
JSCEAL is a new threat targeting Windows users, mainly people using cryptocurrency apps or accounts with sensitive data.
Check Point Research first reported it in July 2025. Since then, the malware has become stronger and better at avoiding security tools.
A new attack wave in August 2025 shows the malware is improving, using smarter hiding methods and upgraded command-and-control systems.
All about the JSCEAL Malware
JSCEAL spreads through fake ads that lead users to misleading websites. When users click these pages, they unknowingly download installers that look real but are actually malicious.
Once installed, the malware steals important information such as usernames, passwords, and browser data
The attack method is simple but still effective, often surprising security teams.
CATO Networks found that JSCEAL has grown more advanced over time.
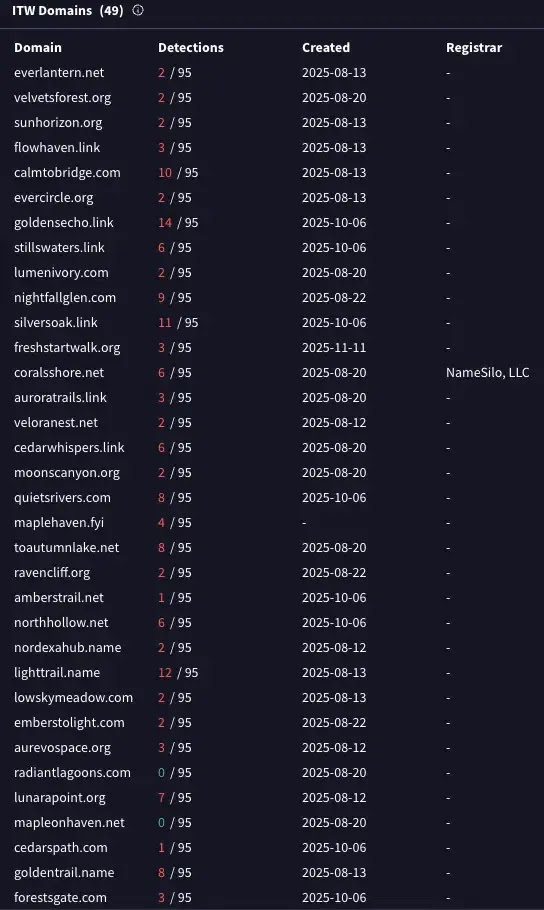
From August 20, 2025, the attackers rebuilt their setup and began using short single-word domains like emberstolight.com to stay hidden.
Advanced Detection Evasion Techniques
The malware now uses smart tricks to avoid being detected. Its command-and-control servers only respond when a specific PowerShell user-agent is used.
If someone tries to check the servers through a normal browser, they are shown fake error messages that look like broken PDF files, making the malware harder to analyze.
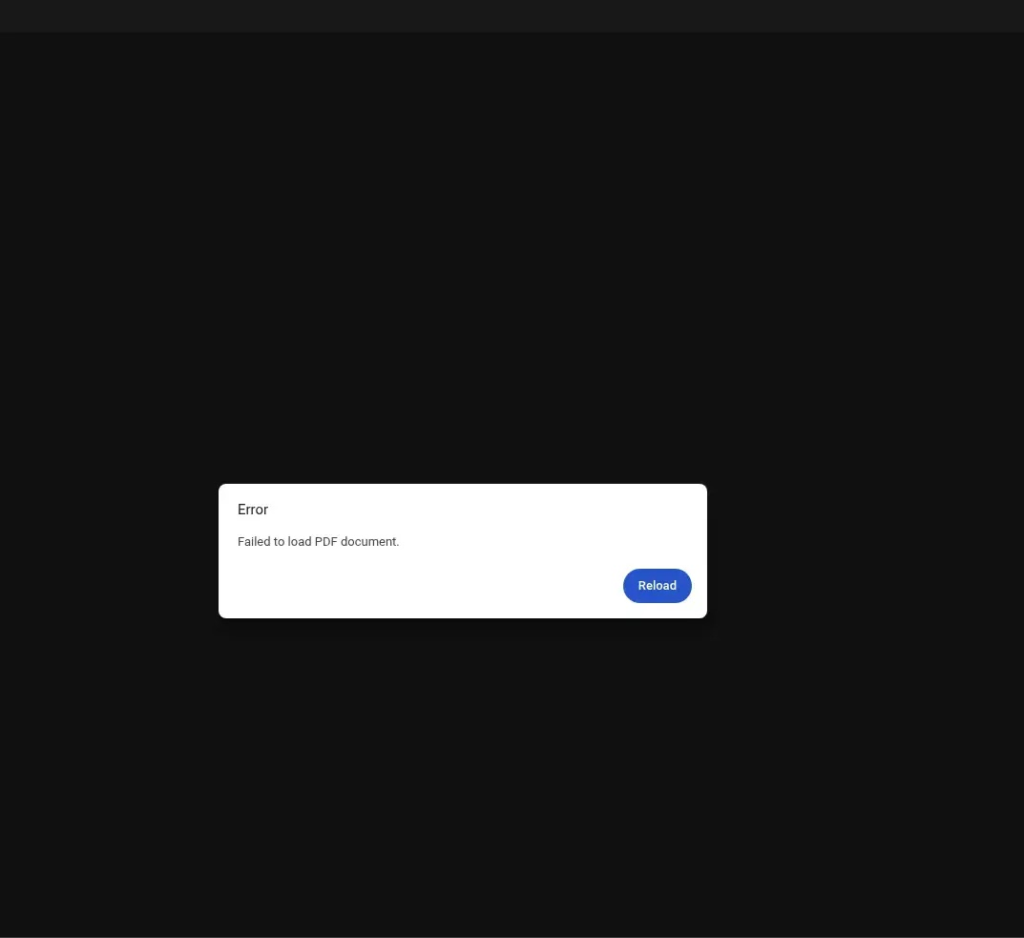
Only systems that pass the checks get the real payload, making analysis difficult. The script confirms a fake PDF response before continuing, and the new PowerShell version now uses Windows Scheduler through COM objects, adding more complexity.
These changes make the malware much harder to detect, and the new payload system supports multiple formats, giving attackers more flexibility.
The threat is still active, so organizations should block suspicious PowerShell activity, watch for unusual command-and-control traffic, and warn users about fake ads. Security teams must stay alert because JSCEAL spreads not through big exploits, but through steady improvements in stealth and design.




