On November 7, Veracode researchers found a dangerous typosquatting attack targeting developers who use GitHub Actions.
A fake npm package called “@acitons/artifact” had already reached 206,000 downloads before it was removed. This package looked almost identical to the real “@actions/artifact” package. The attacker simply swapped two letters — “ti” became “it” — hoping developers would mistype the name and install the wrong package.
How the Attack Worked
Veracode discovered six versions of the malicious package. Each one had a post-install script that ran automatically after installation.
This script downloaded hidden malware that antivirus tools could not detect at the time — it showed zero detections on VirusTotal.
The malware used an obfuscated shell script compiled with the Shell Script Compiler (shc). When executed, it restarted itself, changed environment variables, and then ran a hidden Node.js package containing an obfuscated file called “verify.js.”
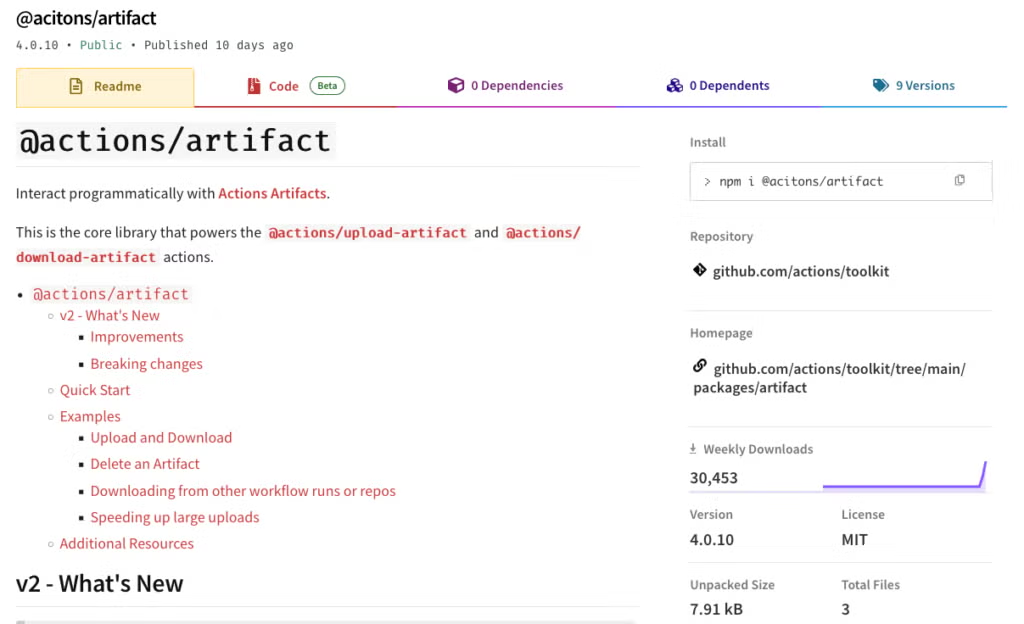
The script was designed to check for GitHub-specific environment variables, meaning the attack was aimed directly at GitHub Actions workflows.
The malware was built to target only specific GitHub repositories. It quietly exited unless the repository owner matched the attacker’s chosen targets — including GitHub itself.
More importantly, the malware attempted to steal authentication tokens from the build environment. With these tokens, attackers could publish fake artifacts that looked like they came from GitHub, putting developers and downstream users at serious risk of a wider supply chain attack.
The attackers showed a high level of planning. Each malicious file had a built-in expiry date, causing it to stop working after a certain time. One sample expired on November 6 (UTC), and another expired the following day.
This indicates the campaign was designed to run only for a short period to avoid detection. GitHub later identified the malicious activity, and the involved GitHub accounts have since been removed.
The stolen data was sent out through encrypted channels. The malware first downloaded an AES encryption key from a remote command-and-control server and then used it to send encrypted information to a GitHub App–based endpoint. This made it even harder to trace the attacker’s real infrastructure.
Veracode quickly reported the malicious package to npm, which led to its removal. Customers using Veracode Package Firewall were protected immediately once the threat was analyzed.
Researchers also found and blocked 12 additional versions of another malicious package called “8jfiesaf83”, released earlier in November by the same attacker.
This incident highlights the increasing danger of supply chain attacks, now listed as the third most serious security risk in the OWASP Top 10 for 2025.
It also shows that typosquatting is still a highly effective method for compromising CI/CD pipelines and stealing sensitive authentication tokens.
Organizations using GitHub Actions should carefully review their dependencies and add extra security checks before installing any packages.
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!












Leave A Comment