
A never ever-in advance of-observed Linux malware has been dubbed a “Swiss Military Knife” for its modular architecture and its functionality to set up rootkits.
Lightning Framework
This previously undetected Linux threat, called Lightning Framework by Intezer, is equipped with a plethora of features.
“The framework has both passive and active capabilities for communication with the threat actor, including opening up SSH on an infected machine, and a polymorphic malleable command and control configuration,” Intezer researcher Ryan Robinson said in a new report published today.
Central to the malware is a downloader (“kbioset”) and a core (“kkdmflush”) module, the former of which is engineered to retrieve at least seven different plugins from a remote server that are subsequently invoked by the core component.
Lightning Framework is built using a simple structure: a downloader component that will download and install the malware’s other modules and plugins, including its core module, on compromised Linux devices.
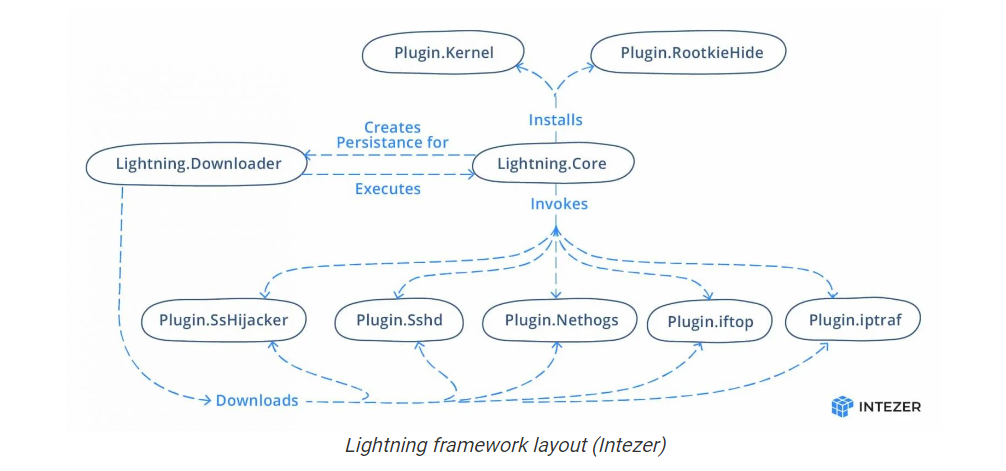
It further sets up persistence by creating an initialization script that’s executed upon system boot, effectively allowing the downloader to be automatically launched.
“Malware targeting Linux environments surged in 2021, with a large amount of innovation resulting in new malicious code, especially in ransomwares, trojans, and botnets,” Robinson said.
IOCS for Linux malware
| File | SHA256 |
| Lightning.Downloader | 48f9471c20316b295704e6f8feb2196dd619799edec5835734fc24051f45c5b7 |
| Lightning.Core | fd285c2fb4d42dde23590118dba016bf5b846625da3abdbe48773530a07bcd1e |
| Linux.Plugin.Lightning.Sshd | ad16989a3ebf0b416681f8db31af098e02eabd25452f8d781383547ead395237 |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




