What is Shadow Volume Copies?
Shadow Copy is a technology included in Microsoft Windows that can create backup copies or snapshots of computer files or volumes, even when they are in use. It is implemented as a Windows service called the Volume Shadow Copy service.
vssadmin.exe:-
Vssadmin is a default Windows process that controls volume shadow duplicates of the documents on a given PC. By default, Windows will attempt to create new Shadow Volume snapshots of your C: drive every day.
vssadmin.exe in Windows that allows an administrator to manage the Shadow Volume Copies that are on the computer.
Unfortunately, with the rise of Crypto Ransomware, this tool has become more of a problem than a benefit and everyone should disable it.
Ransomware Vaccine – Raccine:-
A new ransomware vaccine program has been created that terminates processes that try to delete volume shadow copies using Microsoft’s vssadmin.exe program.
As ransomware infections do not want victims to use this feature to recover files for free, one of the first things they do when executed is to delete all Shadow Volume copies on the computer.
One method of deleting Shadow Volumes is to use the following vssadmin.exe command:
vssadmin delete shadows /all /quietThis weekend, security researcher Florian Roth released the ‘Raccine’ ransomware vaccine that will monitor for the deletion of shadow volume copies using the vssadmin.exe command.
“We see ransomware delete all shadow copies using vssadmin pretty often. What if we could just intercept that request and kill the invoking process? Let’s try to create a simple vaccine,” Raccine’s GitHub page explains.
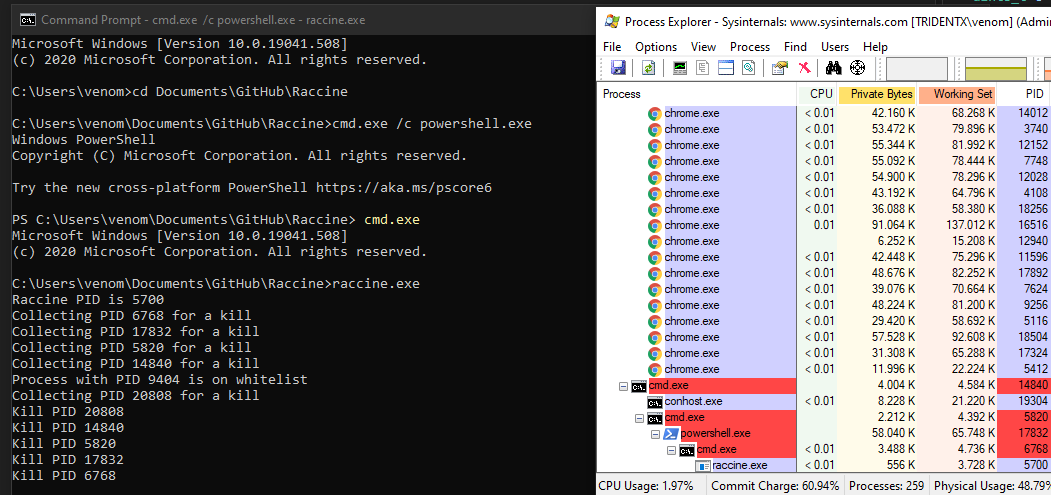
raccine.exe and watch the parent process tree dieOnce raccine.exe is registered as a debugger, every time vssadmin.exe is executed, it will also launch Raccine, which will check to see if vssadmin is trying to delete shadow copies.
Malicious combinations:
deleteandshadows(vssadmin)resizeandshadowstorage(vssadmin)deleteandshadowcopy(wmic)
If it detects a process is using ‘vssadmin delete,’ it will automatically terminate the process, which is usually done before ransomware begins encrypting files on a computer.
Install Raccine, and if you find that it is terminating legitimate programs that you use, you can uninstall it by running the raccine-reg-patch-uninstall.reg registry file and deleting C:\windows\raccine.exe, where it no longer detect and terminate processes that delete shadow volume copies using vssadmin.exe













Leave A Comment