
Cyber security and data privacy protection concept with icon of a shield and lock over binary digits background
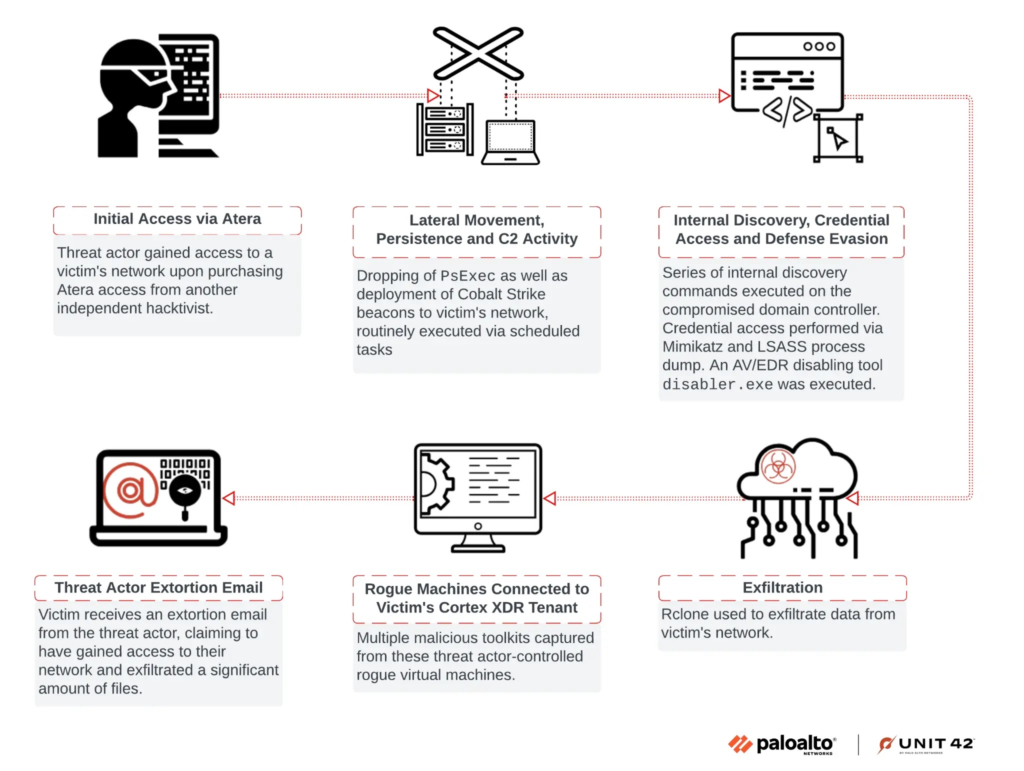
Palo Alto Networks’ Unit 42 recently found that hackers are using AV and EDR bypass tools from cybercrime forums to evade endpoint security.
EDRSandBlast
An extortion probe revealed two outdated Cortex XDR endpoints testing an AV/EDR bypass tool called “disabler.exe”—a modified “EDRSandBlast” used to disable security hooks in user-mode libraries and kernel-mode callbacks.
The investigation uncovered a virtual machine (hostname: DESKTOP-J8AOTJS) loaded with advanced attack tools like Mimikatz (for stealing credentials), shellcode generators, kernel driver utilities, and code obfuscation tools.
Noteworthy files included “ContiTraining.rar,” containing leaked Conti ransomware playbooks, as well as links to cybercrime forums XSS and Exploit, associated with a user named “Marti71” and “KernelMode.”
The analysis of the system revealed connections to domains such as ‘temp.vxsh.net’ (used for fake AV/EDR tokens) and signs of tool testing through ‘Oracle VM VirtualBox.’
The threat actor’s operational security was compromised by artifacts like a Kazakhstan-based P-1 form, browser history showing visits to ya.ru and sourceforge.net, and video recordings made with OBS Studio that displayed the use of “WinBox” (a Mikrotik router administration tool) under a username beginning with “Andry.”
The endpoints had a “Z:\freelance” directory, linking various criminal affiliates and their tools. The investigation revealed a sophisticated cyber attack resembling Conti ransomware tactics, with key indicators including:
- Atera for initial access and persistence
- Cobalt Strike beacons (watermark ID: 1357776117) for C&C
- PsExec for lateral movement
- Rclone for data theft
The Cobalt Strike configuration analysis revealed links to around 160 unique IPs and domains, some overlapping with “Dark Scorpius” (aka “Black Basta”) ransomware.
The investigation’s breakthrough came with the discovery of a compromised system, “DESKTOP-J8AOTJS,” containing AV/EDR bypass tool videos and a P-1 expense form. These operational security slips led investigators to identify “Andry” from Kazakhstan, who uses the alias “KernelMode” on cybercrime forums.
This individual is thought to develop sophisticated AV/EDR bypass tools sold through subscription models in underground markets, though direct links to the network intrusion are unclear. The attack’s complexity suggests it was interrupted before completion, highlighting modern cyber threats that blend automation with human expertise.
Indicators of Compromise
Host Based
SHA256 hash:
3758c5eb1fbab2362ef23091f082710606c1b4ebaeaff9b514896dc2a1e2ab17
File name: disabler.exe
File description: AV/EDR bypass tool based on EDRSandBlast
SHA256 hash:
1228fd70d7ce0f31f7e7c98520e66a01935e428be561ce0d25140ba33598f688
File name: 0bffbb8.exe
File description: Cobalt Strike beacon
SHA256 hash:
6106d1ce671b92d522144fcd3bc01276a975fe5d5b0fde09ca1cca16d09b7143
File name: WNBIOS.sys
File description: Vulnerable driver loaded by disabler.exe
SHA256 hash:
6106d1ce671b92d522144fcd3bc01276a975fe5d5b0fde09ca1cca16d09b7143
File name: WN_64.sys
File description: Vulnerable driver loaded by disabler.exe
SHA256 hash:
14364f1969b83cf4ec2c0e293c6b4d8f750932f6cbf9a8f32173400de33469fd
File name: abased.dll
File description: Cobalt Strike beacon
SHA256 hash:
264a29a703682456ebe9f679a0e7d18291af84ef4b53a669c2555061e4972394
File name: vm32.dll
File description: Cobalt Strike beacon
SHA256 hash:
61c0810a23580cf492a6ba4f7654566108331e7a4134c968c2d6a05261b2d8a1
File name: mimikatz.exe
File description: Mimikatz credential access tool
SHA256 hash:
8d36705a5b7f6179fdef2d600276f9c0cc6cb3b0a670c11d66baaaea6bd2c8ad
File name: mimik.zip
File description: Archive that contains mimikatz.exe
SHA256 hash:
41f32a3d67b3f983c82070e067a121dd5b8fae2804c97e684acc7f599ba308da
File name: safetykatz.exe
File description: SafetyKatz, modified version of Mimikatz
SHA256 hash:
6e37a054bd7c49b233cace747951911f320bd43be8a79ce455b97403c2f7de2c
File name: mmk.exe
File description: Mimikatz credential access tool
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




