A new wave of phishing emails is circulating globally, posing as offers for a “Social Media Manager” role at Red Bull.
These emails, crafted to look like personalized job invitations, are sent from messaging-service@post.xero.com and successfully pass SPF, DKIM, and DMARC checks—allowing them to bypass traditional email security filters undetected.
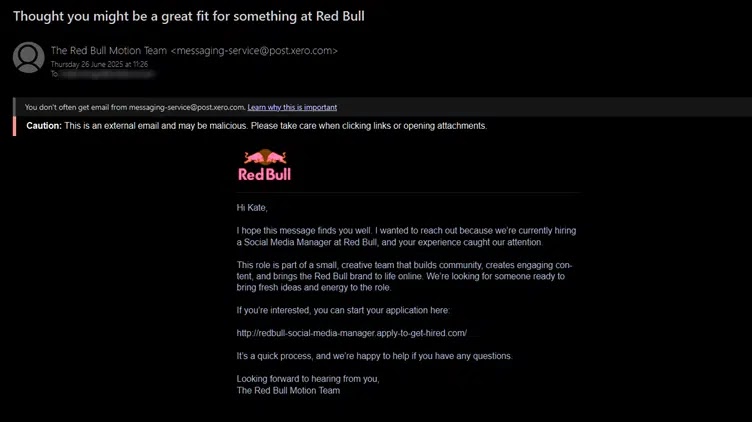
The scam exploits the surge in remote work interest fueled by the pandemic, along with Red Bull’s strong brand recognition, to entice unsuspecting recipients.
Recipients who click the embedded link are first directed through a reCAPTCHA verification, then taken to a convincing, Glassdoor-style job listing page.
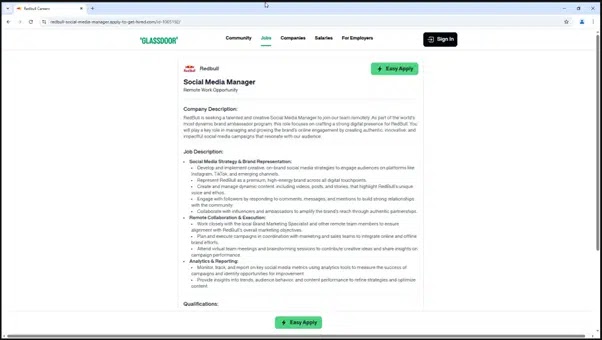
Evalian analysts revealed that although the phishing site appears legitimate, the domain – redbull-social-media-manager.apply-to-get-hired.com – is only a few weeks old and resolves to a VPS hosted in AS-63023, a network known for harboring short-lived malicious infrastructure.
After presenting a fake job listing, the site redirects victims to a counterfeit Facebook login page, where any entered credentials are exfiltrated via a POST request to /login_job on 38.114.120.167. These credentials never reach Facebook; instead, they vanish into a backend that often returns a 504 Gateway Timeout – a deliberate stalling tactic that thwarts sandbox analysis and conceals successful data theft.
Evalian researchers also uncovered the same TLS JARM fingerprint across related domains impersonating brands like MrBeast and Meta, indicating that the phishing setup is part of a rentable kit rather than a one-off operation.
Where this campaign stands out is in its detection evasion techniques. The attackers leverage Mailgun’s high-reputation IP addresses, allowing them to inherit the trust of legitimate services like Xero, while masking the true reply-to address:
red.bull.crew@srbs.user0212-stripe.com.
They also automate the issuance of Let’s Encrypt certificates, ensuring each domain presents a valid SSL certificate and avoiding typical self-signed warnings. Even the reCAPTCHA isn’t user-focused – it’s strategically placed to delay automated URL scanners, buying the phishing infrastructure just enough time to operate undetected.
where mail.sender_domain==”post.xero.com”
and mail.reply_to matches “.*user0212-stripe.com”
and url.domain endswith(“apply-to-get-hired.com”)
and
network.jarm==”27d40d40d00040d00042d43d000000d2e61cae37a985f75ecafb81b33ca523″
The Kusto-style query referenced above—based on Evalian’s SOC detection rules—correlates sender reputation, suspicious reply-to domains, malicious infrastructure, and the shared JARM fingerprint to generate high-confidence alerts without overwhelming analysts with false positives.
Although job seekers are the primary targets, organizations are advised to block the identified IOCs, monitor outbound connections to 38.114.120.167, and educate users that even emails which pass all authentication checks (SPF, DKIM, and DMARC) can still be cleverly disguised threats.












Leave A Comment