In 2022, HardBit Ransomware 4.0 emerged, differing from typical groups by avoiding leak sites and double extortion. Their tactics include data theft, encryption, and ransom demands with additional threats. Cybereason researchers found HardBit actively using passphrase protection to evade security measures.
HardBit Ransomware
They communicate via TOX, a peer-to-peer messaging system. While their initial infection method is unclear, they resemble LockBit Ransomware. Their TTPs include RDP and SMB brute-forcing, credential theft with Mimikatz and NLBrute, and possibly using LaZagne and NirSoft tools.
They are known to download programs from picofile[.]com, a Farsi file-sharing site.
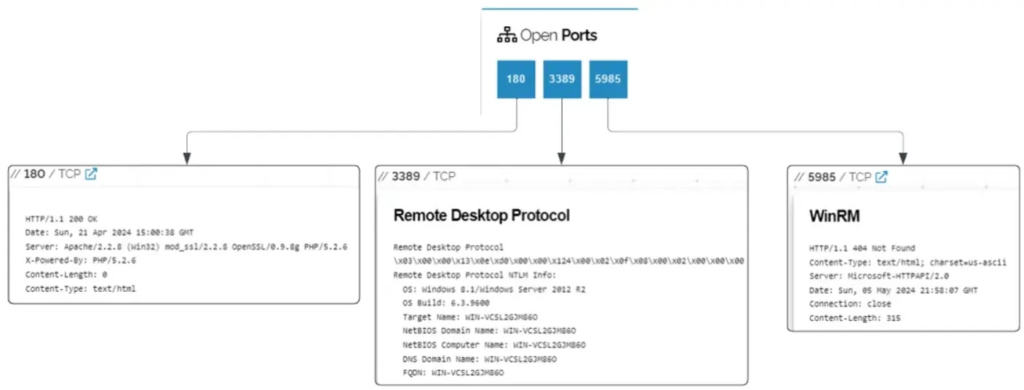
Threat actors used network discovery tools like Advanced Port Scanner and KPortScan 3.0 to move through RDP, reports Cybereason. They installed HardBit ransomware bundled with the Neshta virus, which corrupts files and maintains the infection.
HardBit ransomware requires an authorization ID and encryption key, disables Windows Defender, stops services, and prevents system recovery using BCDEdit, Vssadmin, WBAdmin, and WMIC before encrypting files.
Binary unpacking is key to HardBit ransomware, involving file infection and system manipulation to ensure execution and prevent recovery.
HardBit selectively encrypts files, updates infected machines, and uses encrypted email contacts, obfuscated with Ryan-_-Borland_Protector Cracked v1.0, a modified ConfuserEx.
The GUI version offers ransom and wiper modes, with wiper mode requiring additional authorization via the hard.txt file.
HardBit has evolved through versions 2.0, 3.0, and 4.0, increasing in sophistication and obfuscation techniques.
Recommendations
- Enable Application Control to block execution of malicious files.
- Activate Predictive Ransomware Protection.
- If Predictive Ransomware Protection is unavailable, enable Anti-Ransomware.
- Enable Variant Payload Prevention on your security solution with Prevent mode
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!








Leave A Comment