Wi-Fi...
A critical vulnerability in Git, known as CVE-2024-32002, has recently emerged, posing substantial risks to users of...
Researchers discovered REF4578, an intrusion set that exploits vulnerable drivers to disable EDRs for crypto mining and...
Microsoft is focusing on security in Windows, introducing Secured-Core PCs against hardware to cloud attacks and expanding...
Zabbix, a widely used network monitoring tool in corporate IT infrastructure globally, is susceptible to SQL injection...
Recently, cybersecurity researchers at Symantec uncovered a fresh Linux backdoor actively targeting users through installation packages. All...
Apple has rolled out security updates to tackle a zero-day vulnerability in its Safari web browser, exploited...
Wireshark, the leading network protocol analyzer, has just released version 4.2.5, introducing numerous new features and enhancements....
Researchers have uncovered four significant vulnerabilities in the ThroughTek Kalay Platform, utilized by 100 million IoT-enabled devices....
Google has released a critical security update for its Chrome browser upon uncovering a zero-day vulnerability actively...
Recent email campaigns distribute DanaBot malware through two document types: those exploiting equation editor and those with...
iTunes has an arbitrary code execution vulnerability, potentially enabling attackers to execute malicious code. Apple has issued...
Security researchers have published a Proof-of-Concept (PoC) exploit for a critical vulnerability in the widely used PuTTY...
A zero-day vulnerability in Microsoft Edge, identified as CVE-2024-4671, has been actively exploited by malicious organizations, as...
Cacti, a widely used network monitoring tool, has released a critical security update addressing various vulnerabilities, notably...
Two critical vulnerabilities in F5 Next-Gen Big IP have been uncovered, enabling threat actors to attain full...
Dell Technologies recently disclosed a data breach involving a company portal containing limited customer information related to...
A critical vulnerability, CVE-2024-4040, has been actively exploited in the wild in CrushFTP. This flaw permits attackers...
Hackers exploit weaponized shortcut files because they can execute malicious code without targeting specific users. Given their...
The MorLock ransomware group has escalated its assaults on Russian businesses, resulting in disruptions and financial setbacks....
Security researcher Bassem Essam uncovered a critical cross-site scripting (XSS) vulnerability in the widely-used Yoast SEO WordPress...
A major update for Trend Micro’s Antivirus One software has been launched. This update tackles a critical...
The MITRE Corporation, a non-profit organization managing research and development centers for the U.S. government, has revealed...
Researchers have unveiled a new malware strain named “Cuckoo,” combining features of spyware and infostealers, designed to...
A directory traversal vulnerability (CVE-2024-23334) in aiohttp versions before 3.9.2 permits remote attackers to access sensitive files...
Multiple vulnerabilities in ArubaOS affect HPE Aruba Networking devices, including Mobility Conductor, Mobility Controllers WLAN Gateways, and...
Cuttlefish is a recently discovered malware platform that has been active since at least July 2023. It...
Gemini 1.5 Pro represents the latest iteration of the Gemini AI malware analysis platform, poised to revolutionize...
A new RAT malware targeting Android devices has been discovered, capable of executing additional commands compared to...
Researchers have discovered a new infection chain linked to the DarkGate malware. This Remote Access Trojan (RAT),...
BlackBerry initially reported a new iOS LightSpy malware, but Huntress researchers discovered it as a macOS variant...
XLab researchers uncover “Wpeeper,” a new Android malware infiltrating systems to execute various malicious commands, posing a...
A severe SQL injection vulnerability has been discovered in Grafana, a popular open-source platform extensively used for...
A new threat has surfaced, impacting millions of devices globally. The PlugX USB worm, a sophisticated malware,...
The FROZEN#SHADOW attack campaign employs SSLoad malware alongside Cobalt Strike Implants to seize control of the entire...
Since November 2023, the Cactus ransomware gang has been exploiting vulnerable Qlik Sense servers, leveraging multiple vulnerabilities...
Autodesk Drive serves as a cloud-based data-sharing platform for organizations, facilitating document and file sharing. It accommodates...
Avast researchers recently uncovered GuptiMiner, an aged malware. It leverages the eScan antivirus update system to surreptitiously...
GitLab has issued security patches (16.11.1, 16.10.4, and 16.9.6) for both Community and Enterprise Editions, emphasizing the...
CrushFTP disclosed a zero-day vulnerability (CVE-2024-4040) affecting versions below 10.7.1 and 11.1.0, allowing remote attackers with low...
The OpenMetadata platform has critical vulnerabilities reported by Microsoft Security Blog, enabling attackers to exploit Kubernetes workloads...
Oracle VirtualBox had a critical vulnerability (CVE-2024-21111) allowing Privilege Escalation and Arbitrary File Move/Delete, rated 7.8 (High)....
Russian threat group APT29 targeted German political parties with a new backdoor, WINELOADER, via spear-phishing emails containing...
Hackers frequently exploit PyPI packages to inject malicious code into widely-used Python libraries, seeking vulnerabilities. Recently, FortiGuard...
Cybercriminals frequently deploy Linux ransomware in server environments, targeting organizations with critical data for potentially higher payouts....
Microsoft’s Active Directory (AD) acts as the backbone of your organization’s network, regulating access to network and...
Tor Browser 13.0.14 is now available, featuring crucial security enhancements for the widely-used privacy-centric web browser. Tor...
The cybersecurity community warns of the rising threat of a “mobile NotPetya” event, a self-propagating mobile malware...
Hackers exploit LockBit 3.0 ransomware for its advanced encryption, successfully locking victims’ files for ransom. Its stealthiness...
Two recently discovered SharePoint techniques empower malicious actors to circumvent conventional security measures and extract sensitive data...
A recently discovered malware dubbed LightSpy has been found to target both Android and iOS users. LightSpy,...
Palo Alto Networks alerts customers to a critical command injection vulnerability in PAN-OS GlobalProtect feature, scoring the...
Hackers are employing malware-infected devices for scanning target networks rather than conducting direct scans. This strategy allows...
LG has addressed four critical vulnerabilities found in numerous TV models, dating back to 2023, which could...
On April Patch Tuesday, Microsoft addressed 149 bugs, one of its largest security updates, spanning various products...
Andres Freund discovered a backdoor in the liblzma library, part of the XZ data compression tool. The...
Cybersecurity researchers uncover a complex multi-stage attack employing invoice-themed phishing decoys to distribute various malware, including Venom...
Google has revealed the detection of two Android zero-day security vulnerabilities in its Pixel smartphones, with patches...
Since 2021, a fake e-shop scam campaign has targeted Southeast Asia, with increased activity observed by CRIL...
Progress Flowmon is a network monitoring and security solution developed by Progress, a software company. It is...
Cybercriminals are exploiting YouTube, a platform adored by millions, to orchestrate advanced malware attacks. These perpetrators, capitalizing...
A sophisticated variant of StrelaStealer malware, tailored for Spanish-speaking users, is targeting popular email clients Outlook and...
Microsoft has rolled out new tools in Azure AI Studio to aid generative AI app developers in...
Bitdefender has patched a vulnerability across its popular products like Internet Security, Antivirus Plus, Total Security, and...
In late March 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an alert concerning the...
Wireshark continues to reign supreme, providing unmatched tools for troubleshooting, analysis, development, and education. The latest release,...
Researchers have revealed a vulnerability in Apple Silicon processors called GoFetch, enabling attackers to extract secret keys...
Apple users are being targeted by a sophisticated phishing campaign aimed at seizing control of their Apple...
Originally focused on Latin America, the banking trojan Mispadu has broadened its scope to Europe, employing phishing...
Security specialists have unearthed a group of Android VPN apps that surreptitiously convert user devices into proxy...
Cybercriminals leverage 2FA (Two-Factor Authentication) phishing kits to bypass the added security layer provided by 2FA. These...
A malvertising campaign distributing a fake PuTTY client has been discovered, aiming to deploy the dangerous Rhadamanthys...
Mozilla has swiftly responded to two zero-day vulnerabilities exploited during the recent Pwn2Own Vancouver 2024 hacking contest...
First identified in 2020, the Sysrv botnet leverages a Golang worm to infect devices, deploying cryptominers through...
Over 170,000 users have been affected by a sophisticated attack targeting the Python software supply chain. The...
Security researchers have discovered a sophisticated method, named “DHCP Coerce,” that exploits the Dynamic Host Configuration Protocol...
With the rise in digital device usage, personal data security has become increasingly important. Side-channel attacks exploit...
In April 2023, Microsoft announced a multi-year initiative to unify authenticated, user-facing Microsoft 365 apps and services...
AndroxGh0st targets Laravel applications, scanning and extracting login credentials for AWS and Twilio from .env files. AndroxGh0st,...
Researchers at Perception Point have discovered a new malware campaign dubbed PhantomBlu, which targets US organizations. The...
A PoC has been published for a critical RCE vulnerability found in Fortra’s FileCatalyst software. RCE Vulnerability...
A critical vulnerability was found in miniOrange’s Malware Scanner and Web Application Firewall plugins, allowing unauthenticated attackers...
Google has announced an upgrade to its Safe Browsing technology, enhancing Chrome users’ protection against phishing, malware,...
A vulnerability categorized as improper input validation was discovered in Zoom Clients for Windows, Zoom VDI Client...
Threat actors frequently target GitHub users because of the abundance of valuable code repositories and sensitive information...
Hackers are using weaponized LNK files to deploy AutoIt malware, causing concern in the cybersecurity community. The...
A new tool discovered on the Dark Web indicates a change in cybercriminal tactics for illicitly accessing...
PixPirate, an Android banking malware, is pioneering stealth techniques to evade detection. IBM Trusteer researchers have unveiled...
A recent email spam campaign is distributing infostealer malware disguised as an Adobe Reader Installer. The spam...
In addition to ChatGPT and Gemini AI, two of the most popular publicly available Artificial Intelligence systems,...
The cybercriminal group BianLian, recognized for their ransomware assaults, has garnered attention from the information security community....
Vulnerability in Over 150,000 Fortinet Devices Enables Remote Execution of Arbitrary Code by Hackers


Vulnerability in Over 150,000 Fortinet Devices Enables Remote Execution of Arbitrary Code by Hackers
A critical security flaw, identified as CVE-2024-21762, has been uncovered in Fortinet’s FortiOS and FortiProxy secure web...
PUA:Win32/Softcnapp is a generic detection name used by Microsoft Defender to identify unwanted programs. It can occasionally...
CHAVECLOAK is a type of malware, specifically a banking trojan, known for targeting users, particularly in Brazil,...
GitLab has released updated versions for its Community Edition (CE) and Enterprise Edition (EE) platforms, addressing critical...
The malicious actor, known as “z0miner,” has been discovered targeting Korean WebLogic servers to disseminate various forms...
Two zero-day vulnerabilities have been uncovered in iOS and iPadOS 17.4 versions, enabling threat actors to circumvent...
Malware leverages the Notepad service to target systems like Windows and Linux, exploiting the ubiquity of Notepad...
Two fresh security vulnerabilities have surfaced in JetBrains TeamCity On-Premises, a prevalent CI/CD solution. Designated as CVE-2024-27198...
A recently identified DNS threat actor known as Savvy Seahorse is employing advanced tactics to lure victims...
The pandemic has spurred significant shifts in business models. With the rise of digital transformation, increased efficiency,...
A new Linux variant of Bifrost, called Bifrose, was detected employing a clever evasion tactic by utilizing...
A newly discovered phishing kit has been observed impersonating the login pages of prominent cryptocurrency services as...
Cybercriminals are leveraging the flexibility of SVG (Scalable Vector Graphics) files for the dissemination of the GUloader...
Cyber adversaries utilize ZIP files as a means to weaponize them, leveraging the ease of concealing malicious...
Recent discoveries by Phylum indicate that a series of counterfeit npm packages identified on the Node.js repository...
Threat actors exploit SSH credentials to gain unauthorized access to systems and networks, executing malicious activities by...
Researchers at Patchstack have issued a warning regarding an unauthenticated site-wide stored XSS vulnerability, identified as CVE-2023-40000,...
A newly identified, sophisticated malware coded in C# has emerged. Dubbed Xeno RAT, this malware boasts advanced...
Researchers uncovered an advanced cyberattack involving a dormant Python Package Index (PyPI) package called Django-log-tracker, which was...
The narrative surrounding the takedown of the LockBit ransomware on February 19 is still evolving. Following nearly...
Microsoft has commenced testing Wi-Fi 7 compatibility within the Windows 11 Insider Preview Build 26063. Initially available...
Information has surfaced regarding a recently patched high-severity security vulnerability in Apple’s Shortcuts app, allowing a shortcut...
Five vulnerabilities have been discovered within the Joomla content management system that could be exploited to execute...
MrB ransomware, a variant of Dharma ransomware, was identified on February 21, 2024. It encrypts files with...
Two recently discovered Wi-Fi authentication bypass vulnerabilities in open-source software could potentially expose numerous enterprise and home...
ConnectWise has remedied a critical vulnerability rated CVSS 10 in its ScreenConnect product, a desktop and mobile...
A recent malware campaign has been detected, focusing on gaining initial access through Redis servers, aiming to...
Cybersecurity experts have uncovered a critical vulnerability in the decentralized social network Mastodon, potentially enabling unauthorized access...
Meta Platforms announced it has taken measures to combat malicious activities originating from eight firms in Italy,...
SYSDF is a ransomware program belonging to the Dharma malware family. Typically targeting small businesses, it encrypts...
“A recent report by Trustwave SpiderLabs reveals the emergence of Ov3r_Stealer, a Windows malware propagated through deceptive...
Security researchers have uncovered a critical vulnerability in Shim, a commonly used Linux bootloader. This flaw has...
Zoom, the well-known video conferencing platform, recently patched 7 security vulnerabilities in a recent update. These vulnerabilities...
The public release of ChatGPT caused a sensation back in 2022, and it’s fair to say it’s...
The HijackLoader malware has incorporated additional defense evasion tactics. Increasingly, other threat actors are leveraging this malware...
Fortinet has issued a warning regarding a critical vulnerability found in its FortiOS SSL VPN system, which...
In a recent security update, GitLab has released a patch addressing a critical vulnerability that could permit...
The Cybersecurity and Infrastructure Security Agency has identified a security flaw in Apple operating systems, specifically iOS...
A recently discovered ransomware, named “Kasseika,” employs Bring Your Own Vulnerable Driver tactics to incapacitate antivirus software...
Fortra has revealed a critical vulnerability in its GoAnywhere MFT (Managed File Transfer) software—an authentication bypass that...
Apple has issued security updates to tackle the first zero-day vulnerability of the year, which has been...
Security researchers recently discovered two new malicious packages on the npm open source package manager. These packages...
CISA has set a deadline of one to three weeks for addressing three vulnerabilities associated with Citrix...
Cybersecurity researchers caution about a significant rise in threat actor activity exploiting a recently patched flaw in...
An ASEC investigation has uncovered the latest tactics employed by the notorious LockBit ransomware. Under the guise...
A recently launched campaign aimed at vulnerable Docker services installs both an XMRig miner and the 9hits...
Recent research reveals a substantial number of vulnerable SonicWall firewall instances susceptible to remote code execution (RCE)...
Atlassian recommends that its customers update their Confluence Data Center and Server to safeguard against the exploitation...
Cybersecurity experts have rediscovered the eight-year-old Azorult malware, known for stealing information and harvesting sensitive data. The...
In the latest release notes, Google discloses a newly discovered 0-day vulnerability already being exploited in the...
In recent years, zero-day exploits and attacks have emerged as prominent threats. Leveraging unknown vulnerabilities within software,...
On January 11, 2024, GitLab issued an update containing a crucial security fix for a vulnerability. This...
The malicious campaign leverages the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen to propagate Phemedrone Stealer. Employing...
SentinelOne’s malware hunters flagged a recently uncovered Python-based hacking tool employed by cybercriminals to hijack cloud platforms...
Cisco has successfully addressed a high-severity security vulnerability in Unity Connection. This flaw had the potential to...
On Wednesday, cybersecurity researchers at Volexity issued a warning, revealing that suspected Chinese nation-state hackers are currently...
In 2023, the threat actor known as Water Curupira has been actively disseminating the PikaBot loader malware...
Two vulnerabilities in Adobe ColdFusion have been targeted in real-world attacks, as cautioned by the Cybersecurity &...
An innovative SMTP Smuggling technique has been reported with the capability to circumvent current security protocols. Additionally,...
Ivanti has resolved a critical vulnerability in its Endpoint Manager (EPM) solution, designated as CVE-2023-39336, carrying a...
Security researchers have delved into the intricacies of SpectralBlur, an emerging macOS backdoor believed to be associated...
Fortinet researchers identified three malicious packages in the PyPI repository—modularseven, driftme, and catme. These packages, attributed to...
In a recent alert, the Cybersecurity and Infrastructure Security Agency (CISA) highlighted that Juniper has issued security...
A purportedly new method allows hackers to exploit the OAuth2 authorization protocol to compromise Google accounts. This...
Microsoft has disabled the MSIX installer protocol in Windows in response to its exploitation in real-world cyberattacks....
A recent Unit 42 investigation uncovered a dual privilege escalation chain affecting Google Kubernetes Engine (GKE). Stemming...
Researchers uncovered a novel Android backdoor named Xamalicious at the end of 2023. This malware demonstrates significant...
The digital landscape is witnessing a rise in sophisticated ransomware attacks, specifically remote encryption attacks. While the...
A recently identified phishing campaign is using decoy Microsoft Word documents as a lure to deploy a...
Scammers exploit a feature of Twitter posts, deceiving users and putting digital assets at risk. This deceptive...
Google has issued emergency updates to address yet another Chrome zero-day vulnerability that has been actively exploited...
In the course of a security assessment of its game development studios, Microsoft identified four vulnerabilities in...
Comcast has officially acknowledged a significant security breach affecting its Xfinity division, with approximately 36 million customers...
Kinsta, a leading WordPress hosting provider, has alerted its customers to a troubling cybersecurity development. Cybercriminals are...
QakBot malware has re-emerged in phishing campaigns, following a disruption of the botnet by law enforcement during...
FortiGuard unveiled security updates on December 12, 2023, to mitigate multiple critical vulnerabilities present in its FortiOS,...
On Thursday, Google declared its plans to initiate testing of a new feature named “Tracking Protection” from...
Security experts have uncovered a collection of 116 malicious packages within the Python Package Index (PyPI) repository,...
Google Emphasizes Clang Sanitizers in Strengthening Android’s Cellular Baseband Security and Mitigating Vulnerabilities What are Clang sanitizers?...
iOS 17.2 and iPadOS 17.2 have been launched by the company, featuring enhancements that resolve twelve security...
Researchers Uncover 21 New Sierra Vulnerabilities Affecting Over 86,000 Exposed Online Devices. Sierra AirLink Routers Users of...
COLDRIVER, the threat actor, persists in carrying out credential theft operations targeting entities strategically significant to Russia,...
Atlassian has issued software patches to rectify four critical vulnerabilities in its software. Successful exploitation of these...
Apple responded to the active exploitation of two zero-day vulnerabilities in the wild by swiftly issuing emergency...
There’s evidence of a CACTUS ransomware campaign exploiting recently revealed security vulnerabilities in Qlik Sense, a cloud...
Google has unveiled RETVec (Resilient and Efficient Text Vectorizer), a new multilingual text vectorizer designed to enhance...
The cybersecurity community has expressed concerns as they’ve detected exploitative activities focusing on ownCloud, leveraging the CVE-2023-49103...
Annually, the holiday season kicks off with the significant retail shopping events in the U.S., Black Friday...
SysJoker, a multi-platform malware, has been identified in a novel iteration, showcasing a comprehensive code overhaul implemented...
An alert has been released by CISA regarding several vulnerabilities affecting Adobe ColdFusion. The alert emphasizes that...
Phishing campaigns distributing malware families like DarkGate and PikaBot are employing tactics reminiscent of attacks associated with...
Successful management of cyber risks in small businesses centers on adherence to workplace regulations and the attainment...
Malicious cyber actors exploit MySQL servers through a botnet known as ‘Ddostf,’ utilizing it as a DDoS-as-a-Service...
Four distinct groups exploited a zero-day vulnerability in the Zimbra Collaboration email software in real-world attacks, aiming...
VMware has just released an advisory (VMSA-2023-0026) addressing a critical authentication bypass vulnerability found in the VMware...
Google Files Lawsuit Against Fraudsters Exploiting Bard’s Genetics Artificial Intelligence Hype to Deceptively Distribute Malware. Today, a...
The OracleIV botnet malware employs various strategies, with a central emphasis on executing DDoS attacks through floods...
A sub-cluster of the notorious Lazarus Group has created deceptive infrastructure mimicking skills assessment portals for inclusion...
Cybersecurity researchers have issued a warning about a Windows variant of a malware called BiBi-Windows Wiper. This...
The latest iteration of GootLoader malware, known as GootBot, enables lateral movement within compromised systems while successfully...
“Researchers Discover BlueNoroff RustBucket Malware Variant Targeting MacOS” – A recent report from Jamf Threat Labs sheds...
A recently emerged business offering a “Dropper-as-a-Service” (DaaS) known as “SecuriDropper” bypasses Android’s “Restricted Settings” function to...
The Mozi malware operation came to a sudden halt in August when an unidentified individual delivered a...
The hacking group known as Arid Viper (also identified as APT-C-23, Desert Falcon, or TAG-63) is purportedly...
Cybersecurity experts have discovered a fresh batch of malicious packages distributed through the NuGet package manager, employing...
A recent cyber campaign attributed to the Lazarus hackers from North Korea appears to have focused on...
A critical vulnerability, known as CVE-2023-46747, has been uncovered in F5 BIG-IP products, allowing unauthenticated remote code...
Safari Vulnerability Exposes Apple iPhones and Macs Powered by A and M-Series CPUs to Security Risks


Safari Vulnerability Exposes Apple iPhones and Macs Powered by A and M-Series CPUs to Security Risks
A team of researchers has developed an innovative side-channel attack called iLeakage, which takes advantage of a...
The backdoor infiltrated Cisco devices by exploiting two zero-day flaws in IOS XE software has been altered...
The TriangleDB implant, designed for infiltrating Apple iOS devices, incorporates four distinct modules: one for capturing audio...
Security researchers have uncovered three critical remote code execution (RCE) vulnerabilities within the SolarWinds Access Rights Manager...
Threat actors are currently exploiting critical vulnerabilities in Citrix NetScaler and WinRAR, posing a significant risk to...
Security researchers conducted an analysis of the Android trojan called SpyNote, revealing numerous spyware capabilities associated with...
Cybercriminals are increasingly employing counterfeit browser updates that imitate genuine notifications from Google Chrome, Mozilla Firefox, and...
His team at Patch Stack recently uncovered a fresh vulnerability in the WordPress plugin “User Submitted Posts,”...
Microsoft has unveiled a fresh bug bounty program that centers around enhancing the AI-powered Bing experience, offering...
In October 2023, Microsoft unveiled its latest Patch Tuesday, addressing a comprehensive 103 security vulnerabilities. Within this...
Google’s research team introduced the v8CTF, a capture-the-flag (CTF) challenge centered around the V8 JavaScript engine used...
The September 2023 Global Threat Index from Check Point cybersecurity researchers has unveiled notable shifts in the...
In the contemporary era dominated by technology and social media, email marketing continues to stand out as...
Online, proof-of-concept exploits have emerged for a critical vulnerability in GNU C Library’s dynamic loader, granting local...
Cisco has issued updates to rectify a critical security vulnerability affecting Emergency Responder, which permits unauthorized remote...
According to the “2023 State of the Threat” report by Her Secureworks, the number of victims reported...
A recent phishing campaign dubbed “EvilProxy” has come to light, with its sights set on the Microsoft...
The Lazarus hacking group, associated with North Korea, launched a cyberattack on a Spanish aerospace company by...
On Wednesday, Cisco issued a warning to its customers, urging them to address a zero-day vulnerability in...
The Android banking Trojan Zanubis has adopted a new disguise, posing as the official application of the...
Malicious actors are actively taking advantage of a critical vulnerability in Openfire messaging servers, using it to...
Researchers have exposed a robust clandestine ecosystem focused on crafting malware for IoT device exploitation. Researchers at...
A recently discovered malware variant named ZenRAT has surfaced, camouflaged within fraudulent Bitwarden installation bundles. ZenRAT Malware...
Researchers have uncovered a new distribution campaign for the Xenomorph malware, focusing on Android users in the...
A recently discovered backdoor malware, known as “Deadglyph,” has been detected in a cyberattack targeting a government...
Mobile malware, as its name implies, is specialized malicious software crafted specifically to infiltrate mobile devices such...
An imitation proof-of-concept (PoC) exploit targeting a WinRAR RCE vulnerability that was recently patched has been discovered...
Mastodon has taken action to resolve two vulnerabilities, specifically CVE-2023-42451 and CVE-2023-42452. Additionally, a zero-day vulnerability, denoted...
Google has confirmed that due to a recent court ruling, it is currently not possible to simultaneously...
XWorm is a recent addition to the remote access trojan family, quickly establishing itself as one of...
A recent analysis of the Android banking trojan Hook has uncovered its foundation in its predecessor, ERMAC....
An innovative cloud-native cryptojacking campaign has targeted lesser-known Amazon Web Services (AWS) offerings like AWS Amplify, AWS...
Researchers have recently uncovered a novel ransomware variant known as 3AM. Their inquiry unveiled that the initial...
The Free Download Manager website has been consistently redirecting Linux users to malware-infected destinations over an extended...
“The latest release, Notepad++ version 8.5.7, includes security updates to address several buffer overflow vulnerabilities identified in...
“HijackLoader, a recently emerged malware loader, is rapidly gaining popularity within the cybercriminal community for distributing a...
Secure Entry in Gmail is a crucial mode that enables users to safeguard against missing essential emails....
In recent updates, there have been emerging reports about threat actors associated with the Akira ransomware focusing...
A fresh malvertising campaign has come to light, disseminating an updated variant of macOS stealer malware known...
A recently updated variant of the Mirai botnet malware is now targeting Android TV set-top boxes, which...
The banking and logistics sectors are currently facing an assault from an updated version of malware known...
Google has released its monthly security patches for Android to tackle various vulnerabilities, one of which is...
“In the ongoing SocGholish infection chains, a revised BLISTER malware loader is now deployed to distribute Mythic,...
Based on a report from VIPRE, the use of malicious links in phishing emails reached 85%, and...
Today, LogicMonitor, a network monitoring company, confirmed that certain users of its SaaS platform have been impacted...
In the coming years, Signal’s applications became compromised, while Telegram, containing the BadBazaar spyware, was uploaded to...
A recently detected malspam campaign has been identified as distributing a readily available malware known as DarkGate....
Dubbed “Ransomed,” this group was initially identified by cybersecurity analyst and blogger Flashpoint on August 15th. The...
Within the realm of digital communication and collaboration, the Zimbra Collaboration Suite has long stood as a...
The ALPHV ransomware group, known as BlackCat, aims to intensify ransom payment pressure on victims by offering...
Cybersecurity analysts have revealed an intricate network of interconnected ransomware variants, all of which can be traced...
Since the beginning of August 2023, over twelve malicious packages have been found in the npm package...
“Cybersecurity experts at ESET reveal the discovery of a malevolent toolkit called Spacecolon, which has been utilized...
A fresh iteration of the XLoader malware targeting macOS disguises itself under the name ‘OfficeNote’ productivity application....
The Bronze Starlight hacking group has ingeniously employed a legitimate Ivacy VPN code-signing certificate to focus on...
A security vulnerability of significant severity has been revealed in the WinRAR utility, posing a potential risk...
A new iteration of the BlackCat ransomware was recently unveiled by Microsoft’s researchers. Termed ‘Sphynx’, this variant...
Malicious actors could exploit existing vulnerabilities within the PowerShell Gallery to execute supply chain attacks targeting users...
Two significant security flaws, designated as CVE-2023-32560, have been unearthed in Ivanti Avalanche. This enterprise mobility management...
Researchers from UC Irvine and Tsinghua University have created a potent cache poisoning attack named “MaginotDNS.” This...
Fortinet has raised an alert regarding the Gafgyt botnet malware, which is currently targeting a vulnerability in...
The amateur hacker group Lapsus$—mostly teenagers with limited technical training—has skillfully breached major targets like Microsoft, Okta,...
Microsoft introduces the August 2023 Patch Tuesday update, encompassing 87 security enhancements addressing 23 vulnerabilities. Among these...
Since June 4, 2023, an unidentified threat actor has been employing a Yashma ransomware variant to target...
As of late June 2023, the QakBot (aka QBot) malware operators have established 15 new command-and-control (C2)...
PaperCut NG and PaperCut MF are widely adopted software solutions for managing print services on servers. CVE-2023-39143...
Microsoft addressed a critical vulnerability in its Power Platform after criticism for a delayed response. Tenable reported...
IT professionals were targeted by a malicious package named “VMConnect,” which impersonated the VMware vSphere connector module...
Malicious apps employ sneaky versioning techniques to evade detection by Google Play Store scanners.


Malicious apps employ sneaky versioning techniques to evade detection by Google Play Store scanners.
Threat actors use versioning to bypass Google Play Store’s malware detection and target Android users. In its...
Palo Alto Networks Unit 42 found a new phishing campaign distributing a Python variant of NodeStealer. The...
The Chat GPT and other AI models have undergone numerous modifications to prevent malicious users from exploiting...
Cybercriminals are fabricating counterfeit websites containing software installers that have been infected with a downloader malware named...
The Flipper Zero team recently introduced “Flipper Apps,” its very own mobile app store. This new store...
The renowned WordPress form plugin, Ninja Forms, has been identified to have three vulnerabilities that might grant...
Lazarus, a state-backed North Korean hacker group, targets Windows Internet Information Service (IIS) web servers to use...
Azimuth Group, an Italian asset management company, oversees a substantial portfolio of over $87.2 billion in assets....
Wiz security researchers have revealed that Chinese hackers, known as Storm-0558, successfully stole Microsoft’s consumer signing key....
Estee Lauder has recently experienced a significant ransomware breach, joining the list of prominent companies targeted by...
New findings from Palo Alto Networks Unit 42 reveal that in 2023, Mallox ransomware activities have surged...
The cybersecurity landscape has been recently shaken by the emergence of BundleBot, a sophisticated malware strain that...
Adobe has addressed three vulnerabilities in ColdFusion, including a zero-day vulnerability. Adobe fixed three vulnerabilities in ColdFusion,...
Artificial Intelligence (AI) has introduced revolutionary advances, including generative AI, which shows great potential for creative use....
Microsoft and the Ukrainian CERT issued a warning about Russian state hacking group Turla launching new attacks....
Citrix ADC and Citrix Gateway, renowned for their role in facilitating secure application delivery and remote access...
AVrecon malware infects 70,000 Linux routers, forming a botnet for bandwidth theft and a hidden residential proxy...
The Computer Emergency Response Team (CERT-UA) of Ukraine has issued a warning regarding the rapid actions of...
Zimbra Collaboration Suite (ZCS) has issued an urgent advisory, urging administrators to apply a manual patch for...
A fake PoC about a Linux kernel vulnerability on GitHub exposed researchers to malware. A backdoor with...
The Triada malware infiltrates Android devices through a counterfeit Telegram app. Thankfully, the version of Telegram infected...
SonicWall has issued an urgent warning to its customers, urging them to promptly patch several critical vulnerabilities...
Today, Microsoft Corp. released software updates to address a total of 130 security vulnerabilities in its Windows...
Recently, a critical vulnerability was discovered in ShareFile, a cloud-based file sharing application. This vulnerability, identified as...
Progress is notifying customers about a newly discovered critical SQL injection vulnerability, identified as CVE-2023-36934, in its...
Rekoobe, a backdoor malware, specifically targets vulnerable Linux servers commonly utilized by the Chinese APT31. Rekoobe Malware...
The “TeamsPhisher” cybersecurity tool provides a means for both pen testers and malicious actors to send harmful...
Recent reports have brought to light crucial technical details regarding a critical vulnerability impacting various versions of...
A new version of the DDoSia attack tool has been released by the threat actors, featuring an...
A vulnerability found in the Ultimate Member plugin has the potential to exploit thousands of WordPress sites,...
The BlackCat ransomware group launched a malvertising campaign to push Cobalt Strike. They put up advertisements to...
Cybersecurity researchers recently uncovered a concerning discovery regarding a modified iteration of the widely-used messaging application, Telegram,...
Last year, the North Korean hacking group Andariel utilized a previously undisclosed malware named EarlyRat to carry...
Security researchers have recently discovered ThirdEye, an information stealer designed for Windows operating systems. This stealthy malware...
Cybersecurity experts have recently disclosed the intricate workings of Fluhorse, an Android malware family. The malware “represents...
Akira, a ransomware operation, has recently shifted its focus from Windows systems to VMware ESXi virtual machines,...
Arcserve has recently launched a security update to resolve a severe authentication bypass vulnerability known as CVE-2023-26258,...
A trojanized installer for the popular Super Mario 3: Mario Forever game for Windows has been discovered,...
The BIND 9 DNS software suite, an integral part of the Domain Name System (DNS), has recently...
A new strain of the JavaScript dropper has been observed delivering next-stage payloads such as Bumblebee and...
Cybersecurity researchers have recently informed that a vulnerability in the latest version of Microsoft Teams allows attackers to inject...
The Chinese hackers which are tracked as APT15 are involved in a new campaign that uses a backdoor with the name “Graphican“. The...
ESET researchers have identified an updated version of Android GravityRAT spyware being distributed as the messaging apps...
More than 101.000 ChatGPT user accounts have been stolen by infostealer malware over the past year, according...
Security researchers warn that malware developers are adopting a handy obfuscation tool to get malware past antiviruses....
Cybersecurity scams continue to be on the rise. As scammers get smarter, it’s important to stay up...
Zyxel has released firmware patches for a critical vulnerability (CVE-2023-27992) in some of its consumer network attached storage (NAS)...
A new stealer malware is on the rise, designed to obtain user credentials to help attackers penetrate...
The principle of least privilege (POLP), also named the “principle of least authority” (POLA) or “the principle...
Diicot shares its new name with the Romanian anti-terrorist police unit and uses the same style of...
Researchers detected fake company accounts on GitHub linked to a deceitful cybersecurity company. These accounts are promoting harmful...
Russia-linked state-sponsored cyber-espionage group Gamaredon (Armageddon, UAC-0010) continues its relentless attacks against government entities, and organizations in...
A new Golang-based information stealer called Skuld has compromised Windows systems across Europe, Southeast Asia, and the U.S. What...
A fully undetectable (FUD) malware obfuscation engine called BatCloak has been used to deploy various malwastrains since...
Fortinet has patched a critical flaw in its Fortigate devices, with admins urged to apply firmware updates...
Gmail is tightening its implementation of an email security protocol after a researcher discovered a flaw allowing...
Cisco has recently fixed a high-severity vulnerability found in its Cisco Secure Client (previously known as AnyConnect...
A new PowerShell malware script, named “PowerDrop”, has been discovered to be used in attacks targeting the...
A recent malware campaign has been discovered that exploits the Satacom downloader as a means to deploy...
The Cyclops group has developed multi-platform ransomware that can infect Windows, Linux, and macOS systems. The Cyclops...
TrueBot downloader trojan botnet activity has increased significantly in the past month, researchers say. What is TrueBot?...
Yesterday, Google addressed another zero-day vulnerability affecting Google Chrome. The Flashpoint Intel Team quickly published an alert to VulnDB customers and...
The popular and one of the most-used WordPress plugins, Jetpack recently addressed a critical security issue. Despite...
Cybersecurity firm Eclypsium has uncovered a potential backdoor in Gigabyte systems, raising concerns about the security of the technology...
A critical vulnerability in Progress Software’s MoveIt Transfer is under exploitation, according to a report from Rapid7....
A technical write-up for a ReportLab vulnerability are now available. The vulnerability tracked as CVE-2023-33733. Recently, during an audit of...
ChatGPT (generative pre-trained transformer) is an AI-powered chatbot created by Open AI and designed to produce human-like text...
An open-source Android virus known as DogeRAT (Remote Access Trojan) has been discovered by CloudSEK, an AI cybersecurity company. The malware...
A new Android malware – SpinOk – distributed as an advertisement SDK has been discovered in several...
D-Link has fixed two critical vulnerabilities in the D-View 8 network management suite that could allow remote...
Zyxell has released a security advisory for multiple buffer overflow vulnerabilities. Exploitation of these vulnerabilities could allow an unauthenticated...
Security professionals warn that Google’s new top-level domains, .zip and .mov, pose social engineering risks while providing...
Luxottica, the world’s largest eyewear company, has revealed that it was the victim of a major cyber attack....
Researchers have been tracking a financially motivated threat group known as GUI-vil (aka p0-LUCR-1), based in Indonesia, which...
Research has revealed how the Russian gang’s malware remains hidden in systems and gets around end-point security....
A proof-of-concept (PoC) has been made available for a security flaw in the KeePass password manager that...
Malicious actors frequently resort to alternative techniques to gain initial access, such as employing diverse file formats...
Apple announced that it will make available new important “Accessibility functions“At iOS 17 that will be released this year, and...
The threat actors behind the CopperStealer malware re-emerged in March and April 2023 with two new campaigns...
Top streaming service Discord has suffered a minor cybersecurity incident in which potentially sensitive and personal user...
WordPress plugins allow organizations to quickly extend the functionality of their websites without requiring any coding or...
New samples of it RapperBot botnet malware, reviewed by experts security, they have added cryptomining capabilities to mine cryptocurrency from hacked...
Hackers have been detected breaking into popular verified Facebook pages and using them to run ads on...
A Phishing-as-a-Service (PhaaS) platform called “Greatness” has seen a spike in activity as it targets organizations using...
Shopping cart malware, known as Magecart, is still one of the most popular tools in the attacker’s...
Based on the Computer Emergency Response Team of Ukraine (CERT-UA), the SmokeLoader malware is now being spread...
A new Android malware named “FluHorse” has been discovered, targeting users in East Asia with malicious apps...
The KEKW malware employs a malicious function known as system_information() to gather a wide range of system-related...
Cisco SPA112 2-Port Phone Adapters have been reported to be vulnerable to arbitrary code execution via a malicious firmware...
A novel ransomware strain dubbed ‘Cactus’ has been found to be exploiting vulnerabilities in Fortinet VPN devices to gain...
Sandworm (UAC-0165), a Russian hacking group, has been linked to an attack on Ukrainian state networks that...
The Windows Known Issue Email Alerts is a new feature recently introduced. The Email Alerts for Windows...
The North Korean threat actor known as APT37 has been observed changing deployment methods and using South...
Cybersecurity researchers have discovered a new malware, called ‘LOBSHOT,’ distributed through Google ads. What is LOBSHOT Malware...
A recent ‘malverposting’ campaign linked to a Vietnamese threat actor has been ongoing for months and is estimated...
Git and GitHub are essential tools for developers. However, the learning curve to adapting git version control...
Recently, the cybersecurity researchers at Cyble discovered a new macOS malware, ‘Atomic’ (aka ‘AMOS’), sold for $1,000/month...
RTM Locker ransomware-as-a-service operators have now turned their attention to Linux, network-attached storage devices and ESXi hosts....
Microsoft has recently revealed that the Clop and LockBit ransomware gangs are responsible for the attacks on...
To address zero-day vulnerabilities that might be used to achieve code execution on computers using unpatched versions...
Evasive Panda’s malicious campaign uses the update channels of legitimate Chinese applications to deliver their infamous backdoor,...
An AI-powered code analysis feature was recently launched by VirusTotal, dubbed “Code Insight.” Google Cloud Security AI Workbench’s...
Yellow Pages Group, a Canadian directory publisher has confirmed to BleepingComputer that it has been hit by...
The Service Location Protocol (SLP) is intended to allow the automated discovery of shared services within a...
The ‘Decoy Dog’ malware toolkit, aimed at enterprises, was uncovered recently by the security analysts at Infoblox...
The bumblebee malware, first spotted last year targeting enterprise users is now distributed via SEO poisoning and Google Ads, which...
The attack tool known as Evil Extractor and developed by a company called Kodex as an “educational...
Researchers at MalwareHunterTeam uncovered a ZIP archive on VirusTotal that was found to contain encryptors for devices...
Researchers are seeing a “significant increase” in attacks deploying the Qakbot malware, which have targeted victims in...
WhatsApp has announced several new security features which include an extra check when an account is transferred to a...
After a few early developer previews, the Android 14 Beta program has officially arrived. Here’s how to...
The Kyocera Android print app is vulnerable to unauthorized manipulation, providing malicious applications the opportunity to download and potentially...
Hackers are once again using fake Google Chrome updates as means to infect unsuspecting users with malware....
Apple just issued a short, sharp series of security fixes for Macs, iPhones and iPads. The following...
Microsoft has released another set of security updates to fix a total of 97 flaws impacting its...
The most important of the new notes deals with two critical vulnerabilities in SAP Diagnostics Agent that...
A cyber attack campaign targeting WordPress websites has recently caused significant concern, with experts estimating that up to one...
An up-and-coming cybercrime group, FusionCore, is likely composed of English-speaking European teenagers with distinct skills. All about...
Researchers discovered a new malware that fakes legitimate Google Drive extensions to inject malicious scripts and steal...
Mandiant has identified a new affiliate of ALPHV (BlackCat ransomware), identified as UNC4466, that targets publicly exposed...
Portuguese users should be wary of CryptoClippy, a new form of malware targeting them in a malvertising...
A sophisticated and fast ransomware family, dubbed Rorschach, has emerged in the threat landscape. The ransomware was...
Threat actors exploit WinRAR self-extracting (SFX) archives containing decoy files by adding malicious functionality to install backdoors in target...
A recently discovered comprehensive toolset dubbed AlienFox toolkit is circulating on Telegram. It’s a modular set of...
QNAP, a manufacturer of network-attached storage (NAS) systems, issued a warning to its users regarding a critical...
Recently, cybersecurity company Wiz discovered a misconfiguration issue in Azure Active Directory (AAD) that resulted in unauthorized access to...
The malware may be linked to another state-sponsored APT group called Earth Berberoka (or GamblingPuppet), which mainly...
New IcedID variants found without the usual bank fraud feature. Instead, they appear to be aiming to...
Online transactions ease our daily lives but also pose a serious risk to both businesses and their...
A new Phishing campaign based on legitimate servers from the Microsoft SharePoint platform aims at least 1600 people throughout the Europe, the USA and other...
The recently evolved version of Nexus has targeted more than 450 banks and cryptocurrency services. Multiple threat...
Cybercriminals have been observed abusing Adobe’s Acrobat Sign service to deliver emails leading to a RedLine stealer...
Researchers have discovered a new DDoS botnet capable of launching attacks with data volumes reaching several Tbps....
SAP has recently fixed 19 vulnerabilities as part of its March 2023 patch day. Five vulnerabilities are rated critical...
A new Android vishing (voice phishing) malware tool called “FakeCalls” has been detected targeting victims in South...
A piece of malware designed to load Cobalt Strike beacons onto victim machines has been traced back...
Microsoft fixed zero-day vulnerability that malicious actors were exploiting to bypass its anti-malware service windows smart screen based on cloud and...
A recently identified Golang-based botnet is targeting web servers running FTP, MySQL, phpMyAdmin, and Postgres services, Palo...
The gang behind it Clop ransomware has begun extorting companies whose data were stolen thanks to the use of a zero-day...
A new version of the Xenomorph Android malware has been released with increased malicious capabilities, such as...
A PoC exploit for CVE-2023-21716, a critical RCE vulnerability in Microsoft Word that can be exploited when...
Google is announcing more features that are being expanded to include all Google One subscribers. What is...
Successful compromises by the notorious Emotet malware are occurring again. After several months of inactivity, the botnet...
Cybersecurity scams continue to be on the rise. As scammers get smarter, it’s important to stay up...
Apple is in the process of being finalized iOS 16.4 for its official public release this spring! If all goes...
Google has announced a slew of new features for Android, Chromebook and Wear OS that are designed to improve...
An international law enforcement operation has led to the arrests of suspected core members of the prolific...
Aruba Networks has issued a security advisory addressing six critical vulnerabilities that exist in various versions of...
Cybersecurity company Bitdefender has recently announced the release of a new decryptor for the MortalKombat ransomware. The decryptor...
Exfiltrator-22 is a new post-exploitation kit that can spread ransomware undetected. Researchers speculate that the creators of...
Two critical severity vulnerabilities in the Houzez theme and plugin for WordPress are actively being exploited to...
The Cyber Research and Intelligence Labs have recently identified a novel malware variant known as the “White...
A new threat actor has been seen targeting shipping companies and medical laboratories in Asia with phishing...
VMware has fixed a critical vulnerability (CVE-2023-20858) in Carbon Black App Control, its enterprise solution for preventing...
Security researchers have released a proof-of-concept exploit for a critical vulnerability (CVE-2022-39952) in Fortinet’s FortiNAC network access...
A new information stealer advertised as “Stealc” has been discovered by Sekoia researchers. Security researchers at cyber threat intelligence company...
A sneaky cyber attack has recently surfaced with the aim of deceiving Coinbase employees through fake SMS...
GoDaddy, a web hosting company, has disclosed that during a multi-year period, hackers broke into its systems,...
WordPress is an immensely popular content management system (CMS) powering over 43% of all websites. Many webmasters...
ProxyShellMiner is being distributed to Windows endpoints by a very elusive malware operation, according to Morphisec. ProxyshellMiner...
Cloudflare stated that it had managed to mitigate multiple “hyper-volumetric” DDoS attacks that originated from more than...
Microsoft released it Patch Tuesday for February 2023 correcting over 75 security vulnerabilities, which include all three zero-day bugsthat have been used...
RedEyes Hacking Group (aka APT37), a threat group known for its cyber espionage activities, has recently adopted...
Hackers running a new financially motivated campaign are using a variant of the Xortist ransomware called ‘MortalKombat’,...
Social engineering has been an observable phenomenon since the beginning of history. People with something to gain...
Five malicious packages were found on the Python Package Index (PyPI), stealing passwords, Discord authentication cookies, and...
A vulnerability addressed by the latest update for Apache Kafka is an unsafe Java deserialization issue that could be...
Cl0p has been one of the most active ransomware families over the past several years, targeting numerous...
The vulnerability, tracked as CVE-2021-21974, is caused by a stack overflow issue in the OpenSLP service that unauthenticated threat actors...
The Clop ransomware operation now also uses a variant of the malware that only targets Linux servers,...
Google Fi, Google’s U.S.-only telecommunications and mobile internet service, has notified customers that personal data was exposed...
Since September 2021, over a thousand vulnerable Redis servers online have been infected by a stealthy malware dubbed “HeadCrab”,...
Hackers have been targeting online gaming and gambling companies with what appears to be a previously unseen...
A new exploit called ‘Sh1mmer’ can be used to “unenrolling” enterprise-managed Chromebooks to install apps and bypass...
Palo Alto Networks warns of an increase in cyberattacks targeting CVE-2021-35394, a remote code execution (RCE) vulnerability...
The threat actor has dumped a whopping 44.7 GB worth of Yandex data, including its source code...
VMware addresses multiple vulnerabilities, including two rated as critical, in the vRealize Log Insight product. The vRealize...
Researchers discovered an RCE vulnerability in Microsoft Teams during Pwn2Own 2022. The application is used by a wide range...
A suspected China-nexus threat actor exploited a recently patched vulnerability in Fortinet FortiOS SSL-VPN as a zero-day...
Two new vulnerabilities have been found in the Galaxy App Store application allowing local attackers to install...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released several Industrial Control Systems (ICS) advisories warning of critical...
Netlab recently released a report confirming that this sample was adapted from the leaked Hive project server...
Software development service CircleCI has revealed that a recently disclosed data breach was the result of information...
Operators of the StrRAT and Ratty distant entry trojans (RAT) are operating a brand new marketing campaign...
Open-source, web-based network monitoring and graphing tool Cacti received an update recently to fix a critical-severity security vulnerability that enabled executing...
Windows 7 Professional and Enterprise editions will no longer receive extended security updates for critical and important...
Organisations that fell victim to Andromeda, a commodity malware that dates back 12 years, seem to be at...
South African threat actors known as ‘Automated Libra’ has been improving their techniques to make a profit...
“Taiwan-based NAS maker Synology has addressed a maximum (10/10) severity vulnerability affecting routers configured to run as...
Hackers are actively exploiting a critical vulnerability, tracked as CVE-2022-45359 (CVSS v3: 9.8), affecting the WordPress plugin YITH WooCommerce...
The PyTorch team has issued a warning to users who installed PyTorch-nightly over the holidays, advising them...
Two critical vulnerabilities tracked as CVE-2022-27510 and CVE-2022-27518 still affect thousands of Citrix Application Delivery Controller (ADC)...
In July 2022, Microsoft made a crucial development to its Office software that blocks macros in Office...
A critical remote code execution vulnerability (CVE-2022-47939) has been identified in the ksmbd module of the Linux kernel. This...
PrivateLoader is an active malware in the loader market, used by multiple threat actors to deliver various payloads,...
Cybersecurity researchers exposed new evasion techniques adopted by an advanced malware downloader called GuLoader. GuLoader malware GuLoader is a first-stage trojan designed...
The vulnerability could let attackers introduce malicious code into cloud production environments. Kyverno’s admission controller offers a signature verification...
SentinelLabs disclosed that the Vice Society group has adopted a new custom-branded ransomware payload in recent intrusions,...
LastPass has confirmed that cybercriminals stole its customers’ encrypted password vaults, which store its customers’ passwords and...
Reports says, the zero-day vulnerabilities CVE-2022-41040 and CVE-2022-41082, dubbed ProxyNotShell, are still being actively exploited. ProxyNotShell vulnerabilities are exploited by...
Researchers at Trend Micro have been tracking Raspberry Robin since September and are warning the worm is...
The threat actors behind the Windows banking malware known as Casbaneiro has been attributed as behind a novel Android...
Cybersecurity researchers at ReversingLabs have discovered a new malicious package, named ‘SentinelOne,’ on the Python Package Index...
Apple has confirmed that an iPhone software update it released two weeks ago fixed a zero-day security...
A critical remote code execution vulnerability has been discovered in the SPNEGO (Simple and Protected GSS-API Negotiation...
Microsoft on Tuesday released patches for 48 vulnerabilities in seven Microsoft product families. This includes 6 Critical-class...
Fortinet has released a patch for a critical zero-day security vulnerability affecting its FortiOS SSL-VPN product. The vulnerability could lead to remote...
Security flaw has been disclosed in Amazon Elastic Container Registry (ECR) Public Gallery that could have been...
Research team has found three different vulnerabilities in the MegaRAC Baseboard Management Controller (BMC) software. CVE-2022-40259 and CVE-2022-40242 vulnerabilities have CVSS...
A cryptocurrency mining attack targeting the Linux operating system also involved the use of an open source...
Secureworks Counter Threat Unit (CTU) researchers are investigating the Drokbk malware, which is operated by a subgroup...
Researchers have shed mild on a new hybrid malware campaign targeting the two Android and Windows running...
Lazarus hacking group spreads malware using a fake cryptocurrency app called BloxHolder. This made-up brand pretends to...
Zerobot has been observed in the wild proliferating by taking advantage of nearly two dozen security vulnerabilities in...
A critical stack-based buffer overflow bug, tracked as CVE-2022-23093, in the ping service can allow to take over FreeBSD...
GoTo, maker of the popular virtual meeting and desktop-sharing software, and its affiliate LastPass confirmed on Wednesday...
Password manager LastPass has told customers that some of their information has been accessed in a cybersecurity...
Google researchers said on Wednesday they have linked a Barcelona, Spain-based IT company to the sale of...
ManageEngine recently patched a SQL injection vulnerability bug in their Password Manager Pro, PAM360, and Access Manager...
A Spanish company that offers “tailor made Information Security Solutions” may have exploited vulnerabilities in Chrome, Firefox...
Microsoft already released the big Windows 11 update for the year, 22H2, but the company isn’t slowing...
Hackers are always coming up with clever ways to exploit the latest trends, and the latest example...
Researchers from security company Datadog discovered a cross-tenant vulnerability in a popular Amazon Web Services (AWS) tool, which Amazon...
Google has released an important update to Chrome web browser that fixes another zero-day vulnerability. CVE-2022-413 The...
The latest WhatsApp data leak has reportedly affected as many as 80 countries, including Russia, Italy, Egypt,...
Researchers at SEKOIA identified 7 traffers teams on Dark Web forums that announced the availability of the...
A Vietnam-based hacking operation dubbed “Ducktail” is targeting individuals and companies operating on Facebook’s Ads and Business...
A Google Chrome extension named “VenomSoftX” is being used to steal cryptocurrency from wallets and breach passwords. The malware has...
Security researchers have warned of a new ransomware variant that not only encrypts the victim’s files but...
The Emotet malware-delivery botnet is back after a short hiatus, quickly ramping up the number of malicious...
Security researchers have uncovered a sophisticated phishing campaign using tens of thousands of malicious domains to spread...
North Korea-linked APT Lazarus is using a new version of the DTrack backdoor to attack organizations in Europe and...
The vulnerability CVE-2022-41622 makes BIG-IP and BIG-IQ vulnerable to unauthenticated remote code execution (RCE) via cross-site request forgery due to Big-IP’s SOAP API...
A critical unauthenticated remote code execution vulnerability in Spotify’s Backstage project has been found and fixed, and...
Microsoft on Sunday reported that after installing updates released on the most recent Patch Tuesday on Nov....
Security researchers have spotted an intriguing malware campaign designed to increase the search engine rankings of spam websites...
A new APT group, Earth Longzhi, reportedly targeted organizations in East Asia, Southeast Asia, and Ukraine using...
Trend Micro researchers observed an uptick in attacks targeting bank customers in India, the common entry point...
A new web3 technology is being abused widely by threat actors, according to security researchers from tech...
Microsoft November 2022 Patch Tuesday has been released with patches for a total of 68 vulnerabilities, which...
Threat actors have developed a new approach to deceive cryptocurrency users. They are using Laplas Clipper, a...
Sensitive URLs to shared documents, password reset pages, team invites, payment invoices and more are publicly listed...
A phishing-as-a-service (PhaaS) platform known as Robin Banks has relocated its attack infrastructure to DDoS-Guard, a Russian provider of...
A new analysis of tools put to use by the Black Basta ransomware operation has identified ties...
OpenSSL released patches for two vulnerabilities that have caused widespread concern among cybersecurity experts and researchers over...
File-hosting company Dropbox revealed on Tuesday that it has suffered a phishing incident. Attackers took 130 code repositories using...
The malicious program operators have been silent for five months and have now again started to spam...
Callback phishing emerged as a hybrid social engineering technique that combines phishing and vishing. The phishing technique used to...
Researchers have discovered a new version of the Fodcha DDoS botnet, featuring upgrades to deter analysis by...
A free unofficial patch is available for a Mark-of-the-web (MoTW) security vulnerability impacting Windows 10 and 11,...
Google has announced an update for Chrome issues that fixes an in-the-wild exploit. Mitigation for chrome issues If you’re...
U.S. officials have charged a Ukrainian national over his alleged role in the Raccoon Infostealer malware-as-a-service operation...
Microsoft has discovered recent activity that links the Raspberry Robin worm to human-operated ransomware attacks. The experts noticed that...
Despite the release of Windows 11 this early October, there have been updates for Windows 10, still....
Apple on Monday disclosed and patched a kernel-level zero-day vulnerability affecting many of its iOS devices. The...
The security expert Andreas Kellas detailed a high-severity vulnerability, tracked as CVE-2022-35737 (CVSS score: 7.5), in the...
SideWinder, a prolific nation-state actor mainly known for targeting Pakistan military entities, compromised the official website of...
Ursnif (a.k.a. Gozi), a former banking trojan, has been repurposed as a generic backdoor. Threat actors could use...
The Prestige ransomware first appeared in the threat landscape on October 11 in attacks occurring within an...
The malicious actors behind the relatively new Venus ransomware are hacking publicly exposed Remote Desktop Services to...
Telecommunications and IT company providers in the Middle East and Asia are currently being specific by a...
A beforehand undocumented command-and-manage (C2) framework dubbed Alchimist is most likely currently being used in the wild...
Aruba addressed multiple critical severity vulnerabilities in the EdgeConnect Enterprise Orchestrator that can be exploited by remote...
A critical vulnerability in vm2 might let a remote attacker bypass the sandbox environment and execute shell commands on the device...
Microsoft released fixes for a Windows zero-day and a publicly disclosed vulnerability on October Patch Tuesday but...
A brand new piece of analysis has detailed the more and more refined nature of the malware...
Zimbra-CVE-2022-41352 is an unpatched remote code execution vulnerability in Zimbra Collaboration Suite discovered in the wild due to active...
Zscaler researchers linked a recently discovered sample of a new malware called LilithBot to the Eternity group....
Security researchers have shared facts about a now-addressed security flaw in Apple’s macOS functioning technique that could...
The BlackByte ransomware gang is using a new technique that researchers are calling “Bring Your Own Driver,”...
A novel Android malware referred to as RatMilad has been observed concentrating on a Middle Jap business...
The recently learned Linux-Based ransomware pressure acknowledged as Cheerscrypt has been attributed to a Chinese cyber espionage...
Last week, Microsoft confirmed that two zero-day vulnerabilities in Microsoft Exchange recently disclosed by researchers at cybersecurity firm GTSC...
The North Korea-backed Lazarus Team has been observed deploying a Windows rootkit by taking gain of an...
On September 16, GitHub discovered phishing attacks by hackers impersonating CircleCI. During the attack, users are warned of session expiration and...
Security researchers have discovered a malicious campaign by the hacking group ‘Witchetty’, which uses steganography to hide...
A new, multi-functional Go-based malware dubbed Chaos has been rapidly growing in volume in recent months to ensnare a...
A cyberattack campaign, potentially bent on cyber espionage, is highlighting the increasingly sophisticated nature of cyberthreats targeting defense contractors...
Threat actors started utilizing PowerPoint presentations as a code execution method and delivering Graphite malware in targeted attacks. APT28...
Microsoft SQL servers are succumbing to FARGO ransomware, security researchers at AhnLab Security Emergency Response Center (ASEC)...
A China-linked cyberespionage group, tracked as TA413 (aka LuckyCat), is exploiting recently disclosed flaws in Sophos Firewall (CVE-2022-1040)...
BlackCat Ransomware attackers fine-tuning their malware arsenal in a bid to remain undercover and expand their reach. According...
The US Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical Java deserialisation bug affecting...
Microsoft on Thursday warned of a consumer-facing attack that made use of rogue OAuth applications on compromised...
Cybersecurity company Imperva has disclosed that it mitigated a dispersed denial-of-company (DDoS) attack with a whole of...
Cybersecurity firm Bitdefender published a new decryptor on Friday for LockerGoga, a strain of ransomware best known for...
The newly published GIFShell attack method, which occurs through Microsoft Teams, is a perfect example of how...
Trend Micro recently released a patch for an actively exploited flaw in its endpoint security platform, Apex One....
Password management solution LastPass shared more details pertaining to the security incident last month, disclosing that the...
Researchers believe that hackers with links to North Korean government have been pushing the Trojanized Version of...
Threat actors infected FishPig’s distribution server as part of a supply chain attack. The vendor’s service integrates Adobe’s...
A novel phishing campaign is underway, targeting Greeks with phishing sites that mimic the state’s official tax...
Emotet (also known as SpmTools) is a sophisticated, modular banking trojan. Emotetmostly serves as a downloader or dropper of other banking trojans....
Microsoft on Tuesday released fixes to eliminate 64 new security flaws across its software lineup, including a...
Apple iPhone, iPad, and Mac security update fixes actively exploited zero-day vulnerability, which allows hackers to carry...
The patches for a high-severity vulnerability in the binding configuration of SD-WAN vManage software containershas been announced...
Lampion malware operators use the free file-sharing platform WeTransfer to perform phishing attacks. This way, attackers can avoid security alerts...
A set of six high-severity firmware vulnerabilities impacting a broad range of HP Enterprise devices are still...
A zero-day flaw in a WordPress plugin known as BackupBuddy is being actively exploited, WordPress safety firm Wordfence has...
The North Korean state-sponsored crime ring Lazarus Group is behind a new cyberespionage campaign with the goal...
Cisco has released updates to address vulnerabilities affecting multiple products. The vulnerability, identified as CVE-2022-28199 (CVSS 8.6), is due to improper error handling...
Outdoor clothing giant The North Face has notified customers that their account may have been compromised, after noticing unusual...
The Lazarus Group, a well-known North Korean nation-state actor, has been connected to the MagicRAT remote access trojan....
A stealthy new form of malware is targeting Linux systems in attacks that can take full control...
The Taiwanese company QNAP cautions customers about DeadBolt ransomware attacks upon exploiting a zero-day vulnerability in Photo Station. QNAP detected the issue on...
A new Phishing-as-a-Service (PhaaS) named EvilProxy (also known as Moloch) was seen for sale in dark web forums,...
The information stealing and banking data-targeting Android malware was found installed with the help of applications masquerading...
A Vulnerability has been discovered in Atlassian Bitbucket Server and Data Center which could allow for remote...
Apple has released a new iOS 12 build for customers using the older models of iPhones, iPads...
Cybersecurity company Trend Micro is raising the alarm on a new ransomware family called Agenda, which has...
Google on Tuesday announced it’s launching a new bug bounty program that focuses specifically on open-source software. ...
The danger actor behind the SolarWinds source chain attack has been connected to still a further “extremely...
The threat actor behind the attacks on Twilio and Cloudflare earlier this month has been linked to...
Password management firm LastPass was hacked last week, allowing threat actors to steal the company’s source code...
Threat actors have begun to make use of the Tox peer-to-peer on the spot messaging service as...
Recently security experts from Sucuri, spotted JavaScript injections targeting WordPress sites to display fake DDoS Protection pages...
GitLab released patches where they fixed a critical remote code execution vulnerability. It is labeled CVE-2022-2884 with a CVSS score of...
Atlanta-based mostly cyber risk intelligence corporation, Cyble found out a new Remote Accessibility Trojan (RAT) malware. RAT...
Organizations in the Spanish-speaking nations of Mexico and Spain are in the crosshairs of a new campaign...
Apple has launched emergency safety updates at the moment to repair two zero-day vulnerabilities beforehand exploited by...
Windows users who have installed a new KB5012170 security update for Secure Boot have encountered various issues,...
A group of security researchers found a series of vulnerabilities in the software underlying popular apps like...
Reports from cybersecurity firms SEKOIA and Trend Micro confirm that a new effort by the Chinese threat actor Lucky Mouse involves...
Sova malware adds new features that make it more dangerous to a wider range of Android payment...
Threat actors are exploiting a vulnerability, tracked as CVE-2022-0028 a high severity issue in Palo Alto Networks devices running...
The US Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two disadvantages of it Catalog of known vulnerabilities in...
Cisco confirmed today that the Yanluowang ransomware group infiltrated its corporate network in late May and that...
The first-ever incident possibly linked to the ransomware family known as Maui occurred on April 15, 2021,...
Microsoft has released the Windows 11 KB5016629 cumulative update with security updates, improvements, including fixes for File...
Microsoft says that some of the Exchange Server flaws addressed as part of the August 2022 Patch...
The U.S. Cybersecurity and Infrastructure Security Agency has added two more flaws to its catalog of Known...
A new IoT botnet malware dubbed RapperBot has been noticed promptly evolving its capabilities because it was...
A new ransomware family called ‘GwisinLocker’ targets South Korean industrial and pharmaceutical companies. GwisinLocker ransomware ReversingLabs researchers...
Researchers at Trellix have discovered a critical unauthenticated remote code execution (RCE) vulnerability impacting 29 models of...
On Wednesday, Hackers attacks Russian organizations with the newly discovered malware, allowing them to take control and...
VMware on Tuesday released updates to address 10 security flaws affecting several products that could be used...
Threat actors are increasingly mimicking legitimate applications like Skype, Adobe Reader, and VLC Player as a means...
The operators of the Gootkit access-as-a-service (AaaS) malware have resurfaced with updated techniques to compromise unsuspecting victims....
A group of North Korean hackers is using a rogue Microsoft Edge or Chrome plugin to track or access user email...
The decentralized file system solution known as IPFS is becoming the new “hotbed” for hosting phishing sites,...
The team behind LibreOffice has released security updates to fix three security flaws in the productivity software,...
Risk actors are significantly abusing Internet Details Services (IIS) extensions to backdoor servers as a means of...
Cybersecurity researchers have reiterated similarities involving the hottest iteration of the LockBit ransomware and BlackMatter, a rebranded...
Recent Windows 11 builds come with the Account Lockout Policy policy enabled by default which will automatically...
An Israeli spyware outfit turned the actively exploited, but now patched, Google Chrome zero-day issue into a...
Microsoft announced today that it resumed the rollout of VBA macro auto-blocking in downloaded Office documents after temporarily...
A never ever-in advance of-observed Linux malware has been dubbed a “Swiss Military Knife” for its modular...
Atlassian has patched a crucial hardcoded credentials vulnerability in Confluence Server and Information Heart that would let...
Cybersecurity researchers have taken the wraps off a earlier undocumented spyware focusing on the Apple macOS working...
State-backed hackers part of Russia’s Federation Foreign Intelligence Service (SVR) have started using Google Drive legitimate cloud...
Researchers , have published a paper that demonstrates how a hacker could extract data from an otherwise...
Incident Response :Sensitive data and confidential information are the new gold in the digital age, and cyber...
Netwrix IT asset tracker and compliance auditor, used across more than 11,500 organizations, contains a critical Insecure...
Juniper Networks this week announced the release of patches for more than 30 vulnerabilities across its portfolio,...
The UEFI firmware used in several laptops made by Lenovo is vulnerable to three buffer overflow vulnerabilities...
AWS fixed three authentication bugs present in one line of code in its IAM Authenticator for Kubernetes,...
A new browser hijacker/adware campaign named ChromeLoader also known as Choziosi Loader and ChromeBack was discovered. Despite...
Microsoft on Monday announced the general availability of a feature called Autopatch that automatically keeps Windows and Office software...
New Checkmate ransomware has been discovered targeting QNAP NAS devices. Although the attacks are still being investigated, it is known that...
The operators of the TrickBot malware have resorted to systematically targeting Ukraine since the onset of the...
Researchers from Microsoft Security have spotted an upgraded version of the ransomware-as-a-service (RaaS) dubbed Hive. Hive Ransomware...
A new and entirely undetected Linux threat dubbed Orbit, signally a growing trend of malware attacks towards...
The ShadowServer foundation has recently released a report showing that there are about 3.6 million MySQL servers...
Researchers have uncovered a software supply-chain attack involving packages hosted on the Node Package Manager (npm), which...
Gitlab has patched a critical vulnerability that could allow an attacker to execute code remotely. The security issue, which...
Raspberry Robin is a Windows worm discovered by cybersecurity researchers from Red Canary, the malware propagates through removable...
The Jenkins security team announced 34 security vulnerabilities affecting 29 plugins for the Jenkins open-source automation server....
AstraLocker 2.0 is a ransomware variant belonging to the Babuk family. It recently released its second major release, and...
The Evilnum hacking group have been targeting European organisations that are involved in international migration, showing renewed...
A multistage remote access trojan (RAT) named ZuoRAT has been targeting remote workers with the help of...
The 2FA application necessary to access BBVA bank accounts in Spain is impersonated by a new Android...
A Chinese-speaking threat actor has hacked into the building automation systems (used to control HVAC, fire, and...
CODESYS has launched patches to handle as many as 11 safety flaws that, if efficiently exploited, may...
CrowdStrike researchers recently investigated the compromise of a Mitel VOIP appliance as an entry point in a...
Many ransomware gangs have attempted and failed to quake the cybersecurity landscape. But some have broken through and even...
Malware researchers have noticed a new tool that helps cybercriminals build malicious. LNK files to deliver payloads...
Two Chinese language hacking teams conducting cyber espionage and stealing mental property from Japanese and western firms...
Google announced the release of Chrome 103 to the stable channel with patches for a total of...
Cybersecurity researchers have discovered a new campaign attributed to the chinese “Tropic Trooper” hacking group. Tropic Trooper...
The Ukrainian CERT is warning that russian hacking groups are exploiting the Follina code execution vulnerability in...
In Vmware Spring Cloud Function versions 3.2.5 and older unsupported versions, it is possible for a user...
A complicated persistent menace (APT) group dubbed ToddyCat has been focusing on Microsoft Trade servers all through...
The malicious attacker driving the BRATA banking trojan has upgraded its techniques and added information-stealing features to...
WordPress sites using Ninja Forms, a forms builder plugin with more than 1 million installations, have been force-updated...
Cybersecurity researchers have detailed a recently patched high-severity security vulnerability in the popular Fastjson library that could be potentially...
The ALPHV ransomware gang, also known as BlackCat has created a dedicated website that allows the customers...
The “Blue Mockingbird” group has targeted Telerik UI vulnerabilities to compromise servers. The threat actor installed the Cobalt Strike beacon...
A new side-channel attack known as Hertzbleed allows remote attackers to steal full cryptographic keys by observing...
Citrix has released security updates to address vulnerabilities in application delivery management. An attacker could exploit these...
Zimbra is an enterprise-level email solution, similar to Microsoft Exchange. It comes with mail servers, load balancing...
Cybersecurity researchers report increased activity of the Hello XD ransomware, whose operators are now deploying an stronger...
Google Chrome has been infected with a new type of malware known as Emotet, which steal users’ confidential...
A new Google Chrome browser extension called Vytal prevents webpages from using programming APIs to find your...
A newly discovered Linux malware known as Symbiote infects all running processes on compromised systems, steals account...
A joint multi-national cybersecurity advisory has revealed the top ten attackers vectors most exploited by cybercriminals in order to...
A new binary sampled by Trend Micro included minor additions and changes that make the malware more...
As we all know each WhatsApp account is tied to a phone number, and hackers are calling...
In phishing assaults, the Qbot malware now uses the Windows MSDT zero-day. A serious Windows zero-day vulnerability...
The number of DeadBolt-infected devices is considerably high for a ransomware family that is exclusively targeting NAS...
LuoYu, a Chinese-speaking hacking group, is infecting victims with the WinDealer information stealer that installs backdoors to...
Researchers found a vulnerability in Atlassian Confluence by conducting an incident response investigation. Atlassian rates the severity level...
The CISA is releasing this CSA to warn organizations that malicious cyber actors, likely APT actors, are...
The “Parrot TDS” campaign involving more than 16,500 infected websites. such massive infections don’t go unnoticed by...
Microsoft successfully detected and disabled attack activity abusing OneDrive by a previously undocumented Lebanon-based activity group Microsoft...
Researchers analyzing the leaked chats of the notorious Conti ransomware operation have discovered that teams inside the...
EnemyBot, a botnet derived from many pieces of malware codes, extends its overall reach by rapidly incorporating...
Threat analysts have spotted a new version of the XLoader botnet malware that uses probability theory to...
Security researchers recently discovered a new Microsoft Office zero-day flaw(Follina) exploited in PowerShell remote code execution attacks....
The malware is designed to install malicious extension(s) onto browsers. Currently, two distinct variants of ChromeLoader have...
The Austrian Federal State, Carinthia was attacked on Tuesday and Government services were severely disrupted as more...
Open Automation Software (OAS) has been identified with vulnerabilities by researchers. These vulnerabilities are getting exploited by...
The General Motors had released a report last week about a data breach in the company that...
BPFDoor is a traditional backdoor that had been exploited against the Government, telecommunication, Education and Logistics organizations...
SpiceJet, an airline service providing air transport services since a long time. It offers various destination flights...
A malicious python package named “pymafka” was found in the PyPI registry by Sonatype’s automated malware detection...
Nikkei announced on this Thursday that their server at Asian headquarters located in Singapore was hit by...
Microsoft Office Files are exploited for social engineering lures (especially Excel and Word), as these file formats...
VMware servers are targeted again by the North Korean Hackers called Lazarus. The CVE-2021-44228 is exploited again...
A sophisticated phishing campaign has started targeting Windows User. But, this campaign differs from other phishing attacks...
Recent observance by researchers in the Google Play Store showed that numbers of applications are malicious to...
Due to the hiking interests towards the Pixelmon NFT Site, the threat actors have turned their attention...
Recently, BPFDoor – a malware was brought to light after years under the radar. It allows a...
Starlink is Satellite Internet Company owned by Elon Musk and it was activated in Ukraine after Russia...
A post-exploitation malware Framework set down within the Microsoft Exchange Servers of organizations in various sectors across...
Admins have been warned by the security researchers against a critical Remote-Control Execution (RCE) flaw in the...
Researchers have discovered a new malicious campaign using a never-before-seen technique for injecting Fileless malware on target...
IKEA Canada has notified Canada’s Office of Privacy Commissioner (OPC) after the personal information of 95k Canadian...
Cisco has released software updates that address the Enterprise Network Function Virtualization Infrastructure Software (NFVIS) vulnerabilities. The...
TLStorm – a group of vulnerabilities found while implementing TLS(Transport Security Layer) in multiple models of network...
A recently uncovered espionage threat actors are targeting the employees majoring in the mergers and acquisitions to...
Past Week we could see a lot of Indian Organizations were under targeted attack and they were...
Black Basta, a new ransomware has started its play during the month of April, with a start...
Are they not understanding the aftermath of hacking? The article released by us on Monday about “Stormous...
Security Researchers Identified “Stormous ransomware campaigns” targeting multiple organization, especially Indian organization for financial motivation This group...
OUTLINE The Emerging growth of the Digital Currencies also develops the need of protection from unforeseen hazards....
OVERVIEW Attack was active on Feb-08-2022 through RedLine Malware, now it’s more effective and researchers named that...
TraderTraitor – North Korean Group targeting the Blockchain companies and NFT trading platforms to heist your NFT’s...
Security Advisory Description BIG-IP APM AD (Active Directory) authentication can be bypassed using a spoofed AS-REP (Kerberos...
Attackers using Excel documents to distribute various malware — placing backdoor to compromise machines. Macros Malware Recent...
Siemens released security update for Siemens Mendix Applications — prone to an elevation of privilege vulnerability.prone to...
Adobe released vulnerability update for RoboHelp — prone to an elevation of privilege vulnerability. Elevation of Privilege...
Passwordstate app’s update hijacked to install malware in a supply-chain attack after breaching its networks. Supply Chain...
Attackers are exploiting zero-day in Pulse Secure VPNs to breach organisations — (CVE-2021-22893) 0-Day Vulnerability Security mitigations...
Adobe has released a security update for Adobe Bridge for arbitrary code execution in the context of the current user....
This time the ransomware relied more on compromising exposed RDP connections to gain an initial foothold on...
During external security research a CRITICAL remote code execution vulnerability discovered in overlayd service. CVE-2021-0254 — JUNOS...
Apache released security updates for bypass of older vulnerability — Arbitrary Code Execution Apache Tapestry — Arbitrary...
Adobe has released updates for Windows and macOS for CRITICAL severity vulnerabilities in Photoshop. Photoshop Vulnerability Multiple...
An exploit aimed at the V8 JavaScript rendering engine to hack Google Chrome and Microsoft Edge (Chromium)...
Leading pharmaceutical group Pierre Fabre confirmed a REvil ransomware attack — demanded a $25 million ransom. REvil Ransomware,...
Android Device Malware Attack Malware infection detected in Gigaset Android devices as external update server got compromised....
Cisco has released security updates regarding multiple vulnerabilities — considered as CRITICAL severity. Vulnerability Advisory Cisco Small...
Researchers discovered wormable android malware — capable of propagating via WhatsApp messages. FlixOnline Malicious App Researchers recently...
Threat actors targeting widely deployed, mission-critical SAP applications — exposing the networks of commercial and government organizations...
Security update is available to remediate the critical vulnerability addressing VMware Carbon Black Cloud Workload appliance. CVE-2021-21982...
Fake job offer — phishing campaigns delivering backdoor, targeting job professionals in LinkedIn. LinkedIn Spear-Phishing eSentire’s research...
Multiple vulnerabilities were found in QNAP NAS devices allowing access to user data and complete takeover. 0-Day...
Over 533 million worldwide Facebook users data leaked on a popular cyber-crime forum for free. Tech Giants...
Researcher identified in Umbraco CMS — privilege escalation vulnerability allowing attackers to access resources which are normally...
The FBI and CISA warn — APT actors are scanning Fortinet FortiOS for vulnerabilities — to gain...
Chrome – the Stable channel updated to 89.0.4389.114 for Windows, Mac and Linux. Vulnerability Update Chrome addressed...
Thousands of customers data using Indian Payments App account leaked and available on the dark web. MobiKwik —...
Researchers uncovered malware posing as System Update — takes control of the device, steals almost all the...
Threat actors are hosting a new malware “Purple Fox” campaign — attacks have spiked by about 600%...
RCE vulnerability in latest Apache OFBiz due to Java serialisation using RMI — Patch to the latest...
MyBB released security updates for multiple vulnerabilities including SQL injection, XSS attacks, bypassing issues. Security Vulnerability MyBB...
PC giant Acer attacked by ransomware gangs — demanded $50 million to not leak on dark web...
A security vulnerability update released by Intel to mitigate this potential vulnerability. CVE-2020-24482 — Intel 7360 Cell...
An E-Commerce platform running open-source Magento v2 compromised by threat actors — hid the stolen details in...
Adobe has released security updates for its products causing Boundary Condition problem. CVE-2021-21056 — Adobe Framemaker Adobe...
Threat actors are using the recently disclosed zero-day ProxyLogon vulnerabilities — installing a new strain of ransomware...
Google fixed another 0-day vulnerability in Chrome browser within a month. CVE-2021-21193 — Chrome Zero-Day A new zero-day vulnerability...
Fortinet released security fix for the vulnerability — Security ByPass CVE-2021-22128 — FortiProxy SSL VPN FortiProxy — a...
Apple has released security updates for a severe vulnerability affected in Apple Safari, macOS Big Sur, iOS,...
Accellion released patches addressing vulnerabilities in its File Transfer Appliance. CVE-2021-27104 — Accellion File Transfer Appliance Recently,...
Samsung started rolling out Android’s March 2021 security updates for critical security vulnerabilities. March 2021 — Samsung...
Zero-Day vulnerabilities are actively exploit — attacks against local US government agencies. Microsoft Exchange Server — Zero-Day...
Google warned users to update Chrome browser — zero-day vulnerability in the Chrome browser — actively exploited...
Jailbreaking threat made possible to all iPhone models under risk as a vulnerability that Apple already been...
A weird Windows 10 drive corruption bug fixed — available for Windows Insider program. Windows 10 Driver...
Research at Oxford University lab studying COVID-19 — attacked by threat actors. COVID-19 Research Researcher from Oxford...
Security updates are available to remediate multiple vulnerabilities affecting VMware products. vCenter Security Vulenerabilties: Multiple vulnerabilities in...
A security update released for PHP Denial of Service Vulnerability. CVE-2021-21702 — Denial Of Service In PHP...
Cisco released security updates for Cisco AnyConnect secure mobility client for windows arbitrary code execution vulnerability. CVE-2021-1366...
Underwriters Laboratories UL LLC, a global safety certification company has suffered a ransomware attack that encrypted its servers....
Researchers discovered a zero-day vulnerability on IBM InfoSphere Information Server 8.5.0.0 Description: IBM InfoSphere Information Server is a...
WatchDog botnet performs cryptojacking for almost 2 years to take over windows and linux servers. Daemon —...
Apple has released a new update that could cause serious data loss. Big Sur 11.2 to 11.2.1(20D75)...
A Sticker sent to Telegram account could expose data including Secret chats, Photos, etc Animated Sticker Bug...
Patch released for a new critical vulnerability affecting SAP commerce platforms. SAP Commerce — CVE-2021-21477 SAP Commerce...
The system administrator of Russian company sold thousands of user email accounts. Yandex Suffers Data Breach During...
Threat actors modified the concentration of LYE to dangerous parameters. LYE Level Modified: Anonymous actors accessed computer...
Hackers group has poisoned multiple Sri Lankan domains on Saturday. Defaced .LK Domains: A mysterious group of...
SitePoint admitted a data breach after finding sale of one million SitePoint user details. SitePoint — User...
Google’s browser released a vulnerability which is actively being exploited in the wild. Chromium CVE-2021-21148: Heap Buffer...
A severe vulnerability found in Libgcrypt and recommended not to use. Libgcrypt 1.9.0 Vulnerability Tavis Ormandy of...
Hackers group Lebanese Cedar attack unpatched Atlassian servers at telcoms, Hosting and ISPs providers. Lebanese Cedar A...
Cisco disclosed a high-severity vulnerability allows cross-site request forgery (CSRF) attacks and Information Disclosure Vulnerability. CVE-2021-1257 —...
Sudo vulnerability, local user can exploit this flaw for root privilege escalation. Linux — CVE-2021-3156 Sudo (su...
Three new Zero-Day vulnerabilities patch released by Apple. Exploited in the wild: On Tuesday, Apple released updates...
Researchers found a new Adware campaign spreading through WhatsApp contacts. Adware Campaign — Android Adware, along with...
A technician from ADT accessed more than hundreds of customers CCTV systems to spy on them, engaging...
Cisco warns customers about critical security vulnerabilities affecting SD-WAN, DNA, and the Smart Software Manager Satellite. Security...
SonicWall released an urgent notice to their clients to patch a series Zero-Day vulnerability. VPN Zero-Day Vulnerability:...
A phishing scam through Google search left thousands of stolen passwords exposed. Phishing Campaign A phishing campaign...
Chrome 88 new update with a feature now checks for weak passwords, helps fix them. Chrome 88’s...
Adobe released security updates for arbitrary code execution vulnerability for Windows and macOS. Description: Adobe Photoshop version...
After Microsoft, FireEye and CrowdStrike, Malwarebytes hit by hacked SolarWinds. Malwarebytes — UNC2452 An Anti-Virus provider for...
User data stolen from OpenWRT Forum leading to a database breach. OpenWRT The OpenWrt Project is a...
More than 10million users installed Android apps that showed out-of-context ads. Android Applications — Out-Of-Context Ads Google...
Microsoft to fix Windows 10 bug that can corrupt a hard drive just by opening a folder...
Patch Tuesday of 2021 addressed 83 flaws spanning as many as 11 products and services. Microsoft Patch...
Attackers infect booby-trapped websites — who visited them. Zero-Day Exploit: A computer-software vulnerability that is unknown to...
Ubiquiti, the Networking giant alerts customers to change passwords after a security breach. Data Breach — Ubiquiti...
FortiWeb is vulnerable to a blind SQL injection FortiWeb — CVE-2020-29015 Summary: A blind SQL injection in...
Encrypted messaging service in Signal — verification process delay affecting its new user, recovered. Encrypted Messaging Service:...
Nearby Share feature can be exploited by adversaries to spoof GPS and get access to users’ exact...
In first update of 2021, NVIDIA patched 16 CVEs across its graphics drivers and vGPU software. NVIDIA...
SolarWinds Hackers accessed Office 365 mailboxes of the U.S. Justice Department’s. SolarWinds Attack Over 100 to 280...
Google’s Android Security Update addressed 43 bugs affecting Android Handsets, including Samsung phones. Android Security Update: The...
Apache released patches for some of its products. Apache Tapestry — CVE-2020-17531 Description: Apache Tapestry is prone...
Scammers targeting users to get personal details — Federal officials. COVID-19 Pandemic: Coronavirus disease, an infectious disease...
More than 100,000 Zyxel firewalls, VPN gateways, and access point controllers contain a hardcoded admin-level backdoor account....
Adobe Flash Player will no longer be supporting Flash Player after 31 December 2020. Adobe Flash Player:...
Apache TomEE Security Bypass Vulnerability. Description: Apache TomEE is prone to a security bypass vulnerability. The vulnerability...
Cisco Secure Web Appliance Elevation of Privilege Vulnerability. Description: A vulnerability in the log subscription subsystem of...
Japanese Aerospace Firm Kawasaki — their data have been stolen following a security breach. Kawasaki Heavy Industries,...
A complex Supply-Chain attack hit Vietnam Government Certification Authority (VGCA). Supply Chain Attack: A cyber-attack that seeks to...
Apple users face trouble in accessing data, setting up and signing in on the device. Apple iCloud...
Attackers target online shoppers using fake Amazon gift cards that deliver the Dridex banking Trojan. Holiday Gifts...
Summary: A security bypass vulnerability found in Apache Pulsar. Vulnerability Identifier: CVE-2020-17520 The vulnerability is caused due to...
Cyber-attacks against two separate entities related to COVID-19 research. Lazarus group A threat group, active since at...
US FBI and Interpol have seized a small number of servers used by Joker’s Stash. Joker’s Stash...
Threat actors compromised the IT monitoring and management software of organizations including SolarWinds’s Orion, Intel, Cisco, Nvidia. Trojanized...
Security researchers discovered vulnerabilities in Dell Wyse Thin client devices. Dell Wyse Thin Clients Wyse has been...
Recently, NVD published a list of Common Vulnerabilities and Exposures(CVE) and their impact metrics Security Update NVD,...
Researchers identified malware hidden in at least 28 third-party Google Chrome and Microsoft Edge extensions — affects...
Hewlett Packard Enterprise Systems Insight Manager (SIM), AMF Deserialization of Untrusted Data, Remote Code Execution Vulnerability. Description:...
45 million medical imaging files, personal data left discoverable on the open web, across 67 countries including...
Multiple Google services — Gmail, Docs, YouTube have gone down across the world. Services Restoring After an...
PgMiner botnet targets PostgreSQL databases to install a cryptocurrency miner. PgMiner Botnet: PostgreSQL, also known as Postgres,...
Samsung’s Android December security updates are rolling out to mobile devices to patch security vulnerabilities. High-Security Vulnerabilities...
Former Cisco Engineer’s action lost 16k Webex accounts, as he accessed Cisco’s AWS accounts and deleted 456...
A critical flaw resolved in Glassdoor which could be exploited to take over accounts. Critical Flaw in...
EMA, the EU regulatory body in charge of approving COVID-19 vaccines, became the victim of a cyber-attack today. Cyber-Attack...
MDhex-Ray is a vulnerability that affects a long list of CT, X-Ray, and MRI imaging systems manufactured by...
Nine critical bugs and 58 overall fixes mark the last scheduled security advisory of 2020. Patch for...
Hackers found new way to attack e-commerce stores, online shoppers and steal credit card details. Steganography, Web...
The Brazilian aerospace conglomerate became the victim of a ransomware attack last month. Embraer — Aerospace company...
Kopter’s data has been published on the LockBit gang’s blog, hosted on the dark web. Kopter —...
Johnson & Johnson, are seeing cyber-attacks from nation-state threat actors “every single minute of every single day.”...
Multiple botnets exploit through remote code execution vulnerability in Oracle WebLogic Server. Oracle WebLogic Server: Oracle WebLogic is a...
The remote CentOS Linux host is missing one or more security updates. Description: The remote CentOS Linux...
Access for Hundreds of C-level (like CEO, CFO, etc) executives is sold for $100 to $1500 per...
Over 16 million Brazilian COVID-19 patient’s personal data exposed online, including Brazil President Jair Bolsonaro, seven ministers,...
The Xbox flaw allows hackers to compromise the user’s real-time identity, If attackers had access to the email...
Indian government has banned another 43 Chinese mobile applications. The Ministry of Electronics and Information Technology banned...
Two popular Android apps from Chinese tech giant Baidu caught collecting sensitive user details. Baidu Android Apps:...
VMware has released temporary workarounds to address a critical vulnerability in its products that could be exploited...
Google Project Zero reported a high severity security flaw in GitHub. GitHub GitHub, Inc. is a subsidiary...
A football club, Manchester United Plc can confirm that the club has experienced a cyber attack on...
Facebook fixed a major security bug in Facebook messenger for Android application, which let hackers listen before...
IBM researchers discovered bugs that allow attackers to sneak in and join Webex meetings as ghost users,...
Cisco has hurried out a patch after a day after proof-of-concept (PoC) exploit code was published for...
A fake Java update found on various porn sites actually downloads the well-known Zloader malware. Target On...
Microsoft says hackers from Russia and North Korea are attacking COVID-19 vaccine makers. However, the organizations in...
A new malware, named Jupyter that steals information’s from the user, and also the malware is used...
Intel addressed 95 vulnerabilities on November 2020 Patch Tuesday, including critical ones affecting Intel Wireless Bluetooth products and Intel AMT. Vulnerability...
Microsoft warns that cybercriminals are using Cobalt Strike to infect entire networks beyond the infection point, according...
Multiple operating systems and browsers successfully exploited in minutes by Bug Bounty hunters at Tianfu Cup 2020,...
Android November security update/patch 2020 tracker for all major OEMs and carriers worldwide. Android OEM: OEM stands...
An updated fix was issued by VMware for a critical-severity remote code execution flaw in its ESXi...
GitHub site layout broken as the company failed to renew the SSL certificate. GitHub: Git and Hub...
Short Summary: Multiple vulnerabilities were found in Google Chrome with High severity. These vulnerabilities can be exploited...
Hacker is selling account databases containing a total of 34 million user records stolen from 17 companies....
Microsoft warned Windows 10 users as they received a “small number of reports” from customers and others...
Oracle fixed a vulnerability as attackers started targeting servers running on Oracle WebLogic instances, vulnerable to a...
A team at Avast has uncovered another set of malicious apps in the Google Play Store. Adware?...
This week, the popular Chinese video-sharing social networking service TikTok has launched a public bug bounty program...
Google’s web browser has a “zero-day” vulnerability actively exploited. The Mountain View firm has just released a...
Donald Trump Twitter account was hacked by a Dutch security researcher, claims he has gained access to...
Cyber Security researchers disclosed vulnerability details of multiple popular browsers about an Address Bar Spoofing vulnerability affecting...
Security experts were amazed for the first time, as a Hacking group is donating the stolen money...
Emotet is a Trojan that is primarily spread through spam emails (malspam). The infection may arrive either via a malicious script,...
The Department of Homeland Security, Cybersecurity Agency, urges Windows 10 users to apply for security updates. On September...
A cyber security firm alleges that user and donor data of over five lakh people have been...
Google researchers warned on a new set of potential security vulnerabilities(allow escalation of privilege or information disclosure)...
A serious Cyber Attack hit on the London Council which is affecting many of its services and...
Microsoft released patches for 87 newly discovered vulnerabilities on its October 2020 Patch Tuesday. Of the 87 vulnerabilities...
Android users were alerted by Microsoft, as they found a new ransomware MalLocker.B, the ransomware triggers on...
Cyber Security researchers disclosed details of vulnerabilities found in popular Anti-Virus solutions that could enable attackers to...
What is Shadow Volume Copies? Shadow Copy is a technology included in Microsoft Windows that can create...
University Hospital New Jersey in Newark, New Jersey – Paid a ransom of $670,000 demanded by the...
Twitter removed some accounts based on the tip provided by the FBI. As there was an attempt...
Microsoft says a recent update has affected the processing of authentication requests, making cloud-based services inaccessible. Microsoft said people...
Over 2,000 Magento stores were compromised over the weekend. The private information of thousands of customers has...
Vulnerability – CVE-2020-1472 Description: An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon...
A cybercrime group named Malsmoke has been targeting porn sites with malicious ads redirecting users to exploit...
Attackers got an eye on the Victims O365 credentials in real-time as they enter their credentials into...
Data center giant Equinix has been hit by a ransomware attack. Equinix, one of the world’s largest...
BLURtooth, is referred to the vulnerability for the devices supporting Bluetooth BR/EDR(Bluetooth Basic Rate/ Enhanced Data Rate)...
Patch Tuesday:- The second Tuesday of each month is the one most commonly referred to as Patch Tuesday. That’s when Microsoft releases...
Argentina’s official immigration agency, Dirección Nacional de Migraciones, suffered a Netwalker ransomware attack that temporarily halted for...
On July, there was massive Twitter security breach of 130 high-profiles like US presidential hopeful Joe Biden,...
Norway parliament’s non-elected chief administrator – Marianne Andreassen said that “This has been a significant attack” The...
WordPress File Manager Plugin – Security Vulnerability Short Summary: A remote code execution vulnerability was found in...
VMware RabbitMQ Arbitrary Code Execution Vulnerability Short Summary:A code execution vulnerability was found in VMware RabbitMQ. The...
Magecart Group:- Magecart is a consortium of malicious hacker groups who target online shopping cart systems, usually...
Short Summary Multiple vulnerabilities were found in the Distance Vector Multicast Routing Protocol (DVMRP) feature of Cisco...
Type/Severity Security Advisory: Critical Topic An update is now available for CloudForms Management Engine 5.10. Description A...
Emotet Trojan:- Emotet is a Trojan that is primarily spread through spam emails (malspam). The infection may arrive either via...
Have you invested millions of dollars on your security devices? Better spend half for your employer’s. The...
What is a Malware? Malware is any software intentionally designed to cause damage to a computer, server,...
Name : chromium Product : Fedora 31 Version : 84.0.4147.89 Release : 1.fc31 URL : http://www.chromium.org/Home Summary...
IBM Security Guardium Insights is affected by an Open Redirect vulnerability Summary IBM Security Guardium Insights has...
A vulnerability has been identified in IBM Elastic Storager Server where an attacker can cause a denial of...
Lazarus Group who are known as APT38 enact themselves as a Job recruitment division for the US...
Security researchers have discovered a GhostClaw malware has been discovered in a malicious npm package that steals...
Cybersecurity researchers have uncovered Microsoft Teams attack campaigns are now targeting employees in finance and healthcare organizations...
A critical security vulnerability has been discovered in ZITADEL, an open-source identity and access management platform used...
OpenAI has introduced Codex Security, a new AI-powered application security agent that helps developers automatically detect and...
Researchers have identified a security issue in Apache ActiveMQ, specifically related to the Apache ActiveMQ DoS vulnerability,...