
Zscaler researchers linked a recently discovered sample of a new malware called LilithBot to the Eternity group.
What is LilithBot Malware?
LilithBot, a multipurpose malware sample, was found by ThreatLabz. Further investigation indicated that malware was connected to the Eternity group (also known as EternityTeam or Eternity Project), a threat organization related to the Russian Jester Group.
Their services were spread via a Telegram and a Tor URL for these numerous payloads.
How the attack happens?
LilithBot is able to steal all the information (browser history, cookies, pictures, and screenshots) from infected systems, then uploads itself as a zip file to Command and Control.
Registration of the LilithBot is the first step in the process. The malicious software first verifies a Mutex called “8928a2d3-173b-43cb-8837-0e2e88b6d3b1” before looking for a file in the Startup folder.
The filename is given the .exe extension and entered in the Startup path, successfully registering the bot.
The Eternity Miner module goes for $90 as an annual subscription, customers can customize it with their own Monero pool and AntiVM features. The Eternity operators also sells the clipper malware for $110, it monitors the clipboard for cryptocurrency wallets and replaces them with the wallet address of the attackers,

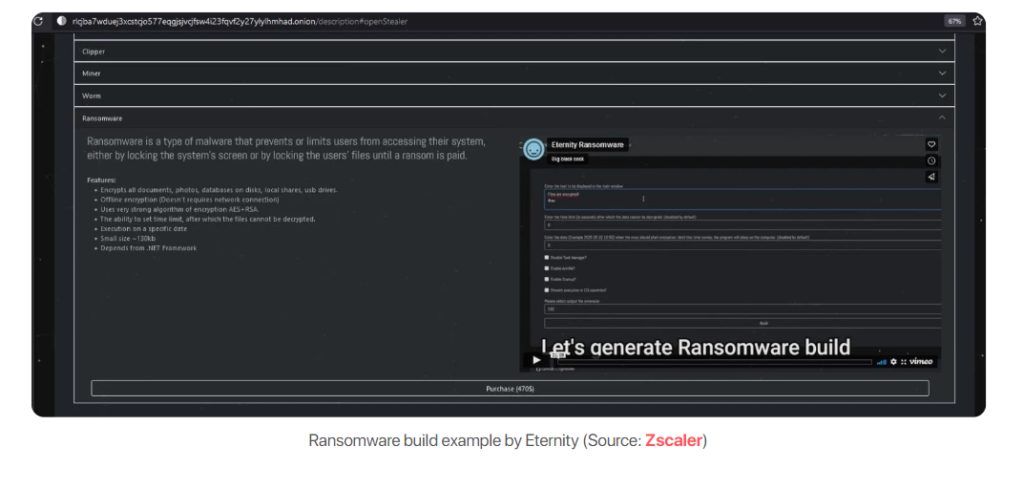
Ransomware is Eternity’s most expensive service; a video on how to create the ransomware payload is available on the Tor page.
However ,Eternity usually operates via Telegram and accepts payments through popular cryptocurrencies including BTC, ETH, XMR, USDT, LTC, DASH, ZEC and DOGE.
According to Cyble, the operators behind the Eternity Project are also developing a DDoS Bot malware borrowing code from the existing Github repository.
Finally ,the threat actors are continuously enhancing the malware by adding new features, including as anti-debugging capabilities and anti-VM checks.
LilithBot Malware IOCs
Executables:
- 0ebe8de305581c9eca37e53a46d033c8
- 1cae8559447370016ff20da8f717db53
- e793fcd5e44422313ec70599078adbdc
DLL:
- 65c0241109562662f4398cff77499b25
C2 Servers:
- 77.73.133.12
- 45.9.148.203
- 91.243.59.210
- 195.2.71.214
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




