A newly observed Linux threat called ShadowHS is showing how modern attackers are moving beyond traditional malware. Instead of dropping files on a system, this framework runs completely in memory, making it much harder for standard security tools to detect.
ShadowHS is built from a modified version of a legitimate utility and turned into a full post-exploitation toolkit. It avoids writing anything to disk, hides its process identity, and executes through memory-based techniques that bypass many antivirus and file-monitoring defenses. The infection chain uses encrypted loaders and carefully rebuilds the payload directly in memory before running it.
The final program is launched directly from memory and often imitates trusted processes, such as Python-related services, to reduce suspicion.
Human-Controlled and Stealth Focused
ShadowHS stands out because it does not behave like typical automated malware. Instead of launching noisy actions right away, it stays quiet at first. The framework focuses on studying the system, identifying security defenses, and ensuring the environment is safe for continued access. This careful, low-profile behavior suggests direct human control rather than a fully automated attack.
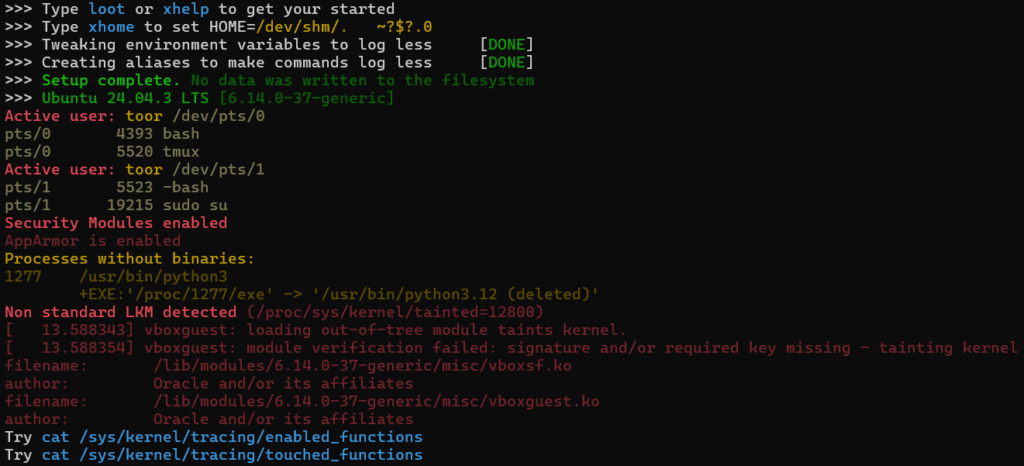
The tool gathers detailed information about installed security products by checking system paths, running services, and protection components. The findings help operators understand what defenses are active before deciding on the next step.
It also includes logic to remove other malicious programs that may already be present. By scanning for known malware, cryptominers, hidden kernel components, and suspicious in-memory programs, it tries to take exclusive control of the system.
Beyond that, the framework examines the system’s overall defense posture, reviewing kernel protections, loaded modules, and process activity to detect monitoring or security instrumentation.
For data theft, ShadowHS uses less common communication methods instead of standard tools like SSH or file transfer utilities. It creates hidden channels using user-space tunneling techniques, allowing files to be moved without triggering typical network monitoring alerts. Because of how these tunnels work, the traffic can appear local while actually being redirected externally, helping the activity remain unnoticed.
Security Measures
When fully activated, ShadowHS can start hidden crypto mining, scan networks to move sideways, and try to collect credentials from systems, cloud services, and virtual platforms.
Since it runs in memory and avoids writing files, regular antivirus tools may not detect it. Protection depends more on watching system behavior than scanning files.
To lower the risk:
- Monitor unusual process and memory activity
- Track suspicious command-line behavior
- Use deeper system and kernel-level monitoring
- Limit what applications can do at runtime
- Watch for strange or hidden network connections
This threat shows that modern Linux attacks are becoming quieter and more controlled, making behavior-based detection more important than ever.
Indicators of Compromise (IOCs)
| Indicator | Indicator Type | Description |
|---|---|---|
| 91.92.242[.]200 | IPv4 | Primary payload staging infrastructure |
| 62.171.153[.]47 | IPv4 | Operator-controlled relay for exfiltration and post-compromise operations |
| 20c1819c2fb886375d9504b0e7e5debb87ec9d1a53073b1f3f36dd6a6ac3f427 | SHA-256 | Main obfuscated shell loader script |
| 9f2cfc65b480695aa2fd847db901e6b1135b5ed982d9942c61b629243d6830dd | SHA-256 | Custom weaponized hackshell payload |
| 148f199591b9a696197ec72f8edb0cf4f90c5dcad0805cfab4a660f65bf27ef3 | SHA-256 | RustScan port scanner |
| 574a17028b28fdf860e23754d16ede622e4e27bac11d33dbf5c39db501dfccdc | SHA-256 | spirit-x86_64.tgz archive |
| 3f014aa3e339d33760934f180915045daf922ca8ae07531c8e716608e683d92d | SHA-256 | spirit/-bash (UPX-packed binary) |
| 847846a0f0c76cf5699342a066378774f1101d2fb74850e3731dc9b74e12a69d | SHA-256 | spirit/-bash (unpacked Golang binary) |
| 5a6b08d42cc8296b32034b132bab18d201a48c1628df3200e869722506dd4ec6 | SHA-256 | gpu1/screen miner wrapper |
| e11bcba19ac628ae1d0b56e43646ae1b5da2ccc1da5162e6719d4b7d68d37096 | SHA-256 | gpu1/lol miner component |
| 0bb7d4d8a9c8f6b3622d07ae9892aa34dc2d0171209e2829d7d39d5024fd79ef | SHA-256 | xmr/xmrigremove.sh |
| 9fdaf64180b7d02b399d2a92f1cdd062af2e6584852ea597c50194b62cca3c0b | SHA-256 | gpustak/-bash binary |
| b3ee445675fce1fccf365a7b681b316124b1a5f0a7e87042136e91776b187f39 | SHA-256 | gpustak/libxmrstak_cuda_backend.so CUDA backend |
| 5a6b08d42cc8296b32034b132bab18d201a48c1628df3200e869722506dd4ec6 | SHA-256 | gpustak/screen miner wrapper |
| 5a6b08d42cc8296b32034b132bab18d201a48c1628df3200e869722506dd4ec6 | SHA-256 | gpuecho/screen miner wrapper |
| 3ba88f92a87c0bb01b13754190c36d8af7cd047f738ebb3d6f975960fe7614d6 | SHA-256 | gpuecho/lol miner component |
| 5a6b08d42cc8296b32034b132bab18d201a48c1628df3200e869722506dd4ec6 | SHA-256 | gpu/screen miner wrapper |
| e11bcba19ac628ae1d0b56e43646ae1b5da2ccc1da5162e6719d4b7d68d37096 | SHA-256 | gpu/lol miner component |
| 4069eaadc94efb5be43b768c47d526e4c080b7d35b4c9e7eeb63b8dcf0038d7d | SHA-256 | ex/dirtycredz.x86_64 credential exploitation tool |
| 72023e9829b0de93cf9f057858cac1bcd4a0499b018fb81406e08cd3053ae55b | SHA-256 | ex/payload.so shared object payload |
| 662d4e58e95b7b27eb961f3d81d299af961892c74bc7a1f2bb7a8f2442030d0e | SHA-256 | ex/overlay helper component |
| e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | SHA-256 | ex/GCONV_PATH=./lol empty placeholder file |
| c679b408275f9624602702f5601954f3b51efbb1acc505950ee88175854e783f | SHA-256 | ex/payload.c payload source code |
| 666122c39b2fd4499678105420e21b938f0f62defdbc85275e14156ae69539d6 | SHA-256 | ex/blast exploitation utility |
| 8007b94d367b7dbacaac4c1da0305b489f0f3f7a38770dcdb68d5824fe33d041 | SHA-256 | ex/dp Dirty Pipe exploit |
| 072e08b38a18a00d75b139a5bbb18ac4aa891f4fd013b55bfd3d6747e1ba0a27 | SHA-256 | ex/ubu privilege escalation helper |
| 6c50fcf14af7f984a152016498bf4096dd1f71e9d35000301b8319bd50f7f6d0 | SHA-256 | ex/cve-2025-21756 exploit binary |
| 04a072481ebda2aa8f9e0dac371847f210199a503bf31950d796901d5dbe9d58 | SHA-256 | ex/traitor-x86_64 privilege escalation tool |
| 19df5436972b330910f7cb9856ef5fb17320f50b6ced68a76faecddcafa7dcd7 | SHA-256 | ex/autoroot.sh automated root escalation script |
| 7fbab71fcc454401f6c3db91ed0afb0027266d5681c23900894f1002ceca389a | SHA-256 | ex/dirtypipe.x86_64 Dirty Pipe exploit variant |
| e5a6deec56095d0ae702655ea2899c752f4a0735f9077605d933a04d45cd7e24 | SHA-256 | ex/dirtypagetable.x86_64 kernel exploitation tool |
| 7361c6861fdb08cab819b13bf2327bc82eebdd70651c7de1aed18515c1700d97 | SHA-256 | ex/lol/gconv-modules GCONV-based exploitation component |
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!













Leave A Comment