eSentire’s Threat Response Unit (TRU) has uncovered a sophisticated campaign in which threat actors exploit the ScreenConnect remote access client to deliver the AsyncRAT trojan, revealing the evolving tactics of cybercriminals and emphasizing the critical need for robust cybersecurity measures.
In June 2024, eSentire’s TRU identified multiple cases where users inadvertently downloaded the ScreenConnect remote access client from deceptive websites.
ScreenConnect, initially a legitimate tool, was exploited by threat actors to gain unauthorized access to users’ systems.
The main method of infection observed was through drive-by downloads, redirecting visitors of compromised websites to automatically download ScreenConnect.
A notable incident involved a user downloading ScreenConnect from the compromised WordPress site aviranpreschool[.]com, which had been redirected from lomklauekabjikaiwoge[.]com.
Once ScreenConnect was launched, it connected to the threat actor’s instance at fa-histsedueg.screenconnect[.]com, establishing a remote session. Through this connection, the attacker deployed an executable file that introduced the AsyncRAT, a remote access trojan, into the system.
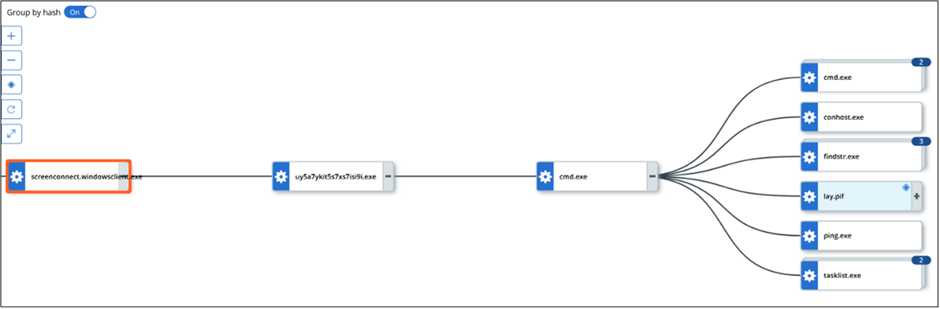
All about the Infection chain
The infection chain commenced with the download of an executable file named uy5a7ykit5s7xs7isi9i.exe (MD5: 6bdba391a77bb67cb5aaae203d061ea8), which housed an NSIS installer featuring an NSI script, embedded AutoIt components, and batch scripts.
The NSI script initiated a batch file named “Industries.cmd” (MD5: 3f8ca557d51e210952bdd7180cb33d10), which orchestrated various tasks to create and manage a malicious AutoIt script.
This batch file consolidated multiple files into a binary named “B” (MD5: 4f3bb0cdfff1c15b75041d07c1b7aac9), embedding the AsyncRAT payload.
It also merged additional files into a single entity named “Lay.pif” (MD5: b06e67f9767e5023892d9698703ad098) and executed the malicious AutoIt script using the reconstructed AutoIt executable.
The script incorporated delays to evade detection by antivirus programs and verified specific processes for successful execution.
The malicious AutoIt script decrypted the AsyncRAT payload using RC4 encryption and injected it into processes like RegAsm.exe or AppLaunch.exe, bypassing security measures to maintain persistence. AsyncRAT granted attackers control over compromised systems, enabling data theft, manipulation, and further malware deployment.
eSentire’s SOC responded swiftly, isolating affected hosts and providing remediation advice, highlighting the importance of vigilant cybersecurity practices.
Recommendations from eSentire’s Threat Response Unit (TRU):
Implementing Endpoint Detection and Response (EDR) solutions ensures real-time threat detection and response across all devices.
Introducing Phishing and Security Awareness Training (PSAT) programs educates employees on emerging threats and safe online practices.
Adopting password managers and implementing master passwords improves security over browser-based storage.
These incidents underscore the need for organizations to adopt robust cybersecurity strategies to defend against evolving threats.
Following these recommendations enhances overall security posture and reduces the likelihood of future attacks.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment