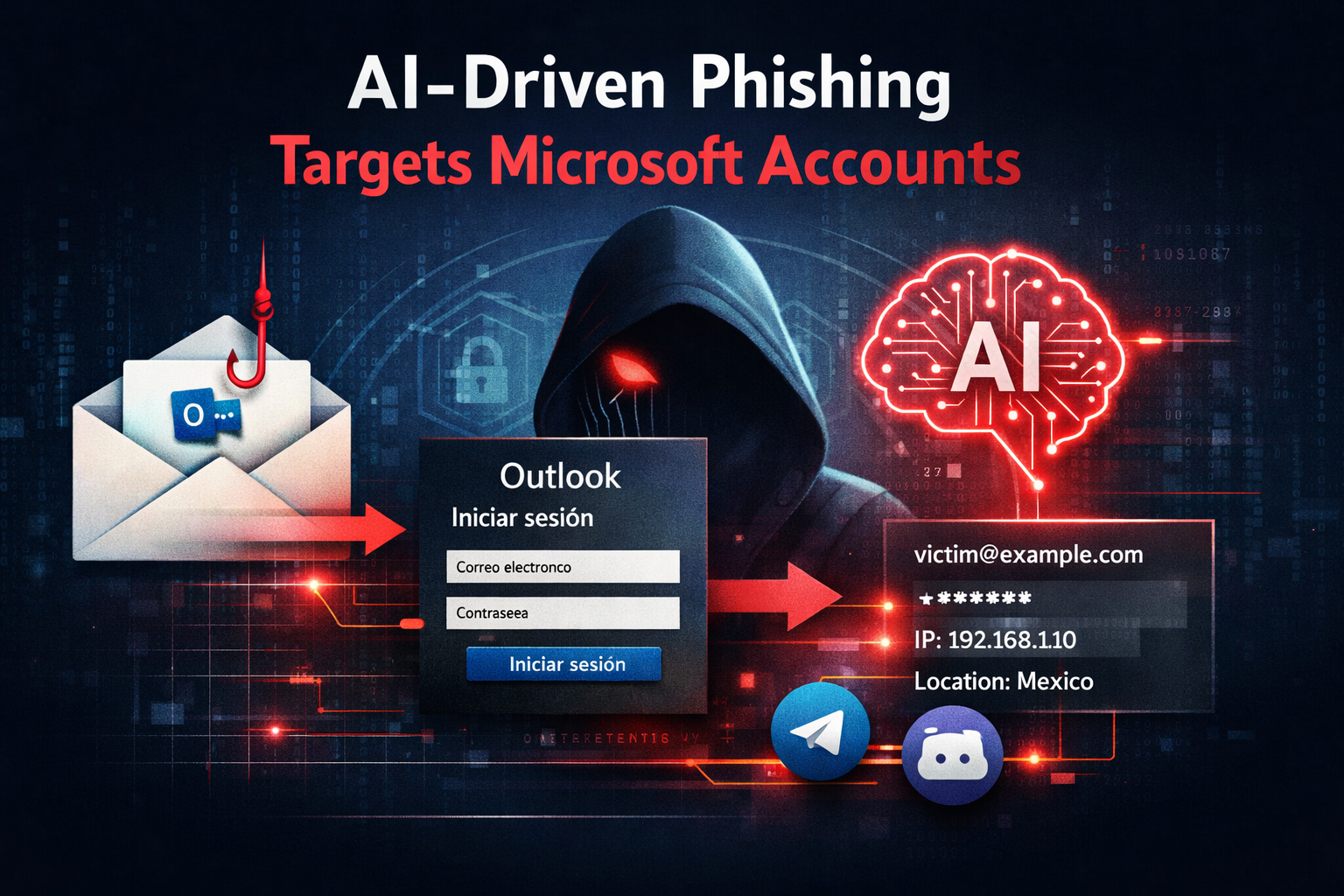
Since March 2025, attackers running a Spanish-language phishing campaign have been going after Microsoft Outlook accounts. The phishing tool they use appears advanced and likely built with help from AI.
AI-Driven Phishing Kit
Researchers track the activity using a small but unusual clue: four mushroom emojis hidden inside the text “OUTL.” So far, this marker has been linked to more than 75 separate attack setups.
The attackers collect stolen email usernames and passwords, along with the victim’s IP address and location. This information is then sent to the attackers using Telegram and Discord.
To trick users, the phishing page copies the Outlook login screen and displays prompts in Spanish, making it look legitimate to victims.
After a victim enters their login details, the phishing tool quickly adds extra context to the stolen data. It checks the user’s IP address using api.ipify.org and pulls location details from ipapi.co.
This data collection happens instantly, before the stolen credentials are sent to the attackers.
The campaign shows careful planning. Even though the attackers change how the code is hidden, the way the operation runs stays mostly the same.
Sage Hollow researchers first spotted the activity by noticing the repeated mushroom emoji marker, which helped them trace more related attacks.
Over time, the phishing kit has appeared in multiple versions. Some use heavy obfuscation and anti-analysis tricks, while others are left completely open and resemble AI-generated code. The latest version, disBLOCK.js, uses clean formatting, clear function names, and Spanish comments explaining each step — signs that the code was likely generated with AI rather than written fully by hand.
How the Phishing Kit Works
The phishing tool is designed with separate pieces, keeping its settings away from the main logic. In earlier versions, a file called xjsx.js was used to store Telegram bot details with only basic hiding techniques.
When someone enters their login details on the fake page, the tool runs through a set process. It checks whether the email address is valid, then reaches out to external services to collect IP and location information.
All stolen data is bundled into a standard message format and sent over regular HTTPS connections. The attackers use either Telegram bots or Discord webhooks to receive this information.
Newer samples rely more on Discord webhooks because they work as one-way channels. Even if the link is discovered, past data cannot be viewed.
This setup points to a shared phishing platform, where multiple attackers reuse the same toolkit across different campaigns.
Security Recommendations
- Organizations should enable phishing-resistant MFA on Microsoft accounts to reduce the impact of stolen passwords.
- Email gateways should be tuned to detect look-alike Outlook login pages and block messages that redirect users to external authentication sites.
- Security teams should monitor outbound traffic for suspicious connections to Telegram bot APIs and Discord webhooks, especially from user workstations.
- User awareness remains critical. Employees should be reminded to verify login pages and avoid entering credentials through email links.
- Incident response teams should reset affected credentials immediately and review sign-in logs for abnormal locations and IP addresses.




