Security researchers have released a detailed technical analysis of the DragonForce ransomware, along with confirmation that working decryptors exist for certain Windows and ESXi victims. By the time DragonForce’s Data Leak Site (DLS) was discovered, at least 17 organizations had already been listed as victims.
First observed in December 2023, DragonForce quickly positioned itself as a serious Ransomware-as-a-Service (RaaS) operation. The group publicly promotes itself as a cartel and runs a service called “Ransombay,” allowing affiliates to request customized payloads and configurations.
DragonForce Ransomware
DragonForce operates under a structured RaaS model that was openly promoted in mid-2024 on underground forums. The group actively recruits a wide range of partners, including initial access brokers and independent penetration testers, offering affiliates up to 80% of ransom payments.
The operation does not exist in isolation. Code analysis shows that DragonForce is heavily derived from leaked LockBit 3.0 (Black) and Conti source code. Some samples demonstrate over 90% similarity with LockBit, strongly indicating reuse of the leaked LockBit builder combined with Conti-style logic.
Infrastructure overlaps and code reuse have also linked DragonForce to other ransomware groups such as BlackLock and RansomHub. In one incident, DragonForce operators even compromised BlackLock’s own leak site through a misconfiguration, exposing internal data.
Technical Design and Encryption Behavior
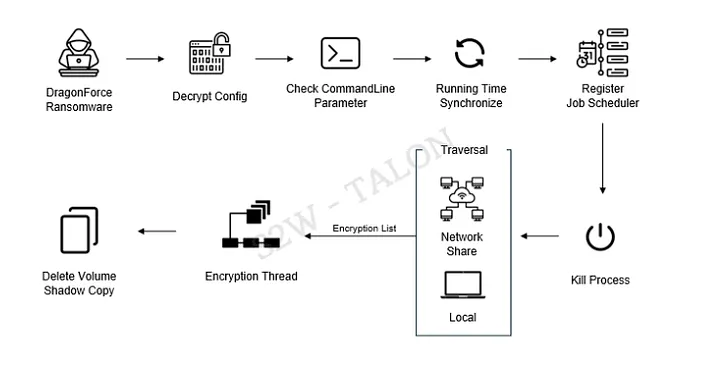
Internally, DragonForce uses custom string obfuscation, decrypting strings only at runtime. File encryption is based on the ChaCha8 stream cipher, with a unique session key generated per file.
Before encryption completes, DragonForce appends a metadata block to each file. This metadata contains the encrypted session key, encryption mode, file size, and additional flags required for recovery. Depending on file type and size, the ransomware applies full, partial, or header-only encryption, prioritizing performance while still disrupting critical systems such as databases and virtual machine images.
Network-based encryption capabilities allow DragonForce to scan private IP ranges, connect over SMB, and selectively target network shares while skipping administrative paths like ADMIN$. Optional features also allow the malware to rename files, change file icons, and replace the desktop wallpaper with ransom-themed imagery.
Decryptors for Windows and ESXi Victims
A significant development came when the S2W Threat Research and Intelligence Center (TALON) obtained DragonForce decryptors during threat-hunting operations. These tools are victim-specific and are not universal decryptors.
Decryptor Capabilities (Summary List)
- Separate decryptors for Windows and ESXi
- Uses embedded RSA-4096 private keys to recover ChaCha8 session keys
- Supports both local and network share decryption
- ESXi decryptors validate files using a per-victim build key
- Fully restores original files by removing appended metadata
Because DragonForce embeds the encryption keys within file metadata (protected by RSA), possession of the correct private key enables full data recovery for affected victims.
Recommendations
Organizations should treat DragonForce as a mature and evolving ransomware threat with strong ties to established ransomware families.
Recommended actions include:
- Monitor for LockBit and Conti-style indicators, including file structure similarities
- Harden initial access vectors, especially exposed services and stolen credentials
- Restrict SMB access and apply network segmentation
- Maintain offline, immutable backups for Windows and ESXi environments
- Engage incident response teams early if DragonForce activity is suspected
While the available decryptors offer hope for some victims, they are limited in scope. Prevention, early detection, and strong recovery planning remain the most reliable defenses against DragonForce attacks.
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!













Leave A Comment