A cyberattack campaign, potentially bent on cyber espionage, is highlighting the increasingly sophisticated nature of cyberthreats targeting defense contractors in the US and elsewhere.
The covert campaign, which researchers at Securonix detected and are tracking as STEEP#MAVERICK, has hit multiple weapons contractors in Europe in recent months, including potentially a supplier to the US F-35 Lightning II fighter aircraft program
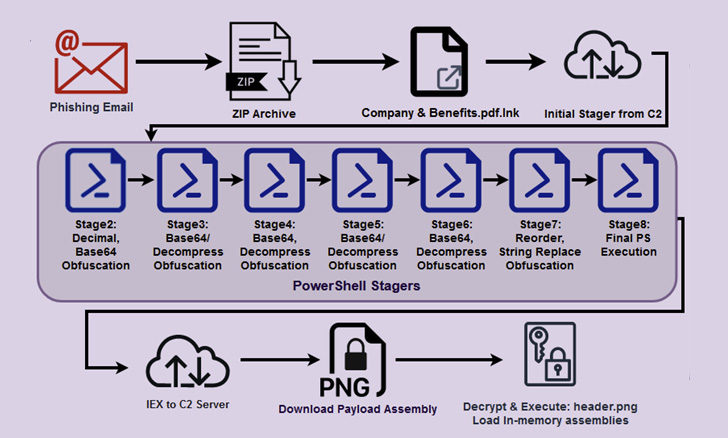
The STEEP#MAVERICK campaign appears to have launched in late summer with attacks on two high-profile defense contractors in Europe. Like many campaigns, the attack chain began with a spear-phishing email that contained a compressed (.zip) fie with a shortcut (.lnk) file to a PDF document purportedly describing company benefits. Securonix described the phishing email as being similar to one it had encountered in a campaign earlier this year .
When the .lnk file is executed, it triggers what Securonix described as a “rather large and robust chain of stagers,” each written in PowerShell and featuring as many as eight obfuscation layers. The malware also features extensive anti-forensic and counter-debugging capabilities which include monitoring a long list of processes that could be uses to look for malicious behavior.
The malware is designed to disable logging and bypass Windows Defender. It uses several techniques to persist on a system, including by embedding itself in the system registry, by embedding itself as a scheduled task and by creating a startup shortcut on the system.
Need to all these checks move, the PowerShell stager proceeds to disable logging, insert Windows Defender exclusions for LNK, RAR, and EXE files, and establish persistence via a scheduled process or Windows Registry modifications.
IOCS
Domains:
- terma[.]dev
- terma[.]icu
- terma[.]app
- terma[.]vip
- terma[.]wiki
- terma[.]pics
- terma[.]lol
- terma[.]ink
- onrender[.]com
- cobham-satcom.onrender[.]com
IP Addresses:
- 199.53.243
- 227.139.39
File Hashes:
- s
Da0888f06b2e690a3a4f52f3b04131f7a181c12c3cb8e6861fc67ff062beef37 - w
Da0888f06b2e690a3a4f52f3b04131f7a181c12c3cb8e6861fc67ff062beef37 - png
691c0a362337f37cf6d92b7a80d7c6407c433f1b476406236e565c6ade1c5e87













Leave A Comment