Cyber-attacks against two separate entities related to COVID-19 research.
Lazarus group
A threat group, active since at least 2009 — attributed to the North Korean government.
Notably, the group responsible for the November 2014 attack against Sony Pictures Entertainment — Operation Blockbuster by Novetta.
Lazarus attacks in September and October 2020, targeted a Ministry of Health and a pharmaceutical company, Kaspersky reveals.
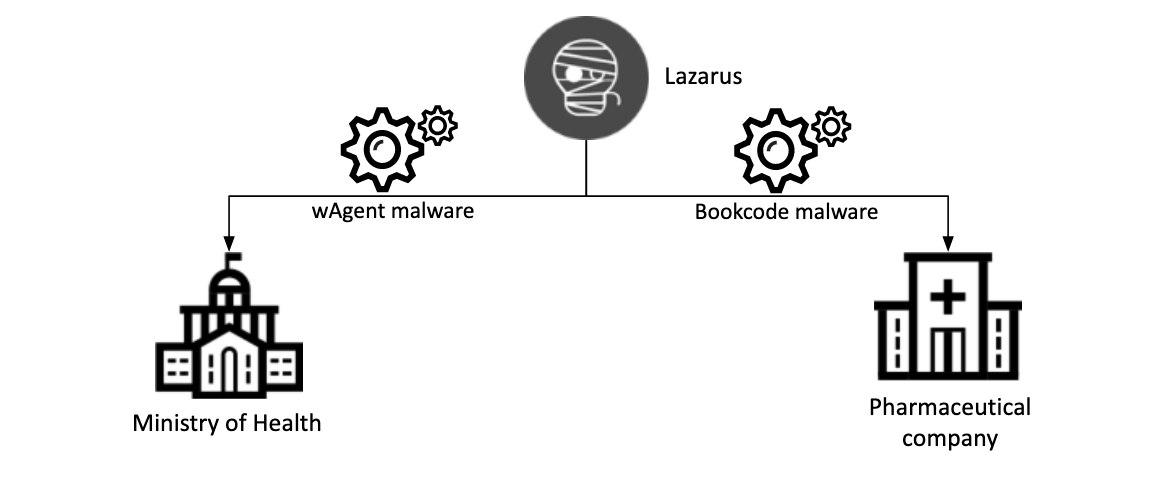
Moreover, they authorized to produce and distribute COVID-19 vaccines, revealing Lazarus’ interest in COVID-19 research.
Importantly, the pharmaceutical company with the BookCode malware, Ministry of Health body with the wAgent malware.
Previously, the malware used to target cryptocurrency businesses.
Tactics, Techniques, and Procedures
Threat actors used different Tactics, Techniques, and Procedures (TTPs) on this attack.
But Kaspersky is highly confident that Lazarus was behind both incidents, functioned — both boasting a full-featured backdoor.
The closer analysis found that the same infection scheme as Lazarus’ had public health officials on previous attacks on cryptocurrency businesses.
wAgent Malware:
Using the wAgent backdoor, the operator installed an additional wAgent payload that has a persistence mechanism.
Importantly, The attackers executed various shell commands to gather information from the victim machine.
An additional payload that included a persistence mechanism was also deployed on two Windows servers, and the full-featured backdoor followed.
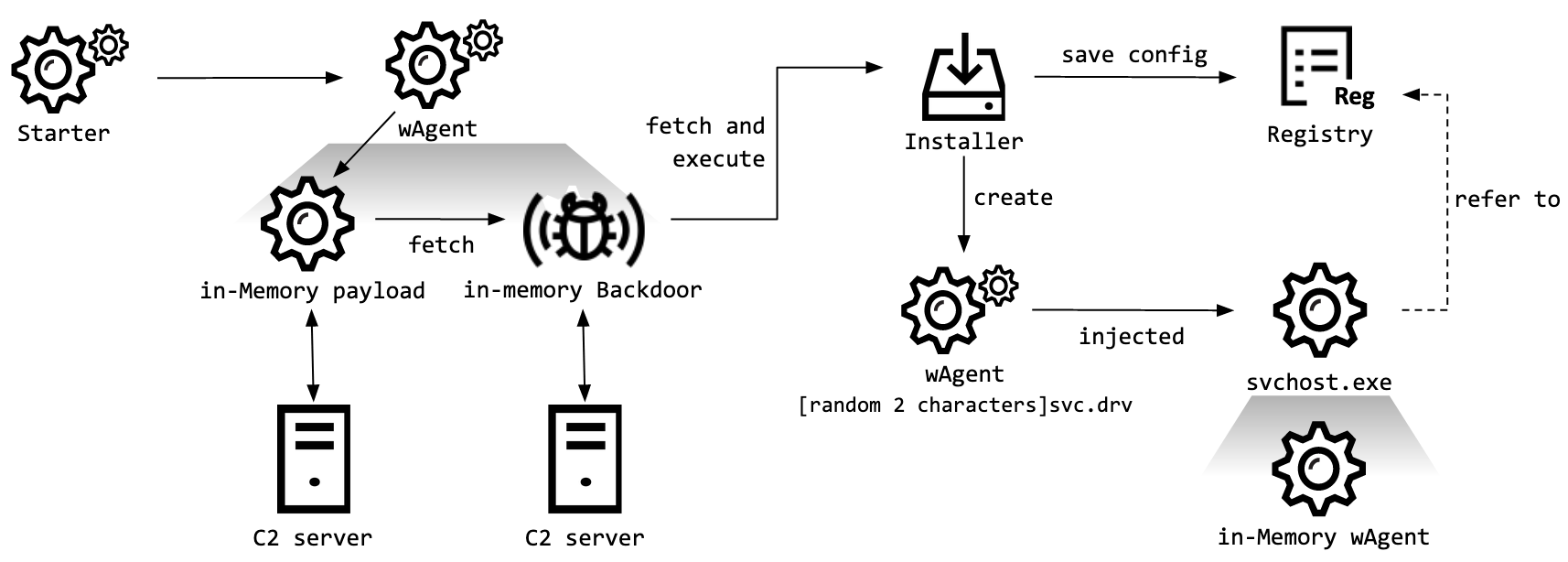
However, The C2 addresses of wAgent malware:
- hxxps://iski.silogica[.]net/events/serial.jsp@WFRForms.jsp@import.jsp@view.jsp@cookie.jsp
- hxxp://sistema.celllab[.]com.br/webrun/Navbar/auth.jsp@cache.jsp@legacy.jsp@chooseIcon.jsp@customZoom.jsp
- hxxp://www.bytecortex.com[.]br/eletronicos/digital.jsp@exit.jsp@helpform.jsp@masks.jsp@Functions.jsp
- hxxps://sac.najatelecom.com[.]br/sac/Dados/ntlm.jsp@loading.jsp@access.jsp@local.jsp@default.jsp
Bookcode Malware
The malware used to gather the following:
- system information
- network information from the victim environment,
- also, along with a registry SAM dump containing password hashes.
Importantly, The adversary also attempted to collect information on other machines on the network, likely for lateral movement.
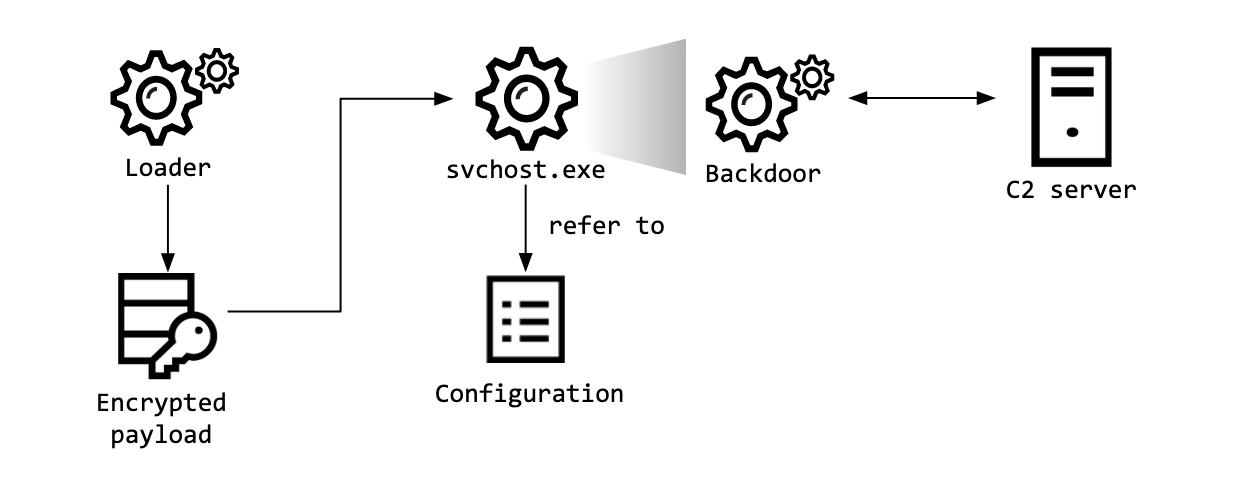
Most importantly, Bookcode cluster has its own unique TTPs, and the same modus operandi was used in this attack.
- Extracting infected host information, including password hashes, from the registry sam dump.
- Using Windows commands in order to check network connectivity.
- Also, Using the WakeMeOnLan tool to scan hosts in the same network.
In addition, during analysis it contains four C2 servers:
- hxxps://www.kne.co[.]kr/upload/Customer/BBS.asp
- hxxp://www.k-kiosk[.]com/bbs/notice_write.asp
- hxxps://www.gongim[.]com/board/ajax_Write.asp
- hxxp://www.cometnet[.]biz/framework/common/common.asp
“We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyber-attacks,” said Park, a security expert at Kaspersky.
For more IOC — Lazarus covets COVID-19-related intelligence | Securelist












A motivating discussion is definitely worth comment.
I do think that you need to write more on this topic, it might not be a taboo subject but usually folks don’t speak about such issues.
To the next! Many thanks!!
Excellent way of describing, and fastidious post
to obtain data regarding my presentation subject, which i am going
to present in academy.