
Organizations in the Spanish-speaking nations of Mexico and Spain are in the crosshairs of a new campaign designed to deliver the Grandoreiro banking trojan.
Grandoreiro Malware
- Keylogging
- Auto-Updation for newer versions and modules
- Web-Injects and restricting access to specific websites
- Command execution
- Manipulating windows
- Guiding the victim’s browser to a certain URL
- C2 Domain Generation via DGA (Domain Generation Algorithm)
- Imitating mouse and keyboard movements
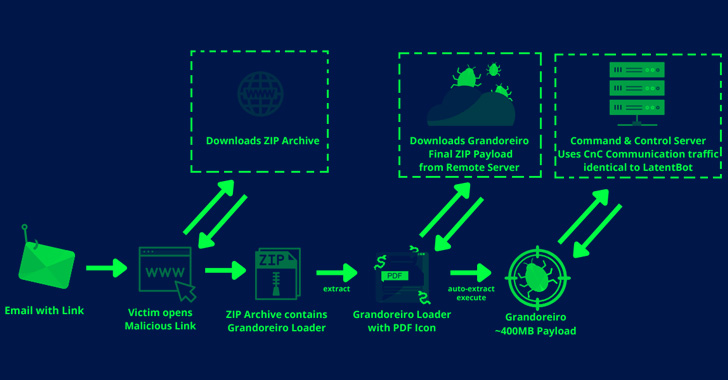
The campaign begins with a spear-phishing email written in Spanish, and the email consists of an embedded link that redirects the victim to a website that further downloads a malicious ZIP archive on the victim’s machine.
The ZIP archive contains the Grandoreiro Loader module with a PDF Icon in order to lure the victim into opening it. Once the file is opened, it downloads and executes the “Grandoreiro” payload (400MB) from a Remote HFS server which further communicates with the C2 server using traffic identical to LatentBot
Researchers observed two separate types of phishing emails used in this specific campaign.
In the first campaign,
they found that the first set of phishing emails observed were those in which the threat actors impersonated the government officials and instructed victims to download and share the Provisional Archiving Resolution.
In the second campaign,
“Once the link is opened it redirects to the malicious domain: http[:]//assesorattlas[.]me which then further downloads a ZIP File consisting of the Grandoreiro Loader,” researchers say.
In all the phishing emails, researchers observed that the ZIP file extracts two files with extensions .exe and .xml files. In this .xml file is not an XML file but a portable executable with the original name “Extensions.dll.” This file is signed with a valid “ASUSTEK COMPUTER INCORPORATION” certificate.
The findings suggest that Grandoreiro is continuously evolving into a sophisticated malware with new anti-analysis features that gives attackers full remote access capabilities and poses a significant threat to employees and their organizations.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




