A highly sophisticated Linux rootkit, Pumakit, has been identified targeting critical infrastructure sectors like telecommunications, finance, and national security.
Discovered by Elastic Security Labs, Pumakit highlights a growing trend of advanced malware targeting Linux environments, which have typically been regarded as more secure than other operating systems.
All about Pumakit
Pumakit uses advanced evasion techniques at the kernel level, posing a serious threat to organizations using Linux systems. Its ability to remain undetected highlights the growing complexity of cyber threats.
It targets kernel-level processes to carry out malicious actions while staying hidden. It uses advanced methods to avoid detection and keep control of compromised systems.
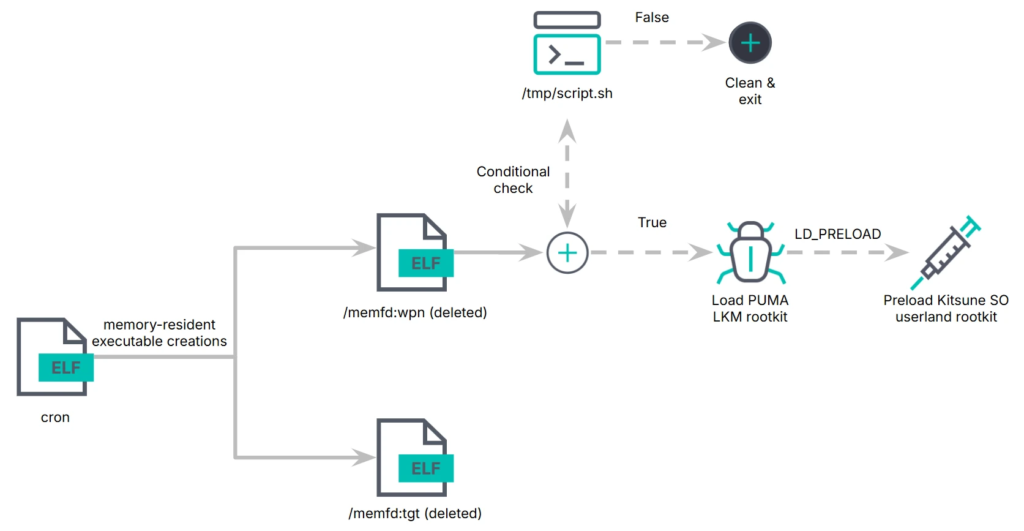
Pumakit hides its activities by manipulating kernel-level system calls, making it invisible to traditional monitoring tools.
It embeds itself in the kernel, ensuring control even after reboots, and erases logs to hide its actions. The rootkit allows attackers to steal data, maintain a backdoor, and disable security tools, making detection difficult. Organizations should monitor for signs of Pumakit infection.
Key indicators of Pumakit include unusual kernel-level modules, changes to system call handlers, and hidden files or processes. Suspicious traffic to IP 89.23.113.204 or domains like rhel.opsecurity1.art, as well as malicious file hashes (e.g., 4375998ea157a8a21e1ead13052bad8a), should raise alarms.
To mitigate Pumakit, organizations should implement strategies like blocking malicious libraries to prevent dynamic linker hijacking (T1574.006), detecting process injection (T1055), enforcing multi-factor authentication (MFA) to protect accounts (T1078.001), and restricting permissions to secure security settings against tampering (T1562.001).
Recommended Defensive Measures
System Hardening: Apply security patches and updates regularly.
Access Management: Limit admin access and enforce strict account policies.
Behavioral Monitoring: Use continuous monitoring tools to detect anomalies.
Incident Response: Have protocols in place for quick rootkit response.
Elastic Security Labs offers a YARA Rule to detect Pumakit infections by scanning for malicious strings, file artifacts, and IP addresses like “PUMA %s,” “opsecurity1.art,” and 89.23.113.204.
Pumakit highlights the risks of advanced cyber threats. Continuous monitoring and proactive strategies are vital to counter such threats.
Indicators of Compromise (IoC)
| Indicator Type | Details |
| Kernel-level modules | Modules with unusual names or attributes |
| System modifications | Unexpected changes to system call handlers |
| Hidden assets | Concealed files, processes, or network connections |
| Suspicious hosts | 89.23.113.204 and domains like rhel.opsecurity1.art |
| File Hashes | Examples: 4375998ea157a8a21e1ead13052bad8a, 810f4b422b9c0a6718e9461de3a2edda |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment