Oracle fixed a vulnerability as attackers started targeting servers running on Oracle WebLogic instances, vulnerable to a critical flaw that allows attackers to take control of the system without authentication.
Oracle WebLogic:
WebLogic Server is a unified and extensible platform for developing, deploying and running enterprise applications, such as Java, for on-premises and in the cloud.
As part of a massive quarterly “Critical Patch Update” (aka “CPU”), Oracle patched CVE-2020-14882 in WebLogic with a CVSS score of 9.8.
Vulnerable WebLogic versions:
- 10.3.6.0.0
- 12.1.3.0.0
- 12.2.1.3.0
- 12.2.1.4.0 and
- 14.1.1.0.
In an advisory today, Johannes Ullrich, Dean of Research at SANS, says that exploit attempts on the honeypots came from the following IP addresses:
- 114.243.211.182 – assigned to China Unicom
- 139.162.33.228 – assigned to Linode (U.S.A.)
- 185.225.19.240 – assigned to MivoCloud (Moldova)
- 84.17.37.239 – assigned to DataCamp Ltd (Hong Kong)
111.206.250.0/24 and 27.115.124.0/24 (multiple hosts in these netblocks) verifying vulnerability by attempting to download a page from *.o3oant.k2x.pw. The DNS lookup triggered by the request attempt is used to verify a vulnerability. The site itself does not exist (and not resolve).
SANS Institute is in the process of alerting the corresponding Internet Service Provider (ISP) on the IP addresses above.
Except the IP address assigned to MivoCloud, other IP addresses are just trying to ping, where 185.225.19.240 attempting to execute “cmd /c” .
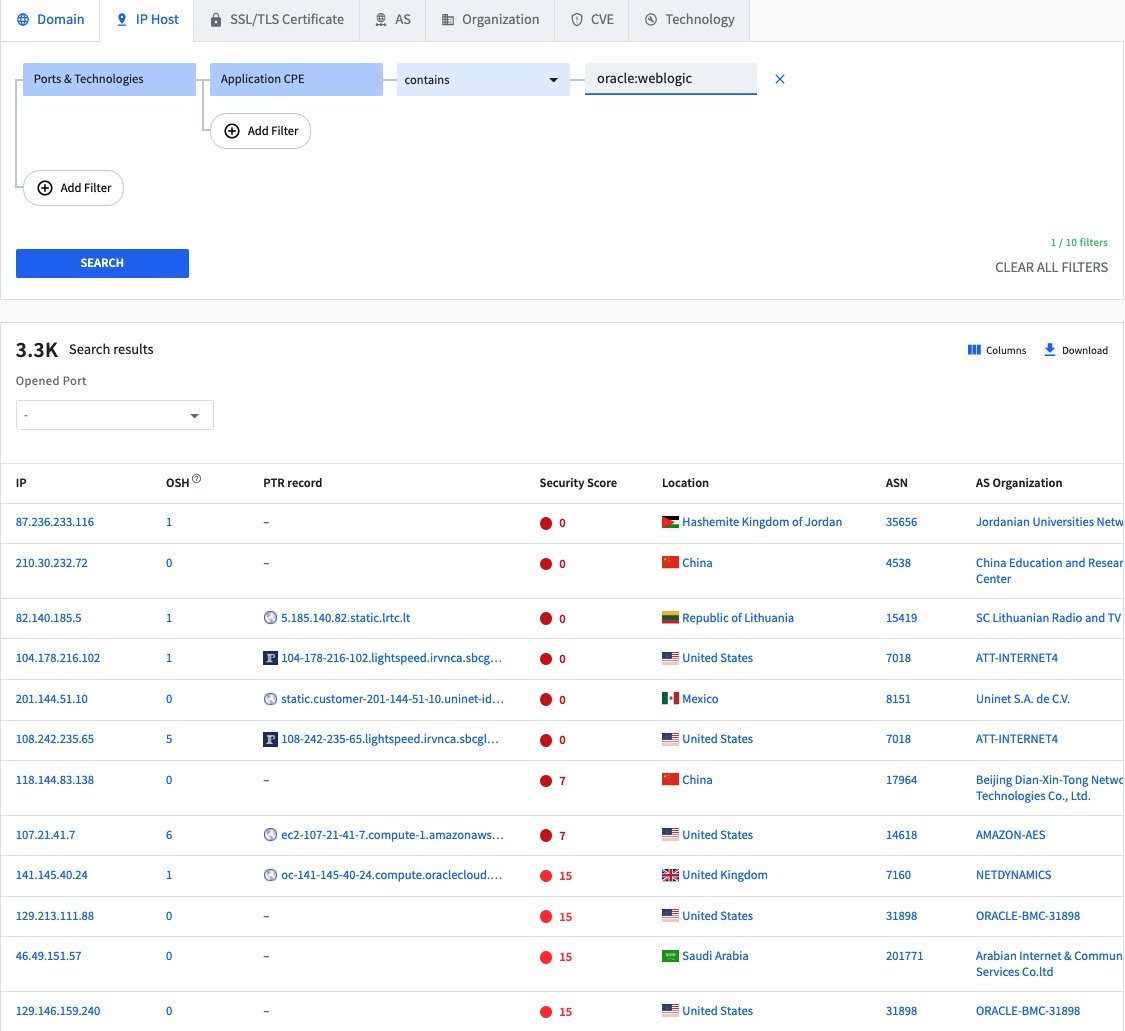
Above all, a search on Spyse engine for scanning and collecting reconnaissance information from exposed assets shows that there are more than 3300 of IP addresses exposed to CVE-2020-14882. The attacks observed by SANS come a little over a week after Oracle released a patch for it. In short, this should come as no surprise, though, considering how trivial it is to exploit, its critical severity, and that exploit code is publicly available.
If you find a vulnerable server in your network: Assume it has been compromised. Applying the patch is currently the best solution to protect against these attacks.













Hello Sir or Ma’am lately I have been wondering how vigilant you are opposed to google with name directories to find people…..I have many friends focused on even so much as their name being cyber manipulated, namely a poor addict girl René Lynn Johnson 28 from Utah, please email me with such data if Oracle can provide it :)…..