More than 900,000 Chrome users were impacted by two harmful browser extensions that quietly collected AI chat content and browsing activity.
The extensions captured conversations from tools like ChatGPT and DeepSeek, along with users’ complete browsing histories, and sent the data to external servers controlled by attackers.
The issue was uncovered by researchers at OX Security, who found that the extensions were designed to closely resemble the popular AITOPIA AI sidebar. One of the fake extensions even gained extra visibility by appearing as a recommended option in the Chrome Web Store.
Both tools offered AI chat features powered by models such as GPT and Claude, making them appear legitimate to users. To avoid suspicion, they asked for permission under the label of “anonymous analytics,” while secretly harvesting data.
Further investigation showed that the attackers used third-party hosting services to publish privacy policies and linked the two extensions together so that removing one would lead users to the other.
How the Malware Works
Once installed, the malicious extensions quietly watch what users do in their browser. They track open tabs and assign a unique ID to each victim.
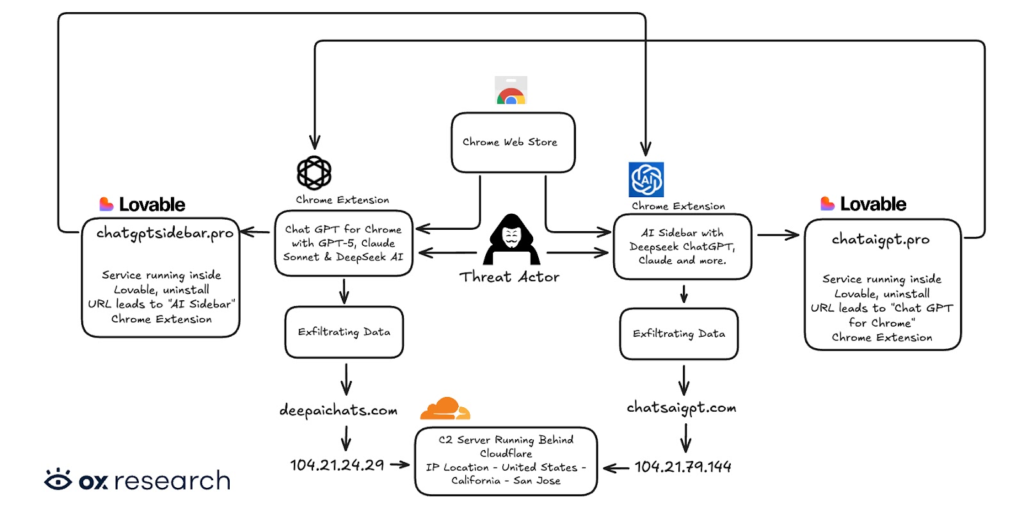
When a user opens ChatGPT or DeepSeek, the extensions jump into action. They read the page content and copy chat messages, questions, replies, and session details directly from the browser window. This information is temporarily saved on the device.
Every 30 minutes, the collected data is packaged, encoded, and sent to attacker-controlled servers. This allows the attackers to harvest sensitive content that users may never expect to leave their browser.
The stolen data can include:
- Proprietary code and internal discussions
- Business plans and strategy conversations
- Personal information and search activity
- Internal links and system references
Beyond chat data, the extensions also record browsing activity. This gives attackers insight into user behavior, company structures, and online habits—information that can later be used for targeted phishing, fraud, or identity theft.
As of early January 2026, both extensions were still available for download. Although one lost its featured status after being reported, it continued to receive updates, helping it appear legitimate.
Users are strongly advised to review installed extensions, remove any unknown or suspicious ones, and avoid relying on store badges alone. Only install extensions from trusted developers and limit permissions whenever possible.
IoCs
| Type | Value | Notes |
|---|---|---|
| Extension name | Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI | Malicious AI sidebar-style extension |
| Extension ID | fnmihdojmnkclgjpcoonokmkhjpjechg | Chrome Web Store ID |
| Version | 1.9.6 | Reported malicious build |
| SHA-256 hash | 98d1f151872c27d0abae3887f7d6cb6e4ce29e99ad827cb077e1232bc4a69c00 | Package hash |
| Extension name | AI Sidebar with Deepseek, ChatGPT, Claude and more | Second malicious extension |
| Extension ID | inhcgfpbfdjbjogdfjbclgolkmhnooop | Chrome Web Store ID |
| Version | 1.6.1 | Reported malicious build |
| SHA-256 hash | 20ba72e91d7685926c8c1c5b4646616fa9d769e32c1bc4e9f15dddaf3429cea7 | Package hash |
Network and C2 IoCs
| Category | Domain / Endpoint | Notes |
|---|---|---|
| C2 endpoint | deepaichats[.]com | Receives stolen chat data and URLs |
| C2 endpoint | chatsaigpt[.]com | Additional C2 for exfiltrated data |
| Lovable-hosted server | chataigpt[.]pro | Used for privacy policy / infra hosting |
| Lovable-hosted server | chatgptsidebar[.]pro | Used for uninstall redirect and infra |
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!













Leave A Comment