Recently security experts from Sucuri, spotted JavaScript injections targeting WordPress sites to display fake DDoS Protection pages which lead victims to download remote access trojan malware.
WordPress, DDoS, malware
Hacked WordPress sites show fake DDoS-protection information. Site visitors see a pop-up that masquerades as a Cloudflare DDoS-protection service.
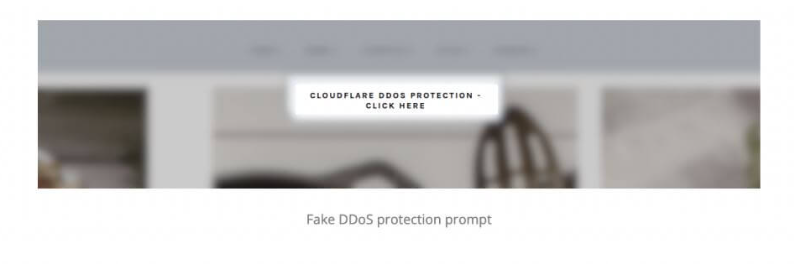
The page above requests that the visitor clicks on a button to bypass the DDoS protection and visit the site. However, upon clicking on the button, the ‘security_install.iso’ file is downloaded to the visitor’s machine.
The file poses as a tool required to bypass the DDoS verification. In order to trick the visitors into opening the file, a new message tells them that the verification code to access the website is contained in the file.
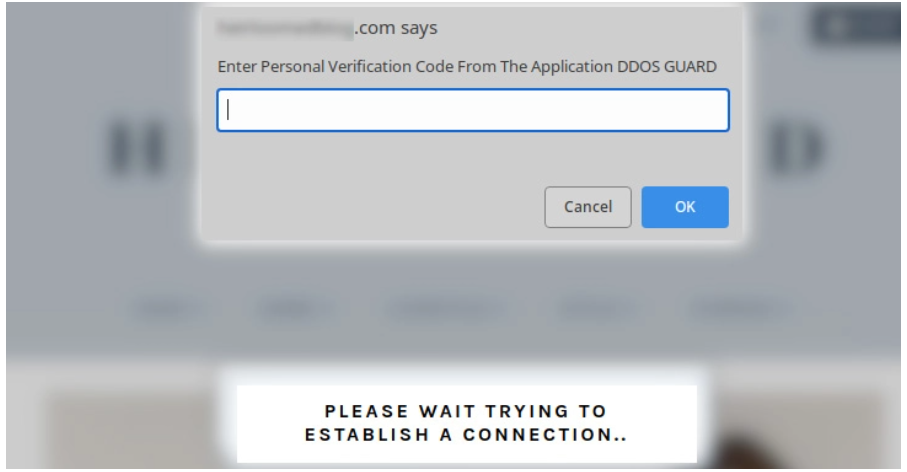
Upon opening the file, the image file is mounted and its content is shown to the visitors. The mounted drive contains a file called security_install.exe, which is actually a Windows shortcut that runs a PowerShell command contained in the debug.txt file in the same drive.
The same malicious program can also install RacoonStealer, a program that sounds more likely to steal your lunch than your files, but that is capable of pinching passwords and user credentials from infected devices.
Website owners are recommended to:
- Keep all software on your website up to date
- Use strong passwords
- Use 2FA on your administrative panel
- Place your website behind a firewall service
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment