Progress is notifying customers about a newly discovered critical SQL injection vulnerability, identified as CVE-2023-36934, in its MOVEit Transfer software.
MOVEit Transfer
The software at the center of the recent massive Clop ransomware breach, MOVEit Transfer, has been updated to address a critical SQL injection bug along with two additional vulnerabilities of lesser severity.
The SQL injection vulnerabilities enable attackers to manipulate queries in order to gain unauthorized access to a database or manipulate its contents by executing malicious code. These attacks exploit the absence of adequate input/output data sanitization in the targeted application.
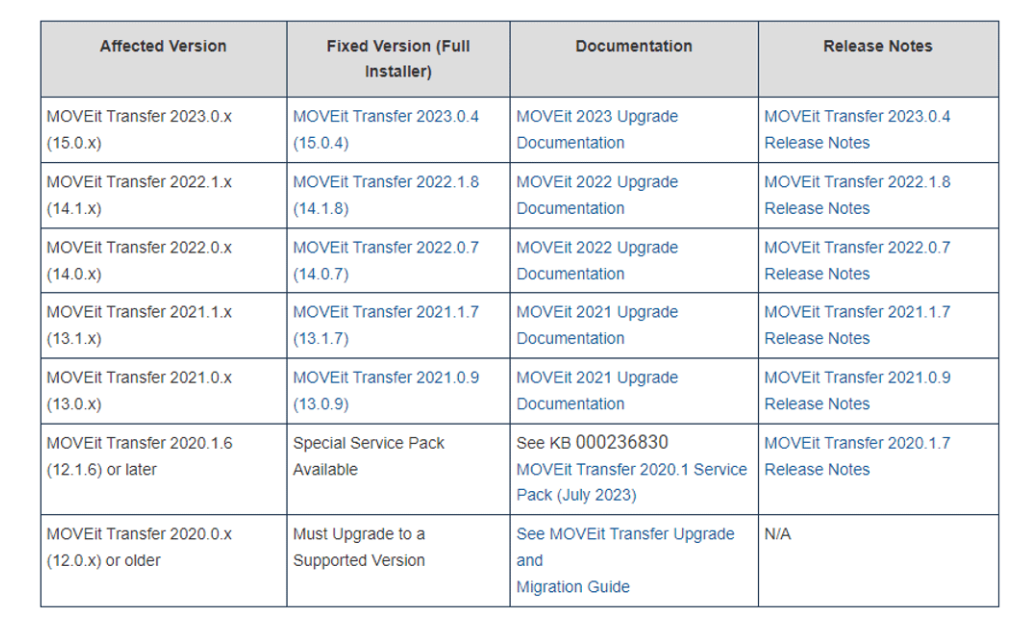
The two SQL injection security issues impact various versions of MOVEit Transfer, including:
- Versions 12.1.10 and earlier
- Versions 13.0.8 and earlier
- Versions 13.1.6 and earlier
- Versions 14.0.6 and earlier
- Versions 14.1.7 and earlier
- Versions 15.0.3 and older.
The second SQL injection flaw, identified as CVE-2023-36932, received a high severity rating because an attacker could exploit it after authentication.
A third vulnerability addressed by this patch is CVE-2023-36933, a high severity issue that allows attackers to cause an unexpected program termination.
In response to the significant impact of the security incident, the American software company has made the decision to implement a proactive measure by introducing monthly security updates known as “Service Packs.”
This new approach enhances the software upgrade process, enabling MOVEit Transfer administrators to apply fixes more efficiently and promptly than previous methods.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment