Cybersecurity researchers have reiterated similarities involving the hottest iteration of the LockBit ransomware and BlackMatter, a rebranded variant of the DarkSide ransomware strain that closed store in November 2021.
The new variation of LockBit
Identified as LockBit 3. aka LockBit Black, was launched in June 2022, launching a manufacturer new leak web site and what is the incredibly very first ransomware bug bounty plan, together with Zcash as a cryptocurrency payment possibility.
Its encryption method involves appending the extension “HLJkNskOq” or “19MqZqZ0s” to every single and every file and shifting the icons of the locked information to that of the .
ico file that’s dropped by the LockBit sample to kick-begin the infection.
Similarities to BlackMatter ransomware
Researchers have pointed out that portions of LockBit 3.0’s code seem to be borrowed from the BlackMatter ransomware, hence the nickname LockBit Black.
LockBit’s comprehensive similarities to BlackMatter appear from overlaps in the privilege escalation and harvesting routines .
Also of note is its use of a “-pass” argument to decrypt its major plan, a conduct noticed in one more defunct ransomware family named Egregor, proficiently producing the binary more challenging to reverse if the parameter is not available.
In addition, LockBit 3.0 is designed to check the victim machine’s display language to avoid compromising systems associated with the Commonwealth of Independent States (CIS) states.
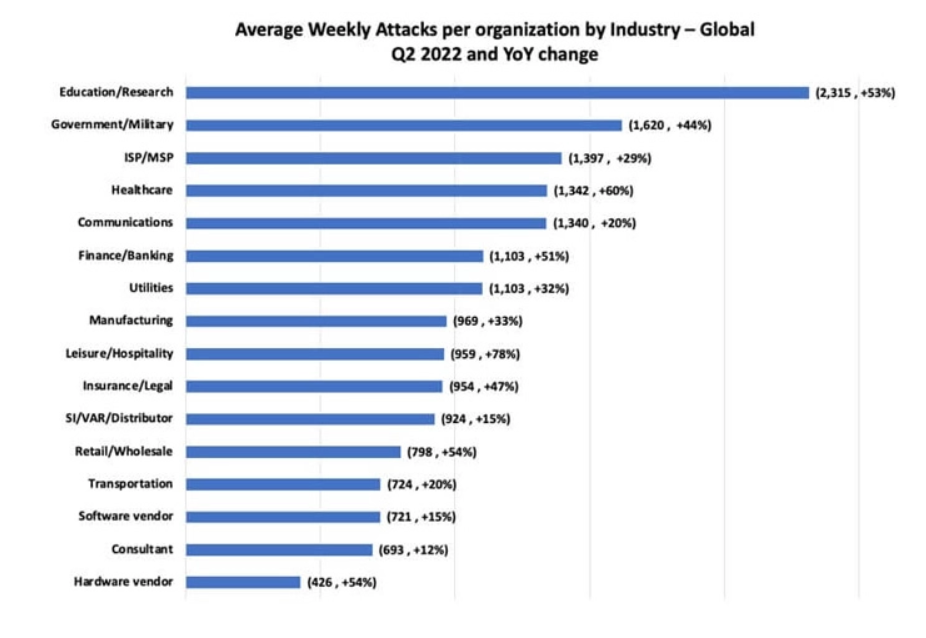
The improvement also highlights the ongoing results of the RaaS enterprise product, reducing the barrier to entry for extortionists and increasing the get to of ransomware.
Trendmicro says like BlackMatter, LockBit 3.0 also performs these routines:
- Attempts to log in using credentials from its configuration list to determine if the compromised system is a part of the domain admin that it will use for later routines
- Terminates and deletes processes and services from its configuration list, a routine similar to that of BlackMatter
- Wipes the recyle bin folder of every drive
- Checks a list of computer name hashes to avoid from its configuration list
- Connects to the C&C server from its configuration list if the flag is set
- Encrypts network shares and Exchange Mailbox if set in its configuration flag
- Obtains a list of files, folders, and extensions to be avoided from its configuration list
- Uses pointed files when encrypting .lnk files
- Prints the ransom note on any available printers and modifies the desktop wallpaper
- Uses the same encryption algorithm as BlackMatter
IOCS
| SHA-256 | Detection name |
| 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce | Ransom.Win32.LOCKBIT.YXCGD |
| a56b41a6023f828cccaaef470874571d169fdb8f683a75edd430fbd31a2c3f6e | Ransom.Win32.LOCKBIT.YXCGFT |
| d61af007f6c792b8fb6c677143b7d0e2533394e28c50737588e40da475c040ee | Ransom.Win32.LOCKBIT.YXCGD |
| 506f3b12853375a1fbbf85c82ddf13341cf941c5acd4a39a51d6addf145a7a51 | Ransom.Win32.LOCKBIT.YXCGKT |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!








Leave A Comment