Researchers are seeing a “significant increase” in attacks deploying the Qakbot malware, which have targeted victims in Germany, Argentina, Italy, Algeria, Spain, the U.S. and other countries with emails containing PDF attachments that deliver the banking trojan.
What is QBOT ?
Qakbot, which was first detected in 2007, has since grown into a multi-purpose malware with multiple functionalities, including tools for performing reconnaissance, exfiltrating data and delivering other payloads. Its modular nature gives it flexibility for keeping up with the evolving threat landscape, and the malware has recently seen growing popularity among a variety of threat groups that either use its various capabilities or any of its second-stage payloads.
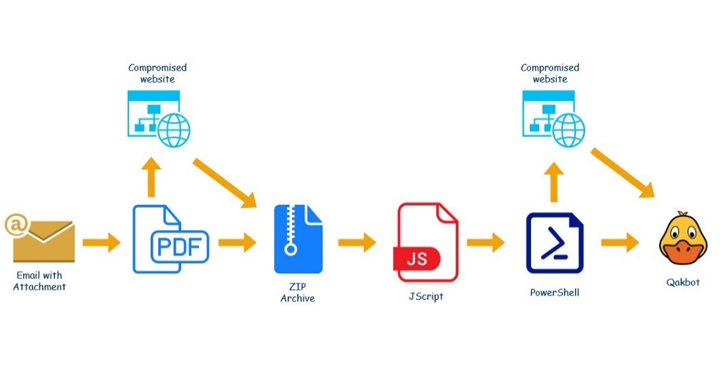
Attackers deploying the malware have previously relied on hijacked email threads (harvested in bulk from Microsoft ProxyLogon).Researchers said at least 4,500 spam emails have been sent in this wave of attacks, which they first observed April 4.
“The malware would be delivered through e-mail letters written in different languages — variations of them were coming in English, German, Italian, and French,” said Victoria Vlasova, Andrey Kovtun and Darya Ivanova, researchers with Kaspersky in a monday report.
“After the WSF file is deobfuscated, its true payload gets revealed: a PowerShell script encoded into a Base64 line,” Kaspersky wrote. “As soon as the user opens the WSF file from the archive, the PowerShell script will be discreetly run on the computer and use wget to download a DLL file from a remote server.”
Kaspersky has also observed some Qbot versions turning victims’ computers into proxy servers to facilitate traffic redirection.
Qbot indicators of compromise
MD5
PDF files
253E43124F66F4FAF23F9671BBBA3D98
39FD8E69EB4CA6DA43B3BE015C2D8B7D
ZIP archives
299FC65A2EECF5B9EF06F167575CC9E2
A6120562EB673552A61F7EEB577C05F8
WSF files
1FBFE5C1CD26C536FC87C46B46DB754D
FD57B3C5D73A4ECD03DF67BA2E48F661
DLL
28C25753F1ECD5C47D316394C7FCEDE2
Malicious links
ZIP archive
cica.com[.]co/stai/stai.php
abhishekmeena[.]in/ducs/ducs.php
DLL
rosewoodlaminates[.]com/hea/yWY9SJ4VOH
agtendelperu[.]com/FPu0Fa/EpN5Xvh
capitalperurrhh[.]com/vQ1iQg/u6oL8xlJ
centerkick[.]com/IC5EQ8/2v6u6vKQwk8
chimpcity[.]com/h7e/p5FuepRZjx
graficalevi.com[.]br/0p6P/R94icuyQ
kmphi[.]com/FWovmB/8oZ0BOV5HqEX
propertynear.co[.]uk/QyYWyp/XRgRWEdFv
theshirtsummit[.]com/MwBGSm/lGP5mGh
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!








Leave A Comment