PromptSpy is a newly discovered Android malware family that uses Google’s Gemini AI model to make real-time decisions on infected devices.
Instead of using fixed screen coordinates or simple automation rules, PromptSpy sends Gemini a natural-language request along with an XML snapshot of the current screen. This snapshot includes details about visible elements such as text, type, and screen position.
Gemini analyzes the screen content and responds with JSON instructions telling the malware what action to perform — such as tap, long-press, or swipe — and exactly where to do it.
The main goal is persistence. PromptSpy uses this AI-driven method to keep its malicious app pinned in the Recent Apps list, even when the user tries to close it.
The malware runs in a loop. It executes Gemini’s instructions using Android’s Accessibility Service, captures the updated screen, and sends it back to Gemini. This continues until the AI confirms the app is successfully pinned. Because it relies on AI analysis instead of hardcoded rules, it works across different devices, Android versions, and manufacturer customizations.
Security researchers at ESET describe PromptSpy as the first known Android malware to directly integrate generative AI into its execution flow. The focus is stealthy persistence and maintaining control over the device.
Android AI Malware Capabilities
Beyond AI-based persistence, PromptSpy also acts as a powerful remote access tool.
It includes a built-in VNC component that allows attackers to control the infected phone in real time. Once the victim grants Accessibility permissions, attackers can:
- View the device screen live
- Simulate taps and gestures
- Perform actions as if physically holding the phone
The malware can capture lockscreen credentials, gather device information, take screenshots, record screen activity as video, and monitor which app is currently in use.
It communicates with a hardcoded command-and-control server using the VNC protocol, protected by AES encryption. The server can also send a Gemini API key and additional task instructions to the malware.
PromptSpy also actively blocks removal attempts. It abuses Accessibility permissions to place invisible overlays on important system buttons, including those used to uninstall the app or disable its privileges.
These transparent overlays intercept user taps on “Uninstall” or “Stop,” preventing normal removal.
Technical analysis shows that PromptSpy is delivered through a dropper app. The malicious payload (app-release.apk) is embedded inside the dropper’s assets directory.
Campaign Spread and Target Regions
ESET connects PromptSpy to a multi-stage, financially driven campaign mainly targeting users in Argentina.
An earlier variant, VNCSpy, was uploaded from Hong Kong in January 2026. More advanced PromptSpy samples appeared from Argentina in February 2026.
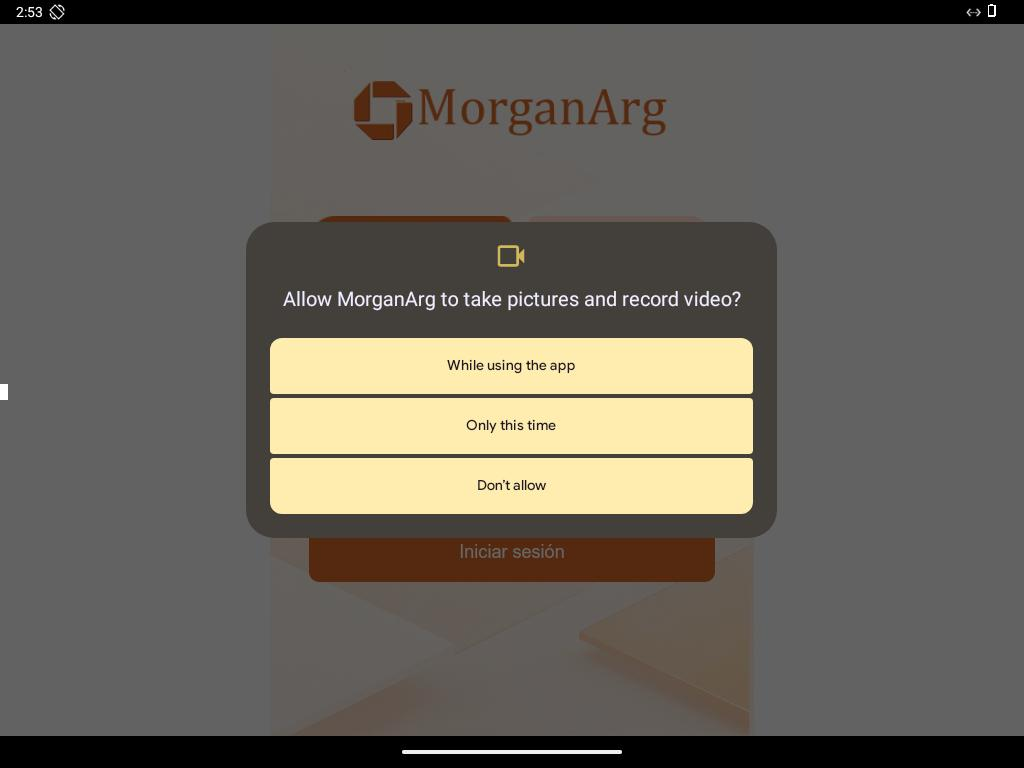
The malware spread through domains such as mgardownload[.]com and m-mgarg[.]com, which imitated JPMorgan Chase branding under the name “MorganArg” using Spanish banking lures.
Analysis of the same infrastructure revealed another Android phishing trojan signed with the same certificate and using the same fake banking site, likely acting as the initial infection stage before deploying PromptSpy.
Although PromptSpy has not appeared widely in ESET telemetry and may still be in limited testing, the active domains confirm some real-world use.
Code findings, including simplified Chinese debug strings and references to Chinese Accessibility events, suggest development in a Chinese-speaking environment, even though current targets are in Latin America.
PromptSpy is not available on Google Play, and Google Play Protect now detects known variants.
This campaign follows ESET’s 2025 discovery of PromptLock, an AI-powered ransomware prototype, highlighting the growing use of generative AI in malware operations.
IOCs
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| 6BBC9AB132BA066F63676E05DA13D108598BC29B | net.ustexas.myavlive.apk | Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| 375D7423E63C8F5F2CC814E8CFE697BA25168AFA | nlll4.un7o6.q38l5.apk | Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| 3978AC5CD14E357320E127D6C87F10CB70A1DCC2 | ppyzz.dpk0p.ln441.apk | Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| E60D12017D2DA579DF87368F5596A0244621AE86 | mgappc-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 9B1723284E311794987997CB7E8814EB6014713F | mgappm-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 076801BD9C6EB78FC0331A4C7A22C73199CC3824 | mgappn-0.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 8364730E9BB2CF3A4B016DE1B34F38341C0EE2FA | mgappn-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| F8F4C5BC498BCCE907DC975DD88BE8D594629909 | app-release.apk | Android/Spy.PromptSpy.A | Android PromptSpy. |
| C14E9B062ED28115EDE096788F62B47A6ED841AC | mgapp.apk | Android/Phishing.Agent.M | Android phishing malware. |
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!













Leave A Comment