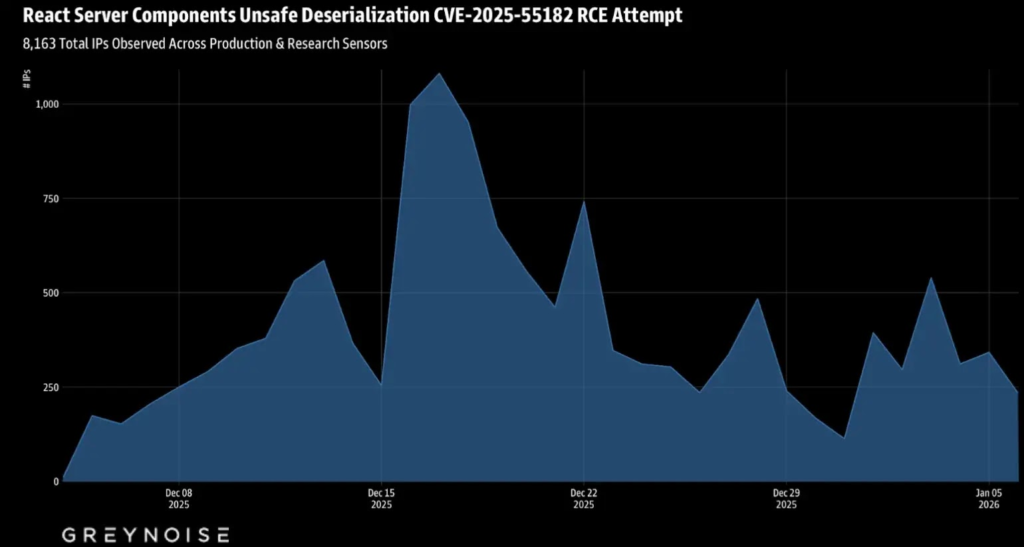
The React2Shell vulnerability (CVE-2025-55182) continues to be heavily targeted, with attackers launching more than 8.1 million attack attempts since the flaw was disclosed.
Data from GreyNoise shows that while daily attack activity has slightly slowed, it remains extremely high. Attack volumes now average 300,000 to 400,000 attempts per day, confirming that exploitation is ongoing and well-organized.
Large-Scale and Global Exploitation
The attack campaign is spread across a wide infrastructure. Researchers observed activity coming from thousands of unique IP addresses, spanning over 1,000 networks and more than 100 countries.
Cloud platforms are being widely abused to support the attacks. A large portion of the traffic originates from major cloud providers, with Amazon Web Services accounting for a significant share. This approach helps attackers blend in with legitimate traffic and rotate infrastructure quickly.
How the Attacks Work
Most exploitation attempts follow a consistent pattern:
- Initial probes test whether commands can be executed on the target system
- If successful, attackers deliver encoded payloads
- Additional scripts are run using techniques designed to bypass security controls
Attackers continue to refine their methods, creating tens of thousands of unique payloads and using varied tools to avoid detection. This constant change makes static defenses like fixed IP blocklists ineffective.
What Organizations Should Do
Systems that remain unpatched are still at risk. Nearly half of the attacking infrastructure appeared only in recent months, showing that new resources are constantly being added.
To reduce exposure, organizations should:
- Patch affected React Server Components immediately
- Monitor for suspicious PowerShell activity and encoded commands
- Use dynamic threat intelligence rather than static blocklists
- Apply network-level protections to exposed services
React2Shell is not a short-lived threat. It remains an active and persistent attack vector that requires immediate attention and ongoing monitoring.
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!













Leave A Comment