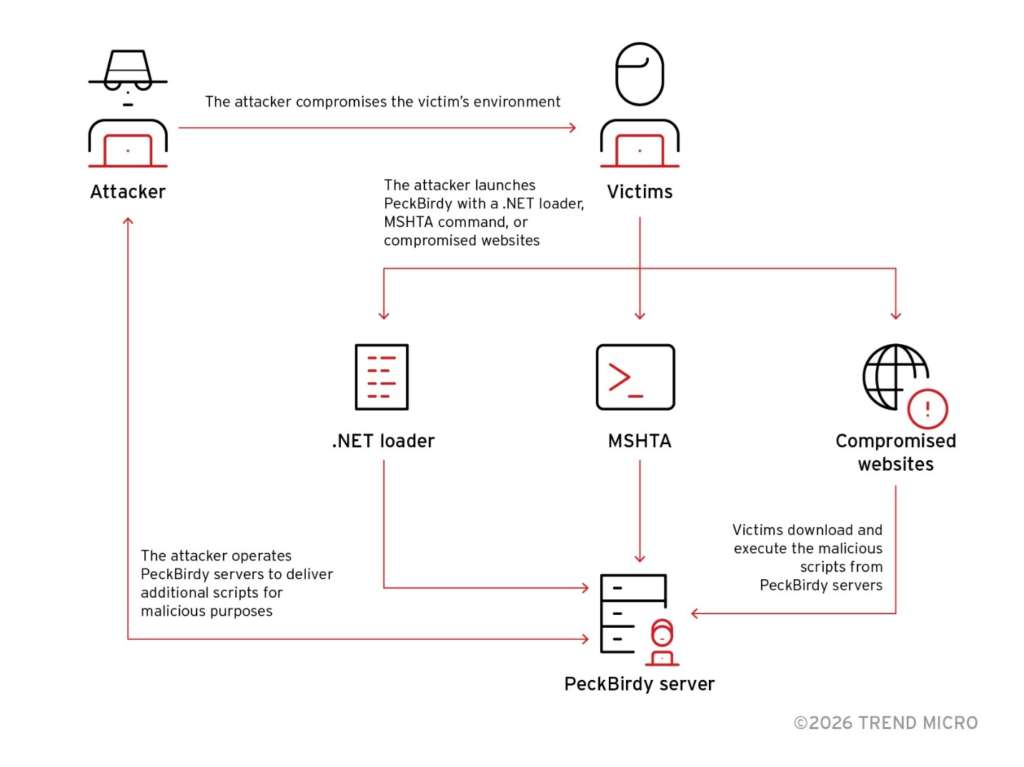
A malware framework called PeckBirdy has been active since 2023, using built-in system tools (LOLBins) to quietly deliver backdoors. Instead of dropping obvious malicious files, attackers use trusted programs already present on systems, helping their activity blend in with normal operations.
The framework has been seen in campaigns named SHADOW-VOID-044 and SHADOW-EARTH-045. These attacks have targeted online gambling platforms, government organizations in Asia, and private companies. They use advanced backdoors like HOLODONUT and MKDOOR to keep long-term access to infected systems.
Designed to Work in Many Environments
PeckBirdy can run in many places — web browsers, Windows scripting tools (MSHTA, WScript), Classic ASP servers, and modern platforms like Node.js and .NET. This allows attackers to use it at different stages of an attack, from the first compromise to deeper network access and persistence.
The malware is written in JScript so it can run on both old and new systems. When it starts, it checks where it is running and changes its behavior based on the environment.
For communication, PeckBirdy mainly uses WebSockets but can switch to other methods that look like normal web traffic. All communication is protected using AES encryption and Base64 encoding, with the key linked to a built-in 32-character ATTACK_ID. This helps attackers keep their control channels hidden and secure.
Coordinated Attack Campaigns
PeckBirdy was used in two organized cyberattack campaigns.
SHADOW-VOID-044 (seen in 2023) targeted Chinese gambling websites. Attackers injected harmful scripts into websites and redirected visitors to fake Google Chrome update pages. Instead of an update, users received malware. The infrastructure used in this campaign has links to a threat group known for attacking the gambling industry.
SHADOW-EARTH-045 (observed in 2024) focused on Asian government bodies and private organizations. Attackers created fake login pages to steal credentials. They also used a Chrome security flaw (CVE-2020-16040) and social engineering to trick users into running malware. In one case in the Philippines, attackers used MSHTA commands and compromised GitHub pages to run PeckBirdy on a web server.
Malware Used
Two main backdoors were involved:
HOLODONUT
A .NET-based backdoor that runs in memory to avoid detection. It can load extra tools when attackers need them and uses techniques to bypass security monitoring.
MKDOOR
A two-part backdoor system. One part installs the malware, and the other controls it remotely. It tries to avoid security tools and makes its network traffic look like normal Microsoft communication.
Infrastructure Findings
Researchers found other malware on related servers and saw the use of stolen digital certificates to make malicious files look legitimate. Some servers overlapped with infrastructure used by other advanced threat groups, though not all links are fully confirmed.
Key Vulnerability Used
CVE-2020-16040
A high-severity Chrome vulnerability that was actively exploited in these attacks.
These campaigns show how attackers combine website compromise, fake updates, credential theft, and stealthy backdoors to keep long-term access to targeted systems.
Mitigations
- Use security platforms that can detect PeckBirdy-related activity and provide threat intelligence for hunting
- Watch for suspicious JScript activity launched through built-in system tools (LOLBins)
- Apply application allowlisting so only approved programs can run
- Check for unsigned or unusually signed executables
- Monitor network traffic for encrypted connections to unknown or unusual domains
- Use behavior-based and memory monitoring tools, since file-based detection may miss this threat
PeckBirdy shows that modern attackers use trusted tools and cross-platform methods to avoid traditional defenses, so visibility into behavior and memory activity is essential.













Leave A Comment