Researchers discovered a misconfiguration in on-premise applications that bypasses Active Directory Group Policy meant to disable NTLMv1, effectively rendering it ineffective, according to Silverfort’s Dor Segal.
NTLM, still widely used in Windows networks for user authentication, was deprecated in mid-2024 but remains in use for backward compatibility.
Microsoft officially removed NTLMv1 in Windows 11 (version 24H2) and Windows Server 2025. Although NTLMv2 includes mitigations to reduce relay attacks, it remains vulnerable to exploits allowing attackers to access sensitive data.
These attacks often involve tricking victims into authenticating to malicious endpoints or relaying their credentials to compromise a target.
Microsoft’s Group Policy mechanism is designed to disable NTLMv1 across networks. According to researcher Dor Segal, the LMCompatibilityLevel registry key ensures Domain Controllers reject messages, returning a “wrong password” error (0xC000006A) during authentication attempts.
Silverfort found that NTLMv1 authentication can bypass Group Policy by exploiting a Netlogon Remote Protocol (MS-NRPC) setting.
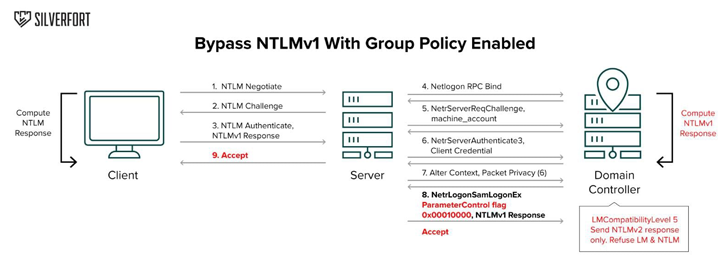
The NETLOGON_LOGON_IDENTITY_INFO structure contains a ParameterControl field, which can be configured to “allow NTLMv1 authentication” even when NTLMv2 is enforced.
“This demonstrates that on-prem applications can override Active Directory’s Group Policy for LAN Manager authentication,” said researcher Dor Segal.
“Organizations may believe they are protected by setting this group policy, but misconfigured applications can still bypass it,” warned Segal.
To reduce NTLMv1 risks, enable audit logs for all NTLM authentications and monitor for applications requesting NTLMv1. Keeping systems updated is also crucial.
Meanwhile, HN Security’s Alessandro Iandoli revealed that certain Windows 11 versions (pre-24H2) have security features that attackers can bypass to execute arbitrary kernel-level code.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment