
Microsoft has released security guidance to address a critical vulnerability called React2Shell (CVE-2025-55182). The issue affects applications built with React Server Components and Next.js and can result in full server compromise.
The vulnerability carries a CVSS score of 10.0 and allows attackers to execute code on a server without authentication. In many cases, a single crafted web request is enough to trigger the attack.
Microsoft observed active exploitation beginning on December 5, 2025. Both Windows and Linux systems were targeted, and the attacks showed a high success rate, indicating that many exposed applications are vulnerable.
How the issue occurs
React Server Components use the Flight protocol to exchange data between the client and server. Due to insufficient input validation, the server may trust malicious data sent by an attacker. This allows internal objects to be manipulated, leading to prototype pollution and, ultimately, remote code execution.
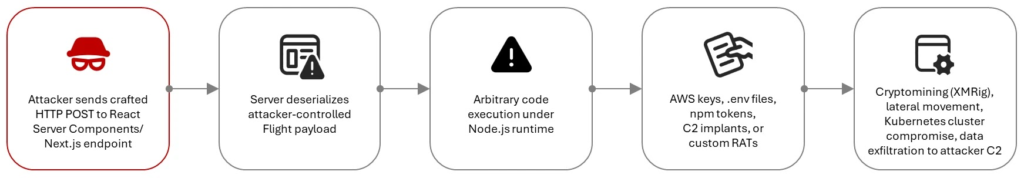
According to Microsoft’s analysis, attackers typically send a specially crafted POST request to a vulnerable application. When the backend processes this request, the malicious logic runs inside the Node.js environment, bypassing normal security checks. Because this behavior is enabled by default, many applications are exposed without any special configuration.
Once attackers gain access, they often establish persistence by deploying reverse shells. These connect back to attacker-controlled infrastructure, commonly using Cobalt Strike, allowing continued access and further activity within the environment.
The attack flow shows how intrusions progress from initial access to achieving the attacker’s goals.
Attackers often use remote management tools like MeshAgent or modify files such as authorized_keys to keep access even after a reboot.
To stay hidden, they may use bind mounts to mask malicious processes from monitoring tools.
The payloads seen include remote access trojans like VShell and EtherRAT, along with XMRig cryptom.
This example of reverse shell observed in one of the campaigns highlights the command structures used during these intrusions.
Beyond immediate control, attackers actively enumerate system details and environment variables to steal cloud identity tokens for Azure, AWS, and Google Cloud Platform.
This credential theft facilitates lateral movement across cloud resources, significantly amplifying the breach’s impact on organizations that rely on these integrated services.




