Cybercriminals created PhishWP, a malicious WordPress plugin, to mimic payment gateways like Stripe for phishing attacks on compromised sites.
PhishWP integrates with Telegram to steal real-time data, including credit card details and personal info. This helps attackers bypass security and execute fraudulent transactions.
PhishWP is a malicious WordPress plugin that steals user information during online transactions. It mimics real payment gateways to collect card details and 3DS codes. Integrated with Telegram, it sends stolen data to attackers.
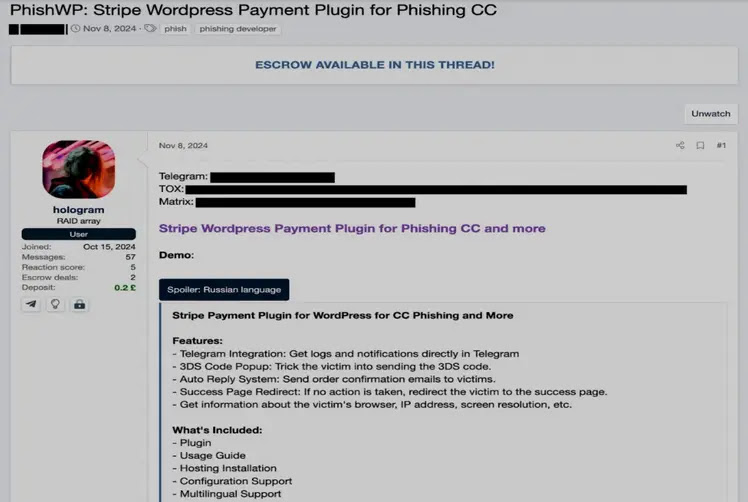
The plugin also profiles users and sends fake confirmation emails to trick victims. Its multi-language support and obfuscation options make it harder to detect and allow for widespread phishing attacks.
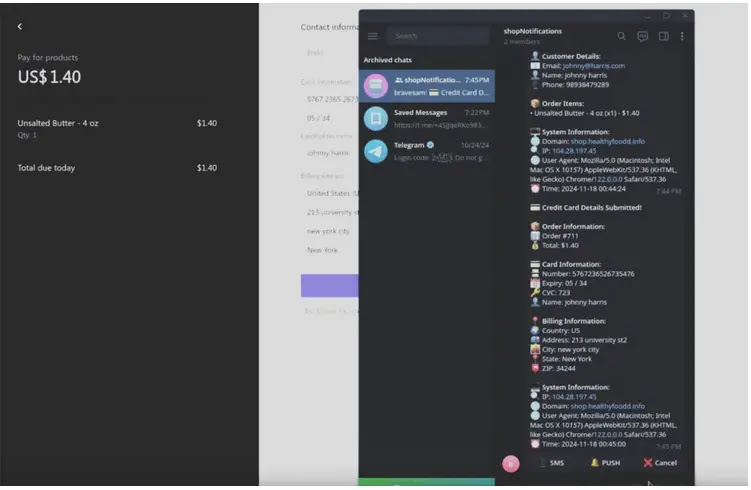
According to SlashNext, an attacker uses PhishWP to set up a fake e-commerce site with discounted products that mimics Stripe payment pages, including 3DS authentication pop-ups.
When users unknowingly enter their payment and personal details, the plugin secretly sends this information, including one-time passwords, to the attacker’s Telegram account.
This allows the attacker to quickly carry out unauthorized transactions or sell the stolen data on the dark web, causing financial and reputational damage. Attackers can compromise WordPress sites by hacking existing ones or creating fake replicas.
PhishWP creates fake payment gateways, like Stripe, to trick victims into entering sensitive information. Targeted phishing campaigns lead users to these deceptive sites, where the plugin captures credit card details and security codes.
The stolen data is sent to the attacker via Telegram. Victims receive fake confirmation emails, while attackers exploit or sell the data on the dark web.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment