Palo Alto Networks researchers have discovered a new Linux malware, “Auto-Color,” which poses a serious threat due to its advanced evasion methods and ability to give attackers full remote access to infected systems.
Found between November and December 2024, the malware targets Linux systems, mainly in universities and government offices in North America and Asia.
It uses advanced techniques to remain undetected, including disguising itself with harmless file names like “door” or “egg” and employing a malicious library, libcext.so.2, to mimic legitimate system files.
Installation and Root Privilege Exploitation
When executed, Auto-Color checks if its file name is “Auto-color.” If not, it renames itself and installs a hidden library implant. The installation requires the user to have root privileges.
Without root access, the malware is limited in its actions but still remains a threat in later stages. With root access, it installs the libcext.so.2 library in the system’s base directory and alters files like /etc/ld.preload for persistence. This change lets the malware load its library first, overriding key system functions.
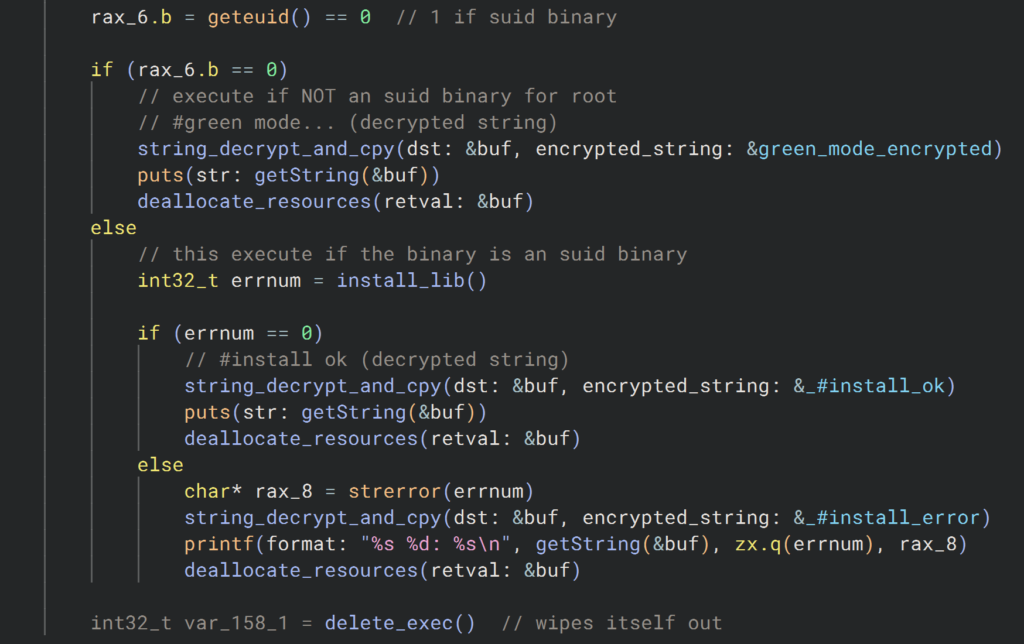
Auto-Color uses custom encryption to hide its configuration and C2 server communication, making it hard to detect. It encrypts payloads with a stream cipher and manipulates system files, like /proc/net/tcp, to conceal network activity.
The malware also hides C2 connections by removing traces of specific IPs or ports, making its operations difficult to track, similar to techniques used by Symbiote but more advanced.
Once installed, Auto-Color gives attackers full remote access, including:
- Establishing reverse shell connections
- Acting as a proxy for further attacks
- Manipulating files and running programs
- Sending and changing global configuration data
It communicates with C2 servers using a custom encrypted protocol. Commands trigger actions like gathering system data or uninstalling itself.
Indicators of compromise include files with names like “log,” “edu,” or “door,” each with the same size (229,160 bytes) but different hashes due to encrypted payloads. Suspicious changes to /etc/ld.preload or unusual network activity could also indicate infection.
Palo Alto Networks recommends using Cortex XDR and Advanced WildFire to detect and block Auto-Color. Organizations should monitor for IoCs and use strong endpoint protection. In case of infection, consult incident response teams like Unit 42 for remediation.
This highlights the need for proactive threat detection and response against increasingly advanced Linux malware.
Indicators of Compromise
Malicious files from Auto-Color:
SHA256 hash: 270fc72074c697ba5921f7b61a6128b968ca6ccbf8906645e796cfc3072d4c43
- File size: 229,160 bytes
- File name: log
- File type: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked
- File description: Sample 1 malware from Auto-color
SHA256 hash: 65a84f6a9b4ccddcdae812ab8783938e3f4c12cfba670131b1a80395710c6fb4
- File size: 229,160 bytes
- File name: edus
- File type: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked
- File description: Sample 2 malware from Auto-color
SHA256 hash: 83d50fcf97b0c1ec3de25b11684ca8db6f159c212f7ff50c92083ec5fbd3a633
- File size: 229,160 bytes
- File name: egg
- File type: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked
- File description: Sample 3 malware from Auto-color
SHA256 hash: a1b09720edcab4d396a53ec568fe6f4ab2851ad00c954255bf1a0c04a9d53d0a
- File size: 229,160 bytes
- File name: edu
- File type: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked
- File description: Sample 4 malware from Auto-color
SHA256 hash: bace40f886aac1bab03bf26f2f463ac418616bacc956ed97045b7c3072f02d6b
- File size: 229,160 bytes
- File name: door
- File type: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked
- File description: Sample 5 malware from Auto-color
SHA256 hash: e1c86a578e8d0b272e2df2d6dd9033c842c7ab5b09cda72c588e0410dc3048f7
- File size: 229,160 bytes
- File name: exup
- File type: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked
- File description: Sample 6 malware from Auto-color
SHA256 hash: 85a77f08fd66aeabc887cb7d4eb8362259afa9c3699a70e3b81efac9042bb255
- File size: 229,160 bytes
- File name: law
- File type: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked
- File description: Sample 7 malware from Auto-color
SHA256 hash: bf503b5eb456f74187a17bb8c08bccc9b3d91a7f0f6fd50110540b051510d1ca
- File size: 35,160 bytes
- File name: libcext.so.2
- File type: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked
- File description: Library Implant from Auto-color
Malicious C2 IP Addresses from Auto-Color:
- 146[.]70[.]41[.]178:443 – log sample
- 216[.]245[.]184[.]214:443 – edus/egg sample
- 146[.]70[.]87[.]67:443 – edu/door sample
- 65[.]38[.]121[.]64:443 – exup sample
- 206[.]189[.]149[.]191:443 – law sample
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment