Hackers group Lebanese Cedar attack unpatched Atlassian servers at telcoms, Hosting and ISPs providers.
Lebanese Cedar
A volatile hacker group “Lebanese Cedar” linked to Lebanese Hezbollah Cyber Unit, has more advanced technological skill than previously thought.
Over the past decade, companies in the US, UK, Egypt, Jordan, Lebanon, Israel have been targeted by this group.

Israeli cybersecurity firm — ClearSky in a report on Thursday, found at least 250 web servers have been hacked by the group.
However, Lebanese Cedar group focus on collecting intelligence and stealing company databases with sensitive information.
In addition, the information includes:
- client call records
- and, private data in the case of telecommunications companies.
Attack Workflow:
Clearsky researchers said the attacks followed a simple pattern.
According to the researchers, threat actors used open-source hacking tools to scan the internet for unpatched Atlassian and Oracle servers.
In follow, hackers performed exploits to gain access to the server and install a web shell for future access.
And, Web shells such as:
- ASPXSpy
- Caterpillar 2
- Mamad Warning
- and, an open-source tool named JSP file browser (which can also function as a web shell).
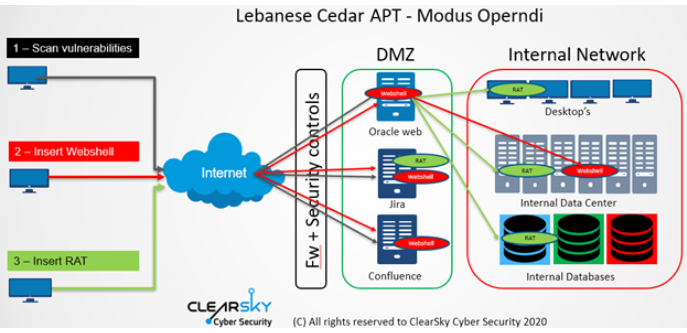
After that, Lebanese Cedar deployed the payload of Explosive RAT into the victims’ network.
According to ClearSky, Lebanese Cedar is the only known threat actor that uses this code, which comes with capabilities to record keystrokes, capture screenshots, and execute arbitrary commands.
Clearsky said the hackers used three flaws in the servers such as:
- CVE-2019-3396 in Atlassian Confluence
- CVE-2019-11581 in Atlassian Jira
- CVE-2012-3152 in Oracle Fusion
Indicators Of Compromise:
ClearSky Lebanese Cedar report’s PDF contains data including indicators of compromise and more technical details.
Hash Values:
| MD5 | File Name | Type |
| webshell | ||
| 33AF1CD4585DA9ED804068B2A45FC8B4 | 404.aspx | Caterpillar 2 |
| 6BA944E9D3D96A46509204CD06EA2B11 | 405.aspx | Caterpillar 2 |
| 61F46FA93083D3A160AC8356FBC15722 | – | Caterpillar 2 – ITSec Team |
| 150DC0141B8A0010BB5A82419B3293EB | – | ASPXSpy |
| 7D58573B98597A010597423652AE3394 | – | ASPXSpy |
| F30F2184ED83929CF96157BC91210DAA | Mamad.aspx | Mamad Warning |
| 8ED3D1CADC4C2251EC606B9D6EB5D272 | – | Caterpillar 2 |
| 2D804386DE4073BAD642DFC816876D08 | – | Caterpillar 2 |
| 2ADF71947E977B85E269D5962243215C | – | SharPyShell |
| 93448B89C592985E22F60AB0D654787D | CV.php | Adminer |
| 2D804386DE4073BAD642DFC816876D08 | – | File Browser JSP |
| 39887492C5C70977C0C0CF0AA0E7154B | test.jsp | File Browser JSP |
| Explosive RAT | ||
| a97fdcb6493c2012aeebdeef0e09625a | Communicate.DLL | dll |
| 1316d35f6472eb323ae2c8b75199fbb5 | spmpm.dll syslib.tmp | dll |
| 09a0970bfc1bc8acec1ec609d8d98fda | Mir.exe | exe |
| fef76a8027e07c7a51b312a26c488653 | dzip | exe |
| 902bcc27ed86bc623e20532239895da7 | 917951-f2030832.dll | dll |
| 8ac64a171736252b81c4a559df1f9bae | – | |
| 65954b4c60031fb857a09761497ff641 | rspr | |
| 4147d6beb17b507a5df345dae5f15c41 | symlock | |
| 544fdcce998fc7f4bb2914b3ec5b4761 | symlock | |
| 1aebf9d07fe6e82d97e062cdbe656a36 | wzip | |
| 5d1f75bfc7cbd96891f26b1041fd5994 | wzip | |
| b54346cdaf9556eb88f3d95e0bad2be5 | wzip | |
| 1aebf9d07fe6e82d97e062cdbe656a36 | vwupd.tmp | |
| e9f0260409c6c964985fa4df926d7e04 | wsinhelpd | |
| 3188df195d09ee38d89707501e330c2f | dllhost.exe wvwupd.exe | exe |
IP Address:
- 68.65.122[.]109
- 74.208.73[.]149
- 191.101.5[.]183
- 198.101.242[.]72
- 169.50.13[.]61












Greate article. Keep posting such kind of information on your site.
Im really impressed by your site.
Hello there, You’ve performed an incredible job. I’ll definitely
digg it and in my view suggest to my friends. I am sure they will be benefited from this web site.