
The OWASP ZAP project has introduced a new add-on that brings the OWASP Penetration Testing Kit (PTK) directly into browsers opened through ZAP. The current release, version 0.2.0 (alpha), removes the need for separate browser extension setup during testing.
OWASP ZAP Releases New Penetration Testing
By embedding PTK into ZAP-controlled browser sessions, testers get immediate access to multiple application security testing capabilities, including dynamic and interactive testing, dependency analysis, and practical browser tools like token and cookie inspectors.
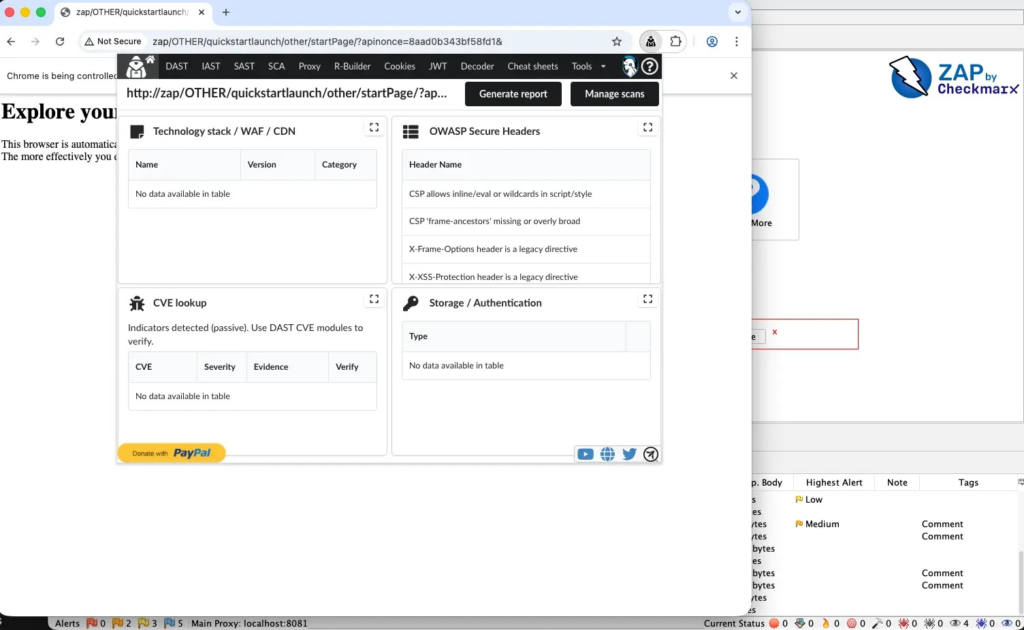
The add-on is available through the ZAP Marketplace and automatically loads PTK when launching Chrome, Edge, or Firefox via ZAP. Testers can start interacting with applications right away, while ZAP continues to capture traffic, build the site structure, and manage sessions in the background.
This integration simplifies web application security testing by keeping both proxy-based analysis and browser-level testing tools in a single workflow.
PTK allows security testing to happen alongside normal application use. Testers can move through key pages and workflows while scans run in the background, then pause testing to review the results.
This method is especially effective for modern web applications that rely on user interaction, such as SPAs. Scan behavior can be adjusted to reduce impact on live environments, and results are shared back into ZAP so issues can be validated and re-tested easily.
PTK also observes how applications behave inside the browser during use. By collecting runtime signals while users navigate authenticated areas, it helps identify issues related to client-side logic, rendering, and dynamic content.
This browser-first approach gives testers better context without breaking their workflow, making it easier to understand issues that only appear during real user interaction.
PTK adds several browser-based security checks that work directly on live applications. It can review scripts loaded on a page, identify risky patterns, and highlight dependency issues without needing access to the source code.
Testers can quickly modify and replay captured requests, adjust headers, and test authentication tokens and cookies to see how applications handle changes. This helps validate access controls, session handling, and token enforcement during real use.
A typical workflow starts by logging in through a ZAP-proxied browser, running PTK checks while navigating the app, and then validating findings using ZAP’s traffic and history view.
This tight integration keeps testing focused, efficient, and well suited for modern, dynamic web applications.




