The cybersecurity landscape is at a worrying point. On December 5, 2025, Huntress discovered a smart attack using the Atomic macOS Stealer (AMOS) delivered through a very simple method.
Attackers are using AI chats on OpenAI’s ChatGPT and xAI’s Grok. They push these chats to the top of search results using SEO tricks, making them look like trusted troubleshooting guides.
The danger is that users don’t download anything suspicious. No installers, no malware files, and no warnings. All it takes is searching on Google, clicking a result, and copy-pasting a command.
This attack works by abusing three types of trust: search engines, legitimate platforms, and AI-generated advice.
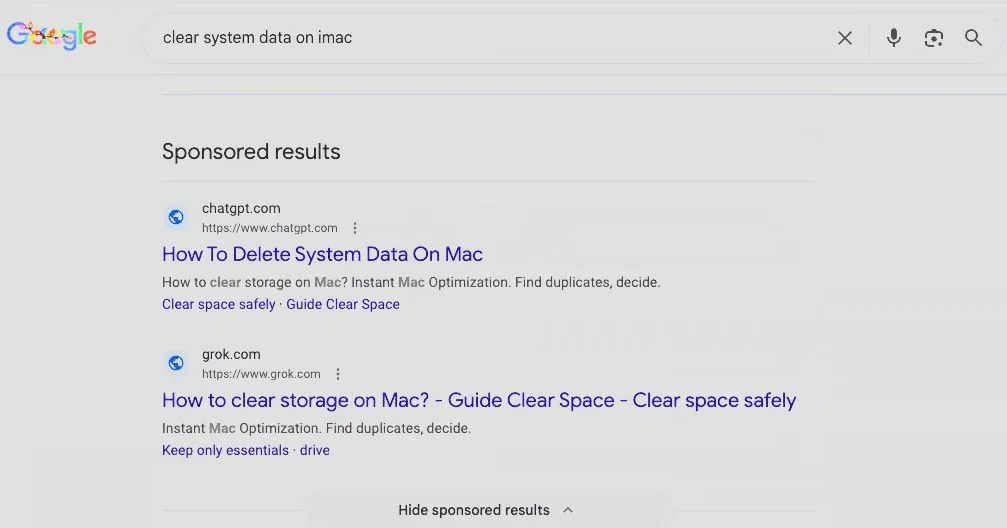
When users search basic macOS tips like “clear disk space on macOS,” top results lead them to real ChatGPT or Grok pages.
These pages look professional and safe, offering step-by-step instructions.
But when the victim runs the Terminal command, it triggers a hidden multi-stage attack that steals credentials, gains higher access, and sends data out silently.
Exploiting Trust Through AI
This is a major evolution in social engineering. Attackers are not pretending to be trusted platforms anymore—they are turning trusted platforms into weapons using poisoned search results.
The malware doesn’t need to look like safe software when it can pretend to be helpful guidance.
During the investigation, Huntress confirmed similar poisoned results for searches like “how to clear data on iMac,” “clear system data on iMac,” and “free up storage on Mac,” proving this is a broad, intentional campaign—not a one-off case.
The presence of similar campaigns on both ChatGPT and Grok shows that a coordinated attacker is actively targeting these platforms.
The AMOS delivery method makes this even more dangerous. The first command runs a bash script that tricks users into entering their system password for “verification.”
Instead of showing a real macOS login prompt, the script checks the password quietly in the background using the dscl-authonly command—no system dialog, no Touch ID, and no warning.
Once the password is confirmed, the script stores it in plaintext and uses it to gain full admin access through sudo -S without asking the user again.
It then installs the main stealer payload in a hidden .helper folder inside the user’s home directory.
Finally, it replaces genuine crypto wallet apps like Ledger and Trezor with fake versions designed to steal seed phrases.
New AI-Enabled Attack Methods
The stealer quietly gathers data from crypto wallets, browser passwords, the macOS Keychain, and other sensitive files.
Its persistence method is also very stealthy. A LaunchDaemon runs a hidden AppleScript loop that checks the active user every second, keeping the malware running nonstop.
f the .helper malware stops for any reason, the watchdog brings it back almost instantly.
This keeps it running all the time — even after a restart or if someone tries to kill the process — and lets it access user-level passwords and app data that normal background services can’t touch.
For defenders, this attack is difficult to spot. The infection starts with a harmless-looking Terminal command, so signature-based tools see nothing unusual.
Detection now depends on noticing odd behavior: unexpected osascript password checks, strange dscl-authonly activity, hidden files in the home directory, or processes using sudo with piped passwords.
For users, the danger is even more subtle. Nothing feels suspicious. Copying a command from ChatGPT seems normal and helpful — not risky.
As AI becomes part of everyday tasks, this technique will spread fast. It’s easy to scale and hard to block with traditional defenses.
This campaign is a turning point for macOS security. The real shift isn’t AMOS itself — it’s the delivery method that slips past both security tools and human judgment.
Today’s attacks don’t just target machines — they target habits and our growing trust in AI.












Leave A Comment