The FLUX#CONSOLE campaign exploits .MSC files to deploy backdoor malware, highlighting advanced phishing and Windows feature abuse.
The FLUX#CONSOLE campaign is a multi-stage attack aimed at delivering backdoor malware.
It uses MSC files to evade antivirus systems and deploy hidden payloads.
This campaign marks a shift from abusing LNK files, long used in phishing attacks. Key tactics include:
- Tax-Themed Phishing Lures: Emails trick users with harmless-looking tax documents.
- Advanced Obfuscation: Layers of concealment, from JavaScript to hidden DLLs, bypass detection.
- DLL Sideloading: Malicious code runs using legitimate tools like Dism.exe.
- Persistence: Scheduled tasks keep the malware active after reboots.
These methods show the effort cybercriminals put into evading detection and maintaining access.
Attack Process
Step 1: Phishing Lure
The attack starts with a phishing email containing a malicious attachment or link disguised as a legitimate file, like a tax document.
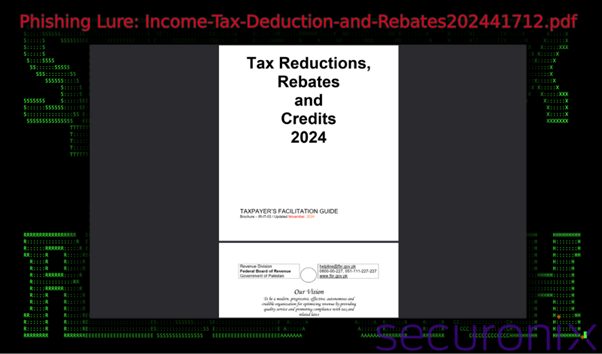
For example, filenames like “Income-Tax-Deduction-and-Rebates202441712.pdf” are used. The .MSC file looks like a PDF, exploiting hidden file extensions in Windows to deceive users.
Step 2: MSC File Execution
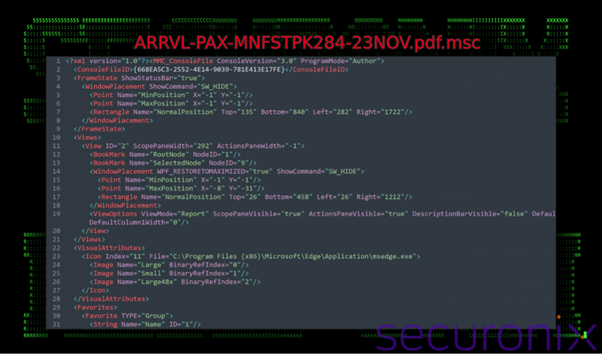
.MSC files, typically used for Windows admin settings, are misused in this attack to run malicious scripts.
When the user opens the .MSC file, it executes harmful JavaScript or VBScript through the mmc.exe process. The file hides its actions by minimizing windows and using obfuscation.
Step 3: Payload Delivery
The .MSC file serves as a loader and dropper, delivering the payload in two ways:
- Directly embedded in the .MSC file.
- Downloaded from a remote server.
It drops a malicious DLL, DismCore.dll, which is sideloaded through the legitimate Dism.exe process.
Step 4: Persistence
The malware sets up scheduled tasks, like “CoreEdgeUpdateServicesTelemetryFallBack,” to run Dism.exe every five minutes, keeping it active.
Microsoft Management Console (.MSC) files are trusted by users, allowing attackers to exploit this trust. When opened:
- The legitimate mmc.exe process is triggered.
- Malicious code runs covertly as an admin tool.
.MSC files can also host scripts like JavaScript or VBScript, making them effective for delivering malicious payloads.
Obfuscation Techniques
The FLUX#CONSOLE campaign uses advanced obfuscation methods:
- JavaScript Layers: The script hides malware commands, requiring multiple decryption steps.
- Base64 & Hex Encoding: Payloads are encoded to evade detection.
- DLL Obfuscation: The DismCore.dll payload includes junk code to confuse analysts.
These tactics hinder detection by traditional security tools.
Once inside, the backdoor:
- Connects to a remote Command-and-Control (C2) server, sending encrypted data.
- Can steal sensitive information.
- Enables lateral movement for further network compromise.
Despite the attack being disrupted within 24 hours, it highlights weaknesses in modern endpoint defenses.
The FLUX#CONSOLE campaign shows the need for stronger security solutions and proactive threat intelligence to counter advanced attacks.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment