
Netlab recently released a report confirming that this sample was adapted from the leaked Hive project server source code from the U.S. CIA.
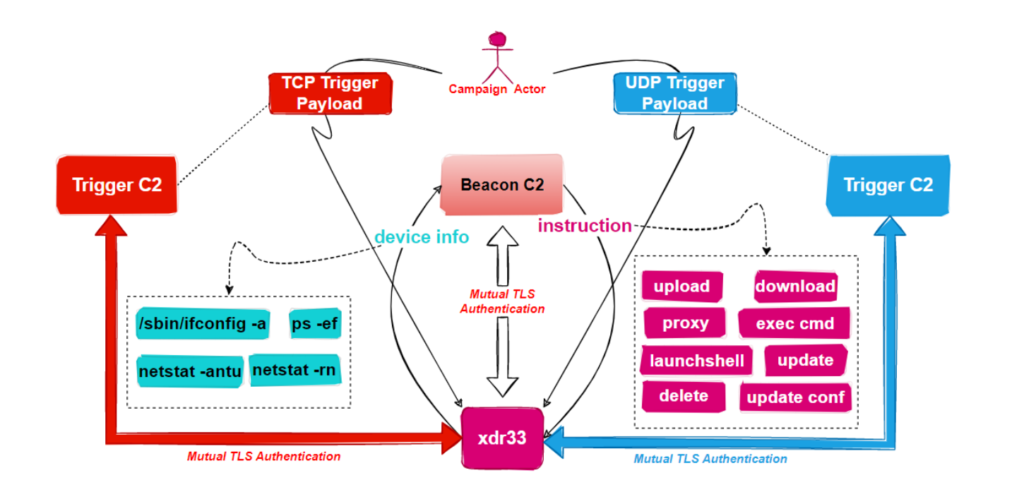
This new variant of the HIVE kit, named Xdr33, mainly functions as a backdoor. It collects sensitive information and provides a foothold for subsequent intrusions.
Trigger’s primary function is to monitor the NIC traffic to identify specific messages that conceal its C2. Subsequently, it establishes communication with the C2 in the Trigger payload and waits for the execution of the commands issued by it.
“In terms of function, there are two main tasks: beacon and trigger, of which beacon is periodically report sensitive information about the device to the hard-coded Beacon C2 and execute the commands issued by it, while the trigger is to monitor the NIC traffic to identify specific messages that conceal the Trigger C2, and when such messages are received, it establishes communication with the Trigger C2 and waits for the execution of the commands issued by it,” the researchers explained.
Expertise-sharing forum GitHub describes the original Hive spyware as providing “a covert communications platform for a whole range of CIA malware” that enables stolen data to be sent to agency servers and instructions to be relayed to field operatives.
The intent of the backdoor, per the Chinese cybersecurity firm, is to harvest sensitive information and act as a launchpad for subsequent intrusions. It improves upon Hive by adding new C2 instructions and functionalities, among other implementation changes.
IOC
af5d2dfcafbb23666129600f982ecb87
ee07a74d12c0bb3594965b51d0e45b6f
45.9.150.144:443
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




