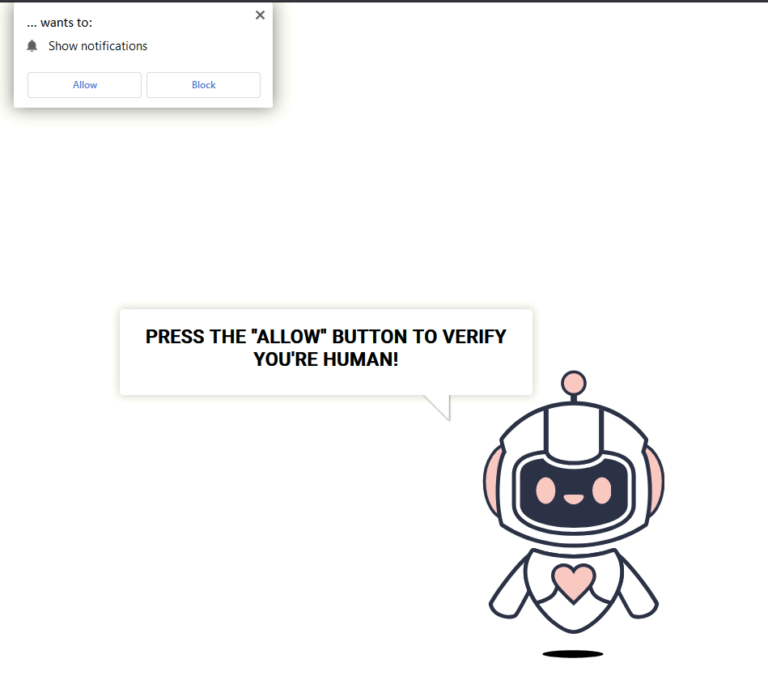
CAPTCHAs, or Completely Automated Public Turing tests, are used online to verify users are human, not bots....
malicious cyber actors
A critical vulnerability in TeamViewer’s Windows Remote client, CVE-2024-7479 and CVE-2024-7481, allows attackers to elevate privileges on...
Cisco revealed a critical vulnerability, CVE-2024-20439, in its Smart Licensing Utility, allowing unauthorized access due to a...
A new malware campaign is gaining traction online, using fake CAPTCHA sites to trick users into installing...
A threat actor has allegedly claimed a breach of Federal Bank, exposing sensitive data of hundreds of...