Recent research has shed light on how underground carding markets operate online. Investigators identified 28 active IP addresses and 85 domains that were being used to host illegal marketplaces where stolen credit card data is sold.
These sites function much like regular online stores, but instead of legitimate goods, they offer stolen payment card details. Prices vary based on factors such as credit limits and whether additional personal information is included.
The research, conducted between July and December 2025, relied on large-scale internet scanning to locate carding infrastructure early—before it could be hidden behind services like content delivery networks.
How the Infrastructure Was Identified
Researchers scanned common web ports and analyzed page titles and banners looking for terms commonly used in carding communities. This method helped uncover servers during setup stages, before protective layers masked their true locations.
Key observations from the analysis include:
- Servers hosting login pages and forums for carding sites
- Repeated use of specific keywords linked to card fraud
- Heavy reliance on certain domain extensions
Many of the identified domains used extensions such as .su, .cc, and .ru, which are often favored due to looser registration controls and jurisdictional challenges.
Where Stolen Card Data Comes From
Stolen payment information enters these markets through several methods. Online attacks include malicious scripts injected into checkout pages and breaches of retail or financial databases. In the physical world, skimming devices placed on ATMs or payment terminals are still widely used.
Once collected, the data moves through a structured underground supply chain, where different actors specialize in theft, resale, and conversion into cash.
The findings provide valuable insight into how carding operations are set up and maintained, offering opportunities for disruption and enforcement action.
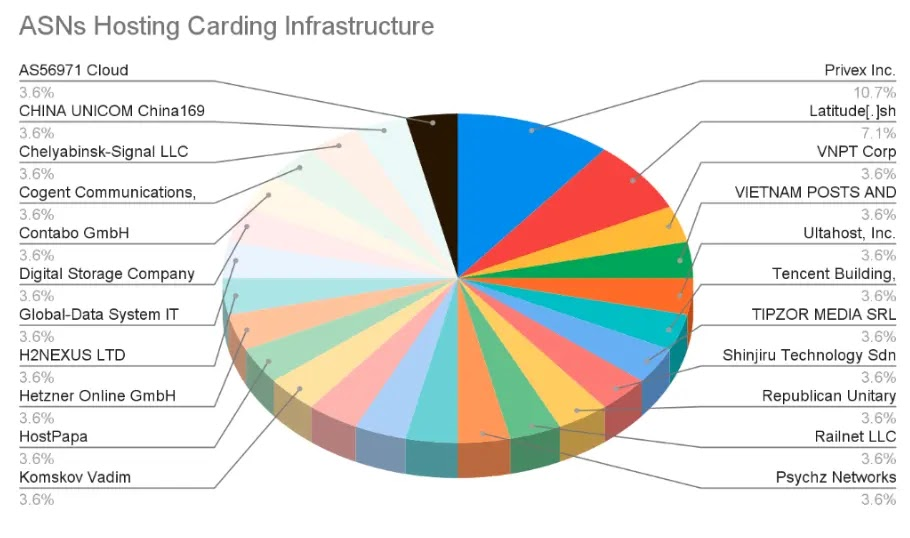
Analysis of the 28 identified IP addresses shows that many of the servers are hosted in regions where cooperation with law enforcement is limited.
Several of the systems were linked to hosting providers that promote privacy-focused services. One provider appeared frequently, offering virtual servers that can be rented with little or no identity verification.
These hosting environments are not used only for carding sites. They are often reused for other malicious activity, including hacking tools and attack infrastructure.
The infrastructure analysis highlights where these servers are hosted, while separate findings show examples of carding market login pages and forum sites uncovered during the investigation.
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!













Leave A Comment