Malware researchers have noticed a new tool that helps cybercriminals build malicious. LNK files to deliver payloads for the initial stages of an attack.
Some of the prevalent malware families using .lnk files for their payload delivery of late are:
- Emotet
- Bumblebee
- Qbot
- Icedid
Quantum offers UAC bypass, Windows Smartscreen bypass, the ability to load multiple payloads on a single LNK file, post-execution hiding, startup or delayed execution.The .

lnk builder embeds the generated .hta payload and creates a new .lnk file. The builder provides various icons as an option while building the .lnk file. The below figure shows the Quantum .lnk builder.
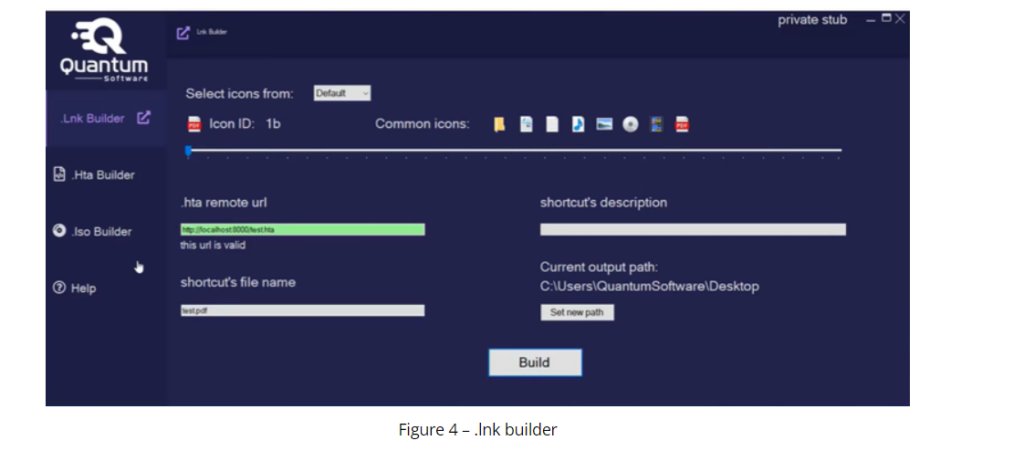
The file used in the campaign is “Password.txt.lnk”,which appears as a text file with a password for a protected PDF document.
The powershell script that executes upon opening the LNK file is very similar to scripts used by Lazarus in recent campaigns .
Tools like Quantum are accelerating the adoption trend even more and make the choice of LNK files more enticing to cybercriminals.
Users are advised to remain vigilant and scan all files they receive via email on an anti-virus tool before executing them
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566 | Phishing |
| Execution | T1204 T1059 | User Execution Command and Scripting Interpreter |
| Defense Evasion | T1218 T1140 | System Binary Proxy Execution Deobfuscate/Decode Files or Information |
Indicators Of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 04e8a5c6e5797b0f436ca36452170a2f 924be824edb54f917d52e43a551c0eb2848cad8f 2f6c1def83936139425edfd611a5a1fbaa78dfd3997efec039f9fd3338360d25 | MD5 SHA-1 SHA-256 | .lnk file |
| hxxps[:]//quantum-software[.]online/remote/bdg[.]hta | Domain | Malicious Domain |
| 52b0b06ab4cf6c6b1a13d8eec2705e3b dfdde88da020e584038d2656d0e3d48cfae27b1a b9899082824f1273e53cbf1d455f3608489388672d20b407338ffeecefc248f1 | MD5 SHA-1 SHA-256 | Laz |
Recommendations
Following recommendations are observed:
- Refrain from opening untrusted links and email attachments without verifying their authenticity.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Verify the source of files before executing them.
- Turn on the automatic software update .
Follow us for more, Facebook, Twitter, LinkedIn and Instagram













Leave A Comment