“A New DCHSpy Variant Unveiled: Iranian Cyber Group MuddyWater Targets Mobile Data Amid Rising Israel-Iran Tensions”
This advanced version of the DCHSpy Android surveillance tool, deployed just a week after the escalation in the Israel-Iran conflict, marks a major leap in mobile surveillance technology. It focuses on stealing sensitive communications data, taking advantage of the current geopolitical unrest to trick victims into falling prey to the attack.
The DCHSpy Malware: A Tool of MuddyWater’s Global Cyber Espionage Campaign
The DCHSpy malware family has been linked to MuddyWater, an Advanced Persistent Threat (APT) group with suspected ties to Iran’s Ministry of Intelligence and Security (MOIS). This cyber espionage group has a long history of targeting a wide array of government and private organizations, including those in telecommunications, defense, oil, and local government sectors, across the Middle East, Asia, Africa, Europe, and North America.
The timing of the latest DCHSpy samples is particularly noteworthy, appearing around a week after Israel’s first strikes on Iranian nuclear facilities.
The malware showcases ongoing development and increased sophistication, reflecting continued investment by state-sponsored actors in mobile surveillance technologies.
Technical analysis has revealed that DCHSpy shares infrastructure with another Android malware, SandStrike, which was previously used to target Baháʼí practitioners. Researchers also found that hardcoded command and control (C2) IP addresses were reused across different malware families, establishing clear connections between various campaigns.
DCHSpy: A Sophisticated Modular Surveillanceware with Advanced Exfiltration Capabilities
DCHSpy operates as a highly modular surveillanceware platform with extensive data collection features. The malware systematically harvests sensitive data from infected devices, including:
- User accounts logged into various apps
- Contacts, SMS messages, and local files
- Precise location data and complete call logs
- Audio recordings by taking control of device microphones
- Photos through manipulation of device cameras
The latest variants have notably enhanced capabilities for extracting WhatsApp data, marking a significant advancement over previous versions.
Once the data is collected, it is compressed and encrypted using passwords received from Command and Control (C2) servers. The encrypted payload is then securely transmitted to Secure File Transfer Protocol (SFTP) servers, ensuring stealthy and effective exfiltration while evading detection.
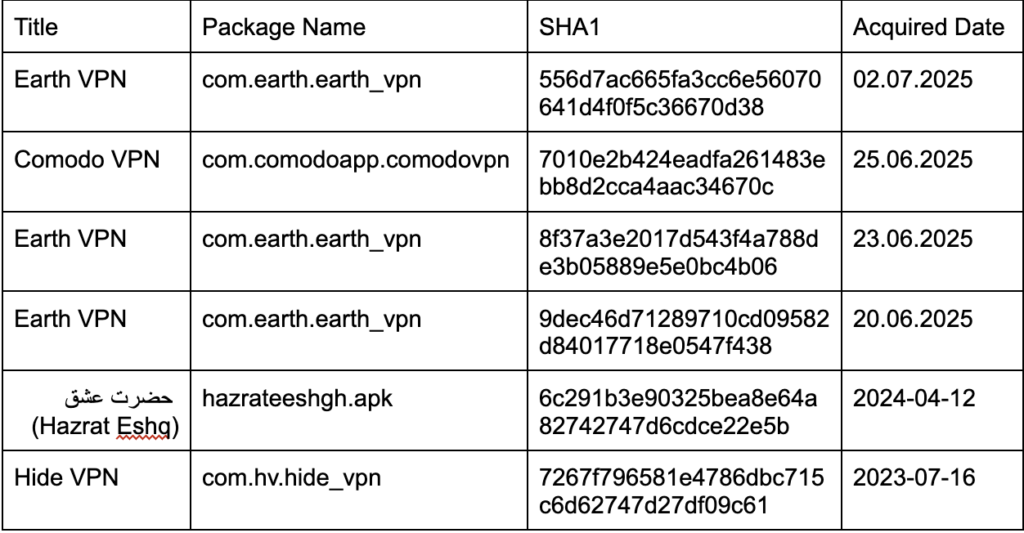
Analyzed samples, such as one with the SHA1 hash 9dec46d71289710cd09582d84017718e0547f438, were found to be distributed under seemingly legitimate names, such as starlink_vpn(1.3.0)-3012 (1).apk, which highlights the sophisticated naming conventions used to mask its true intent.
MuddyWater, the APT group behind DCHSpy, employs social engineering tactics, capitalizing on timely political events and critical services to lure victims. The group typically distributes these malicious applications via Telegram channels, masquerading as legitimate VPN services like EarthVPN and ComodoVPN.
The distribution pages for DCHSpy are carefully crafted to appeal to both English and Farsi-speaking audiences who hold views opposing the Iranian regime. These pages use targeted language and themes designed to attract individuals in politically sensitive environments.
The integration of StarLink-themed lures is particularly significant, appearing to coincide with reports of StarLink providing internet services to Iranian citizens during government-imposed internet outages following the escalation of hostilities between Israel and Iran. This strategic timing showcases how threat actors take advantage of humanitarian crises and the need for internet connectivity to distribute malicious surveillance tools.
By exploiting these circumstances, DCHSpy targets activists and journalists operating in highly restrictive environments, using their vulnerability to deliver tools designed to monitor and suppress their activities. This highlights the increasing sophistication of cyber espionage tactics that manipulate geopolitical and social crises to achieve surveillance objectives.













Leave A Comment