Microsoft SQL servers are succumbing to FARGO ransomware, security researchers at AhnLab Security Emergency Response Center (ASEC) have warned.
Cybersecurity researchers from AhnLab Security say that the newly detected malware variant is an imposter of a past variant named GlobelImposter and starts circulating after Cobalt Strike Beacons are dropped onto the victim machines.
FARGO Ransomware
According to ASEC’s security experts, Fargo is one of the most dangerous and popular forms of ransomware among attackers of Microsoft SQL servers. The ransomware variant is also known as Mallox, as it tends to attach the .mallox extension during file encryption.
The ransomware encrypts the data located on the victim’s computer using a combination of ChaCha20, AES-128, and Curve25519 algorithms. It then displays a message that demands payment in Bitcoin to decrypt the data.
FARGO ransomware is injected into a Windows process called AppLaunch[.]exe, in which it tries deleting some registry keys and ends other database tasks. It also deactivates recovery with a command.
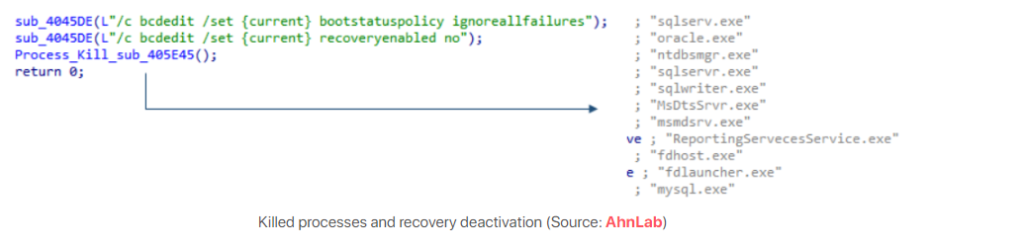
After this, the cybercriminals will rename the encrypted files using the .Fargo3 extension (e.g., OriginalFileName.FileExtension.Fargo3), while the ransom note generated by the malware will appear using the file name “RECOVERY FILES.txt.” In the message, the victims will see threats of getting their system’s file permanently deleted if they use third-party software to resolve it on their own.
Additionally, cybercriminals say they would publish the data in the public domain if the victims refuse to pay the ransom.
IoCs
MD5:
d687eb9fea18e6836bd572b2d180b144
b4fde4fb829dd69940a0368f44fca285
c54daefe372efa4ee4b205502141d360
4d54af1bbf7357964db5d5be67523a7c
41bcad545aaf08d4617c7241fe36267c
Downloader: hxxp://49.235.255[.]219:8080/Pruloh_Matsifkq[.]png
SHA-1: 0e7f076d59ab24ab04200415cb35037c619d0bae
SHA-256: 863e4557e550dd89e5ca0e43c57a3fc1889145c76ec9787e97f76e959fc8e1e1
Vhash: 015056655d155510f8z73hz2075zabz
Imphash: c8318053dac1b12c686403fde752954c








Leave A Comment