VMware servers are targeted again by the North Korean Hackers called Lazarus. The CVE-2021-44228 is exploited again to bring impact to a variety of products including the VMware Horizon Servers.
VULNERABILITY
The CVE-2021-44228 is an unauthenticated Remote Code Execution vulnerability to inject backdoors that fetch information-stealing payloads on the VMware.
At First, Log4j vulnerability is exploited through VMware Horizon’s Apache Tomcat service to execute a PowerShell command. This PowerShell command will trigger installing the NukeSped backdoor on the server.
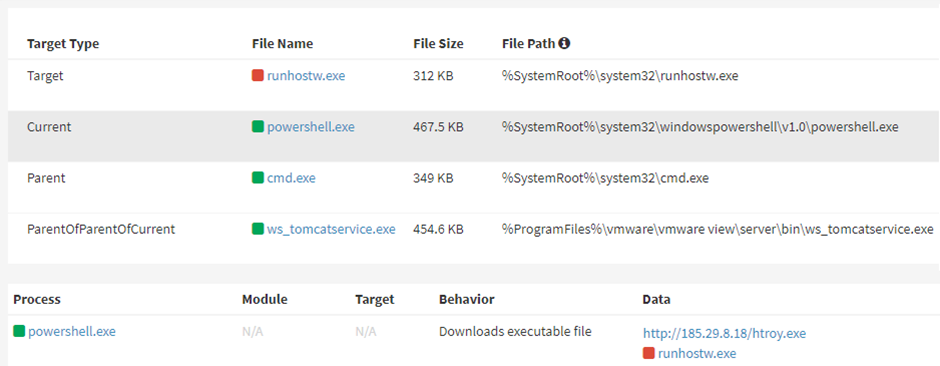
NUKESPED
The NukeSped/NukeSpeed is a backdoor malware, with in-memory execution and remote download. This performs various espionage operations in the compromised environment. Espionage operations involve taking screenshots, recording key presses, accessing files, and more.
From the latest variant collected and analyzed, there are two new modules – one for dumping USB contents and the other for accessing web camera devices.
This backdoor malware is used by Lazarus to install an additional console-based information-stealer malware that collects information stored on web browsers.
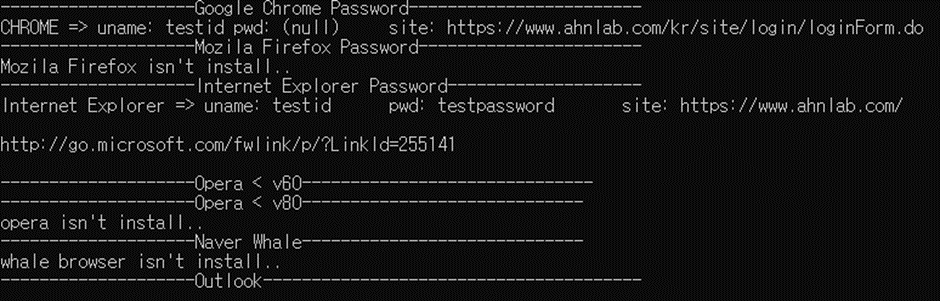
According to ASEC’s Study, the data given below can be stolen by the info-stealer,
- Credentials, Browsing history from web browsers,
- E-mail account details and information, &
- The recent file names of the Microsoft Office Tools (.xxs,.ppt,.docx – formats) and Hancom 2010.
JIN MINER
Apart from NukeSped, Lazarus was observed to be deploying Jin Miner to access Log4Shell. Jin Miner is a Crypto Miner which is probably used in less critical moments by the threat actors.
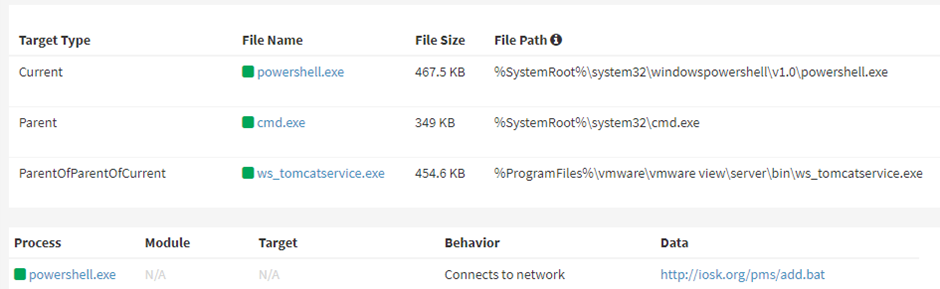
From the beginning of this year-2022, Lazarus was found exploiting the Living-Of-the-Land Binaries (LOLBins) in Campaigns targeting Windows and compromise Windows and macOS devices by downloading and running malicious cryptocurrency apps.
INDICATORS OF COMPROMISE
NukeSped – MD5
1875f6a68f70bee316c8a6eda9ebf8de (Backdoor/Win.NukeSped.R486595) (2022.04.20.03)
NukeSped – Download URL
hxxp://185.29.8[.]18/htroy.exe
InfoStealer – MD5
47791bf9e017e3001ddc68a7351ca2d6 (Backdoor/Win.NukeSped.C4631988) (2021.09.15.01)
Jin Miner (MD5, alias, and engine version)
7a19c59c4373cadb4556f7e30ddd91ac (CoinMiner/BAT.Generic) (2022.05.11.03)
c2412d00eb3b4bccae0d98e9be4d92bb (CoinMiner/BAT.Generic) (2022.05.11.03)
8c8a38f5af62986a45f2ab4f44a0b983 (Win-Trojan/Miner3.Exp) (2020.01.29.00)
7ef97450e84211f9f35d45e1e6ae1481 (Win-Trojan/Miner3.Exp) (2020.01.29.00)
dd4b8a2dc73a29bc7a598148eb8606bb (Unwanted/Win32.NSSM.R353938) (2020.10.27.00)
Jin Miner Download URL
hxxp://iosk[.]org/pms/add.bat
hxxp://iosk[.]org/pms/mad.bat
hxxp://iosk[.]org/pms/jin.zip
hxxp://iosk[.]org/pms/jin-6.zip













Leave A Comment