
Windows privilege escalation remains a common technique used by attackers to gain deeper control of a system.
By abusing weakly protected components such as kernel drivers and named pipes, a standard user account can be elevated to SYSTEM-level access. Kernel drivers are especially attractive targets when IOCTL handling lacks proper input validation.
Windows Kernel and Named Pipe Flaws
In some WDM drivers that use METHOD_BUFFERED mode, the I/O Manager creates a kernel buffer but does not properly check the data coming from user space. This missing validation becomes a serious security weakness.
Attackers can abuse this gap by sending specially crafted IOCTL requests. These requests include dangerous pointer and size values that the kernel mistakenly trusts and processes.
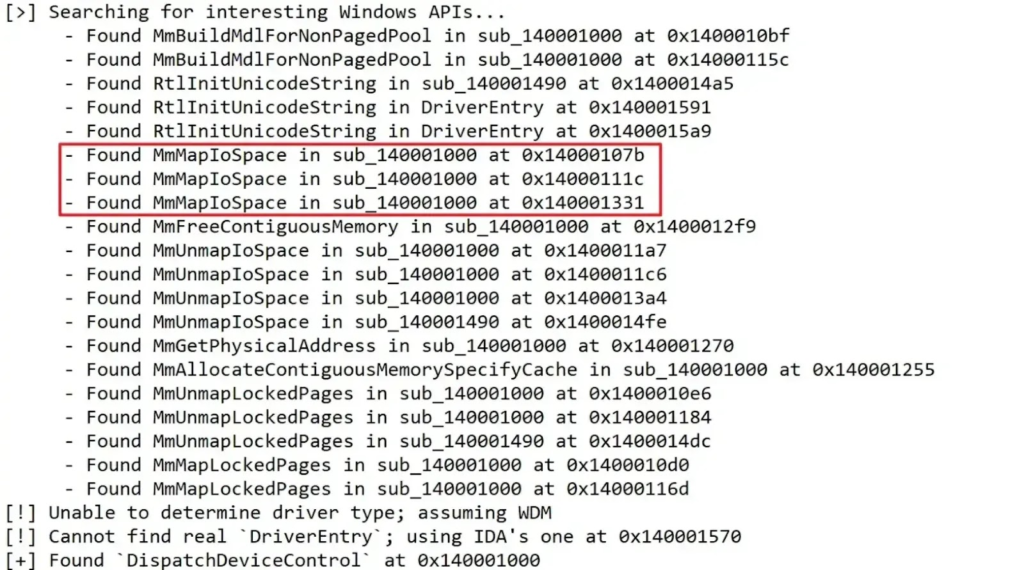
A typical attack starts by finding exposed device names, then reviewing IOCTL handling logic, and finally identifying weak input checks. Once found, attackers can force the driver to call unsafe kernel functions such as MmMapIoSpace.
This gives them arbitrary read and write access in kernel memory, which can be used to steal the SYSTEM process token and assign it to their own process, resulting in full privilege escalation.
Named pipes are widely used for communication between processes, especially by services running as SYSTEM. This makes them an attractive target for attackers.
While named pipes do not access memory directly like kernel drivers, many services trust incoming pipe messages without proper checks, creating another path for privilege escalation.
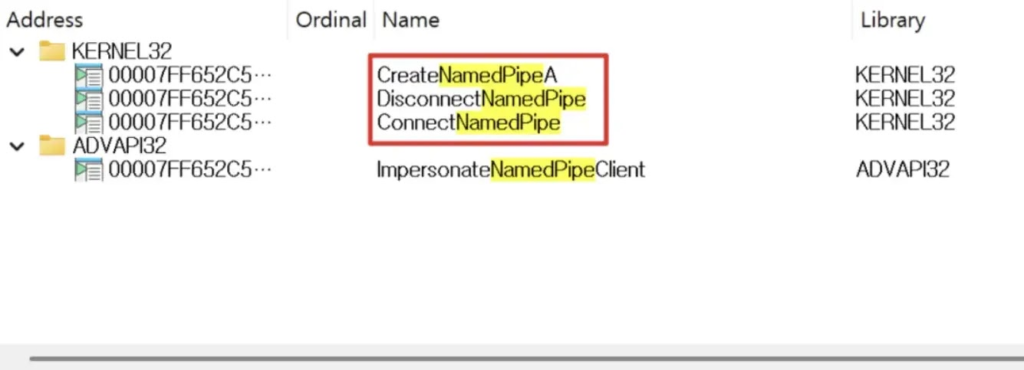
The attack begins by looking for SYSTEM-owned named pipes that have weak permissions, allowing any user to read from or write to them. Attackers then study how the pipe works by analyzing the service’s code.
In some cases, services accept pipe requests without properly checking who sent them. This lets a normal user ask the service to perform privileged actions.
Researchers have seen examples where this flaw allowed changes to sensitive HKLM registry keys. One real-world case involved a commercial antivirus product, where an insecure named pipe was abused to modify the registry without authorization.
This weakness can let attackers abuse Image File Execution Options (IFEO) to run their own code as SYSTEM.
To reduce risk, security teams should closely review third-party kernel drivers, limit IOCTL access, and ensure all user input is properly checked before it reaches the kernel. Named pipes also need strict permission checks and clear validation of every request.
Research published by Hackyboiz shows that many environments expose named pipes with overly broad permissions. Organizations should identify these pipes and disable or lock down the risky ones. As Windows systems continue to be targeted by advanced attackers, understanding these local privilege-escalation paths is critical for protecting enterprise environments.




