
Threat actors are using a new attack method that combines ClickFix social engineering with image steganography to hide malware inside PNG image files.
This technique, identified by Huntress researchers, marks a shift in how information-stealing malware is delivered to victims.
ClickFix works as a multi-step attack that tricks users into running malicious commands themselves. Victims are shown convincing fake pages, such as robot verification checks or Windows Update alerts.
These pages instruct users to press Win + R, open the Run box, and paste a command that is secretly copied to their clipboard.
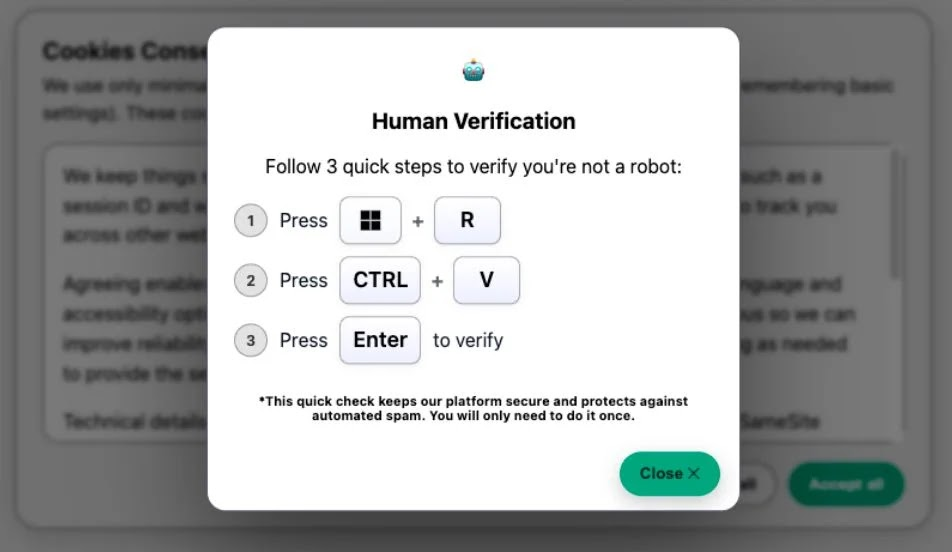
Once the command is executed, it starts a chain of actions that eventually installs malware on the system.
Researchers first observed this activity in October 2025. Early campaigns used simple “human verification” lures, but newer attacks now rely on realistic fake Windows Update screens that appear in full screen, display update animations, and then prompt users to run the ClickFix command.
Hidden Malware in PNG Images
The attackers hide malware directly inside PNG image pixels instead of attaching files. The hidden code is stored in color values, mainly the red channel, and is extracted and executed in memory, making detection difficult.
The attack starts with an mshta.exe command that launches a PowerShell loader. This loader decrypts and loads a hidden .NET component directly into memory.
The component extracts malware hidden inside a PNG image by reading pixel data, mainly the red color channel, to recover the shellcode. The final payload is packed with Donut, allowing it to run in memory without touching disk.
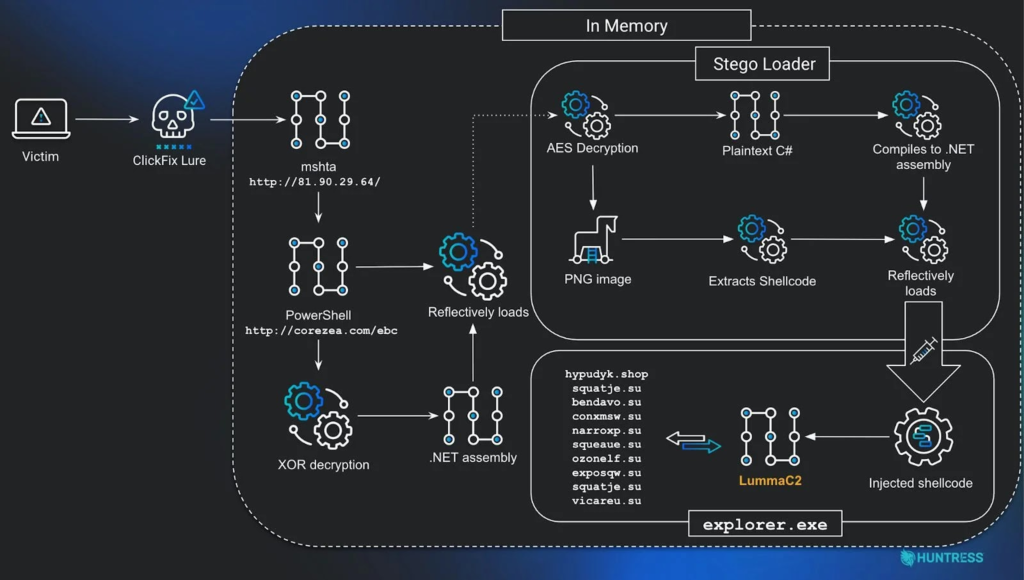
Security analysts have confirmed that the attack eventually installs well-known data-stealing malware, including LummaC2 and Rhadamanthys. These tools are commonly used to collect login details, browser data, and financial information from infected systems.
What makes this campaign stand out is the way the malware is delivered. Instead of using traditional executable files, the attackers hide their code inside image data, allowing it to slip past many detection systems that rely on known file patterns.
Even with these advanced tricks, the attack still depends on one basic factor: user action. Victims are persuaded to run commands themselves, giving the malware a clear path onto the system.
To lower the risk, organizations should reinforce security awareness and limit unnecessary system features such as the Windows Run command, which is commonly abused in these attacks.
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!




