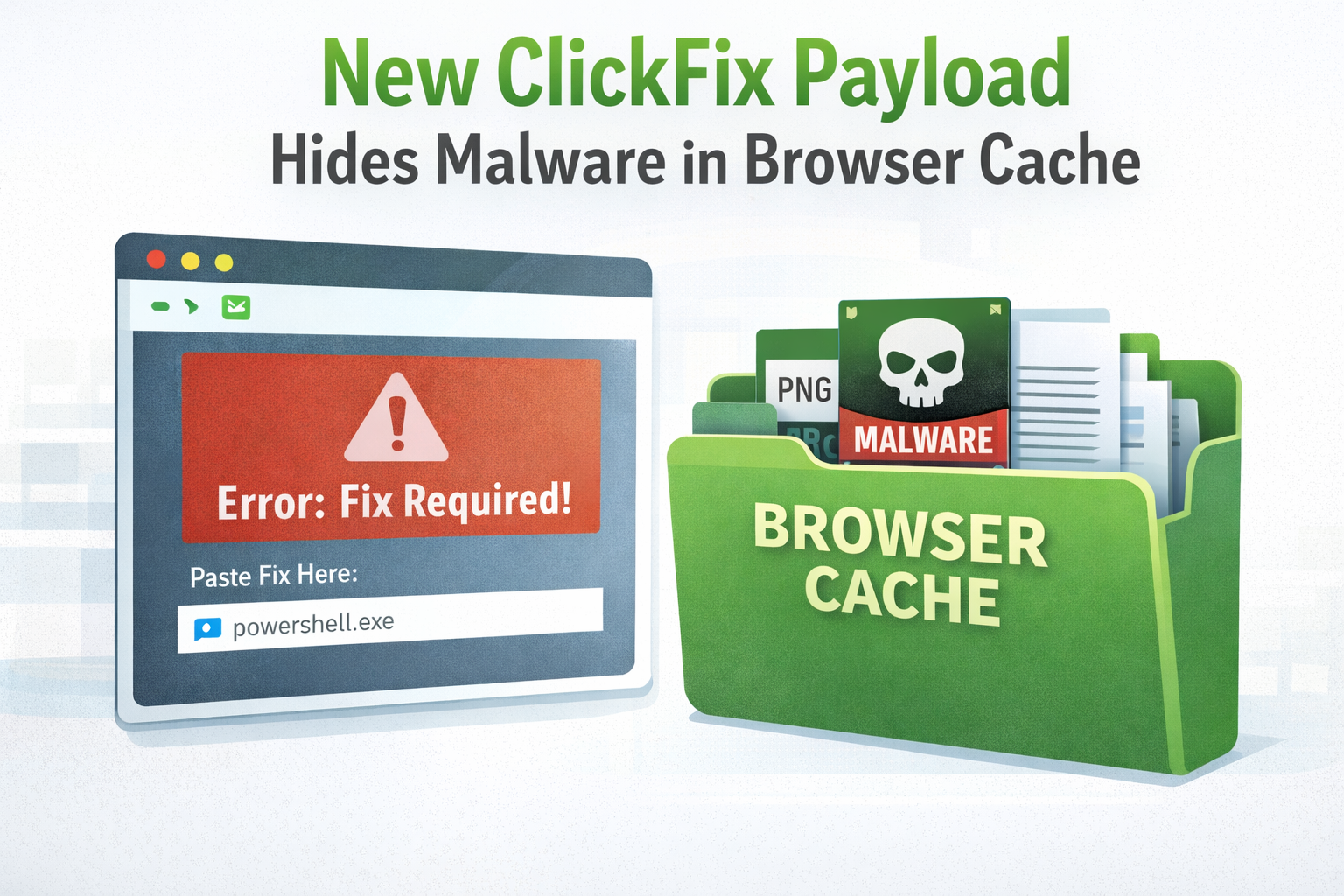
Cybersecurity researchers have uncovered a new version of the ‘ClickFix’ social engineering campaign. In this updated attack, malware is hidden directly inside the victim’s browser cache to avoid detection.
This is a significant shift in how attackers bypass security controls. Instead of downloading a suspicious file in a visible way, threat actors use normal browser functionality to quietly store the malicious payload. Because there is no obvious download at the time of execution, traditional endpoint protection and network monitoring tools may fail to detect the activity.
All about the attack – ClickFix Payload
The attack begins with the familiar ClickFix lure. Victims visiting compromised websites see fake error messages that appear to be related to Google Chrome or Microsoft Word. These messages instruct users to copy and paste a “fix” into PowerShell or the Windows Run dialog, claiming it will resolve the issue.
In earlier versions of ClickFix, the malware was downloaded after the victim executed the command. In this new variant, the malicious payload is silently loaded into the browser cache as soon as the victim visits the page. This pre-loading method helps attackers establish persistence and prepare the system for execution without raising immediate alerts.
According to Dark Web Informer analysts, this new malware strain was advertised on underground forums on February 17, 2026. The threat actor behind the campaign claims the technique specifically targets browser cache storage to hide the payload before it is executed.
The malware is disguised as a normal cached file, such as a PNG or JPG image. Because it appears to be a legitimate browser resource, it does not create suspicious web requests during execution. This approach can bypass many Endpoint Detection and Response (EDR) systems that focus on detecting real-time file downloads or unusual network activity.
The advertisement for the toolkit shows how accessible this attack method has become. The builder, source code, and setup instructions are being offered for $300. An additional $200 service allows buyers to request custom template rewrites, enabling them to tailor phishing lures to specific targets. The relatively low cost increases the likelihood that this technique will be adopted widely, including by actors deploying ransomware or information-stealing malware.
Cache-Based Persistence and Execution
The core innovation in this campaign is the use of the browser cache as a staging area.
When a victim visits the malicious landing page, the payload is silently fetched as what appears to be a harmless resource, such as an image file. It is then stored locally in the browser’s cache directory.
After the victim pastes and runs the provided PowerShell command, the script searches the cache folder, locates the stored file, and executes it.
Because the file is already present on the system, the execution phase does not require a new network connection. This allows the attack to bypass firewalls, proxy filters, and security tools that are designed to detect suspicious downloads initiated by command-line tools.
Security experts recommend closely monitoring PowerShell processes that access browser cache directories. Blocking known ClickFix-related domains and improving user awareness around copy-paste “fix” prompts can significantly reduce the risk of compromise.












Leave A Comment