The operators of the Gootkit access-as-a-service (AaaS) malware have resurfaced with updated techniques to compromise unsuspecting victims.
All about GootKit :
The Gootkit Access-as-a-Service (AaaS) malware’s operators have reemerged with updated techniques to compromise unsuspecting victims. Gootkit previously used freeware installers to disguise malicious files. According to Trend Micro researchers, it now uses legal documents to trick users into downloading these files.
Gootkit is part of the proliferating underground ecosystem of access brokers, who are known to provide other malicious actors a pathway into corporate networks for a price, paving the way for actual damaging attacks such as ransomware.
SEO Poisoning
The technique is to to lure unsuspecting users into visiting compromised websites hosting malware-laced ZIP package files purportedly related to disclosure agreements for real estate transactions.
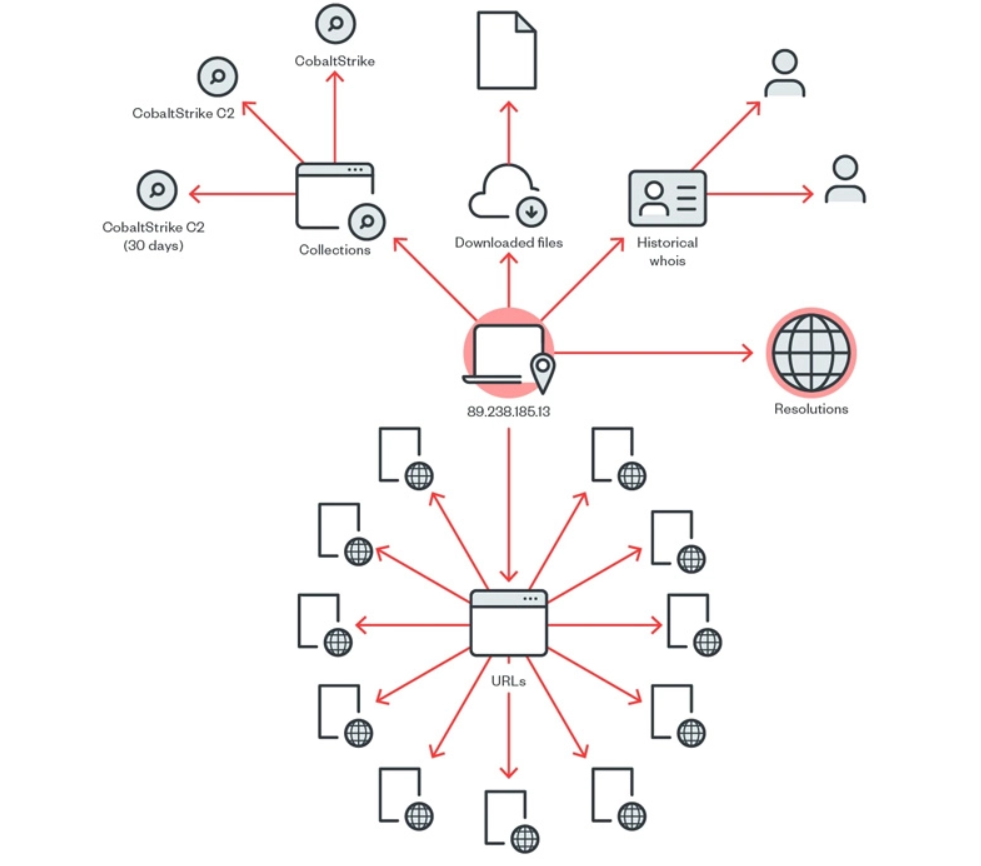
The researchers pointed out that the combination of SEO poisoning and compromised legitimate websites can mask indicators of malicious activity that would normally put users on guard. The ZIP file contains a JavaScript file that loads a Cobalt Strike binary, a tool used for post-exploitation activities that run filelessly in memory.
“Gootkit is still active and improving its techniques,” the researchers said. “This implies that this operation has proven effective, as other threat actors seem to continue using it.”
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment